CoAP: The Next Protocol Vulnerable to DDoS Attacks
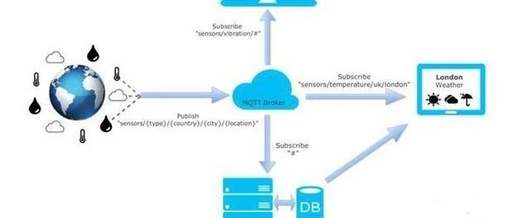
Click the blue text to follow us with one click “ Dream Thinker NetworkSecurity Guardian ” Security researchers indicate that RFC 7252, also known as the Constrained Application Protocol (CoAP), is about to become one of the most abused protocols in DDoS attacks. What is CoAP? CoAP was officially approved in 2014 and has only … Read more