

The Anti-Pyramid Scheme Network released on July 6:This article introduces the fundamental knowledge of the Internet of Things, what it is, and common IoT protocols.Why have participants in IoT investment projects been severely deceived in recent years? Where have the core members of those promotional IoT project investment platforms gone? Not going to discuss that here! Check the China Judgments Online!
01 What is the Internet of Things?
The concept of the Internet of Things (IoT) should be familiar to readers. The term was first proposed in 1999 and has been referred to as the third wave of world information industry development after computers and the internet. It has now developed for over 20 years.
Today, we can encounter many IoT products in our daily lives, such as various smart home appliances and smart locks, which are mature applications of IoT technology.
The earliest definition of the Internet of Things is: Connecting all items to the internet through information sensing devices such as RFID to achieve intelligent identification and management.Of course, as IoT has evolved, its definition and scope have expanded and changed. Below are the characteristics of modern IoT.
1. The Internet of Things is also the Internet
The Internet of Things, or the Internet of Things, is a part of the internet. The IoT uses the internet’s infrastructure as a carrier for information transmission. Modern IoT products must connect to the internet in some way, allowing ‘things’ to upload/download data and interact with people through the internet.
For example, remotely starting a car via a mobile app, when a user completes the start operation through the app, the command is sent from the internet-connected phone to the cloud platform, which finds the internet-connected car’s computer, sends the command, and the car’s computer executes the start command and sends the result back to the cloud platform; at the same time, this operation is recorded in the cloud, allowing the user to check the remote unlocking history anytime from the app.
This is a typical IoT scenario, which is a type of internet application. ‘Things’ connect to the internet, data and information interact through the internet, and like other internet applications, data is aggregated in the cloud.
2. The subject of the Internet of Things is ‘things’
While modern IoT applications are a type of internet application, there is a significant difference from traditional internet applications: in traditional internet applications, the main producers and consumers of data are people, while in modern IoT, the main producers and consumers of data are things.
In modern IoT applications, the producers of data are ‘things’, such as smart devices or sensors, and the consumers of data are often also ‘things’.
In smart agriculture, for example, a temperature sensor in an incubator periodically uploads the temperature to the control center. When the temperature falls below a certain threshold, the center remotely activates the heating device according to preset rules. In this scenario, the data producer is the temperature sensor, and the data consumer is the heating device; both are ‘things’, and humans are not directly involved.
The biggest difference between IoT and traditional internet is: the producers and consumers of data are primarily things, and the data content is closely related to ‘things’.
3. The Internet of Things and Artificial Intelligence
Artificial intelligence has been one of the hottest terms in the IT field in recent years. Looking at the development trajectory of AI, we can see that its rapid advancement is primarily due to two reasons.
-
Hardware development has significantly shortened the learning time of deep learning neural networks.
-
In the era of big data, the cost of obtaining large amounts of data has decreased.
In fact, the second reason is particularly important. Neural networks require vast amounts of data for learning, and the effective amount of data available for learning often determines the final performance of the trained neural network, even the importance of the algorithm can be ranked after the amount of data.
IoT devices, such as smart home appliances and wearable devices, generate massive amounts of data every day, and this data, after processing and cleaning, can serve as good training data for neural networks.At the same time, the neural networks trained can be reapplied to IoT devices, thus forming a positive feedback loop.
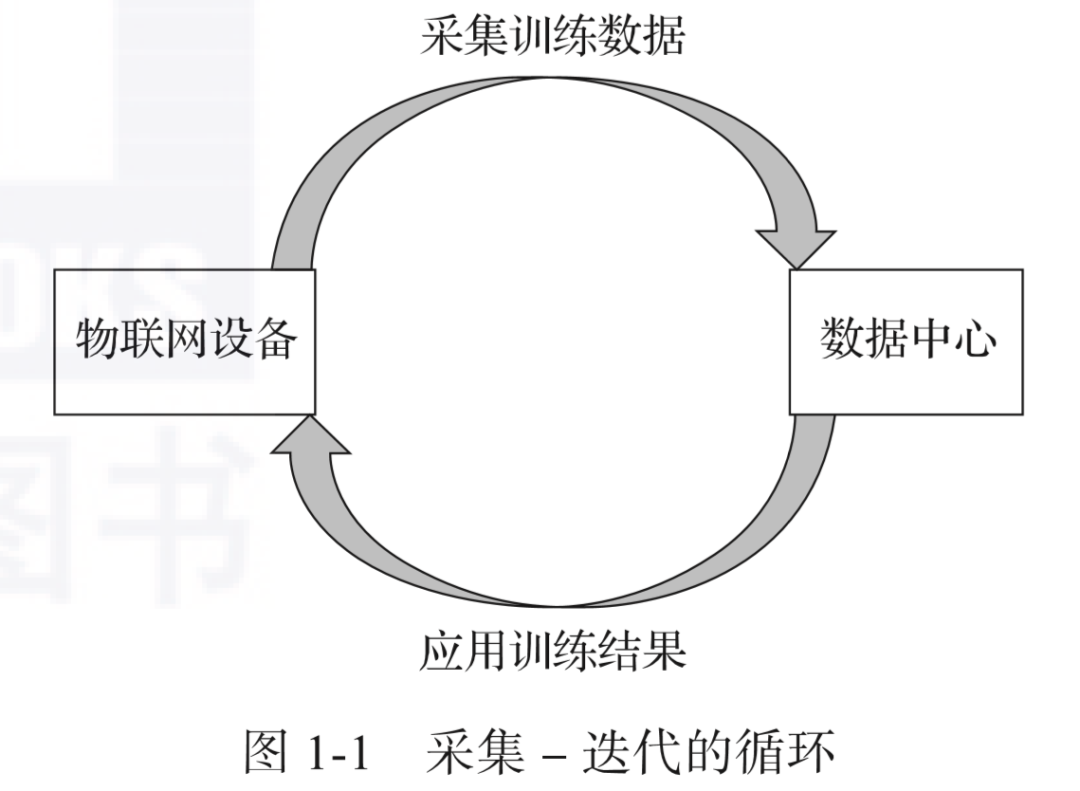
Figure 1-1 shows the iterative cycle of data collection and training using AI methods in the IoT application. Data is collected and trained through IoT devices; after training in the data center, the model is applied to IoT devices and evaluated for the next iteration.
The Internet of Things is an excellent application scenario for artificial intelligence. With the rapid development of AI, the theory and technology of IoT, proposed many years ago, will also welcome a new spring.
Currently, internet data entry is gradually converging toward several major giants (such as Alibaba and Tencent), making it increasingly costly for smaller companies to obtain data; the undeveloped data field of IoT is becoming particularly important.
Front-end devices will eventually tend to be similar, leading to homogeneous competition, and how to collect and effectively utilize the massive data generated by devices will be the decisive factor in whether you have a competitive advantage.
4. The Current Status and Prospects of the Internet of Things
With the arrival of the 5G era, the development of IoT will be very rapid. Additionally, new financing in the IoT sector has been on the rise. Let’s discuss the development prospects of the IoT industry from the perspective of application scenarios.
The application scenarios of IoT are very broad, including:
-
Smart Cities
-
Smart Buildings
-
Vehicle Networks
-
Smart Communities
-
Smart Homes
-
Smart Healthcare
-
Industrial IoT
In different scenarios, the differences in IoT applications are significant, and the heterogeneity of terminal and network architectures means that there are enough niche markets within the IoT industry, making it difficult for a single company to dominate market share. At the same time, due to the large market, it allows enough companies to survive. This situation is uncommon in the internet industry, where the head effect is very significant, and the vast majority of market share is often occupied by two or three leading companies.
The IoT model is relatively ‘heavier’ compared to the internet model. IoT applications always accompany front-end devices, which means that the switching costs for users are relatively high; after all, removing and reinstalling devices is much more complex than simply downloading an app.
This implies that the driving force of capital in the IoT industry is relatively weaker. If you gain a first-mover advantage, it will cost later entrants much more to catch up or push you out of the market compared to the internet industry.
Therefore, the IoT industry is still a blue ocean, and small companies can fully compete with large companies in this sector. After the hype around AI and blockchain cools down, IoT is likely to become the next hotspot. As programmers, it is essential to prepare some knowledge reserves before the windfall arrives.
02 Common IoT Protocols
1. MQTT Protocol
The MQTT protocol (Message Queue Telemetry Transport) was developed by IBM’s Andy Stanford-Clark and Arcom’s Arlen Nipper in 1999 for a project that connected oil pipelines through satellite networks. To meet the demands for low power consumption and low network bandwidth, the MQTT protocol was designed with the following features:
-
Simple implementation
-
Provides QoS for data transmission
-
Lightweight and low bandwidth usage
-
Can transmit any type of data
-
Persistent sessions
Over the years, the focus of the MQTT protocol has shifted from just embedded systems to the broader IoT world.
In simple terms, the MQTT protocol has the following characteristics:
-
Application layer protocol based on TCP
-
Uses a Client/Server architecture
-
Employs a publish/subscribe model, decoupling the sender and receiver of messages
-
Provides three levels of message QoS (Quality of Service): at most once, at least once, exactly once
-
Message sending and receiving are asynchronous, the sender does not need to wait for a response from the receiver
The architecture of the MQTT protocol consists of a Broker and multiple Clients connected to the Broker, as shown in Figure 2-1.
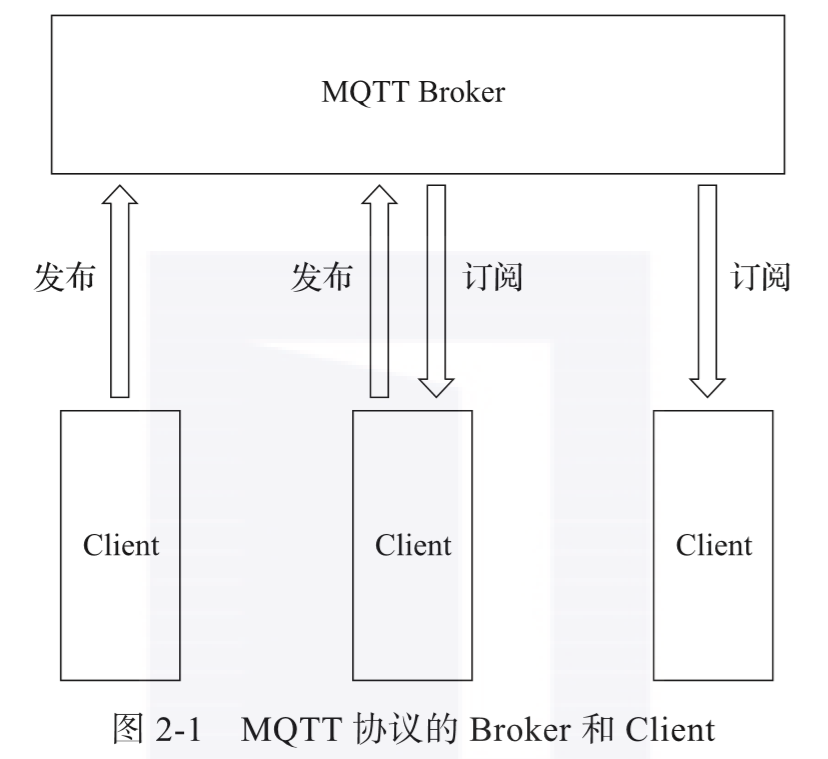
The MQTT protocol can provide communication assurance for a large number of low-power IoT devices in unreliable network environments. It also has significant applications in the mobile internet field, as many Android app push functions are based on the MQTT protocol, and some instant messaging implementations are also based on MQTT.
2. MQTT-SN Protocol
The MQTT-SN (MQTT for Sensor Network) protocol is the sensor version of the MQTT protocol. Although the MQTT protocol is a lightweight application layer protocol, it runs on top of the TCP protocol stack, which is not suitable for devices with very limited computing power and battery life, like sensors.
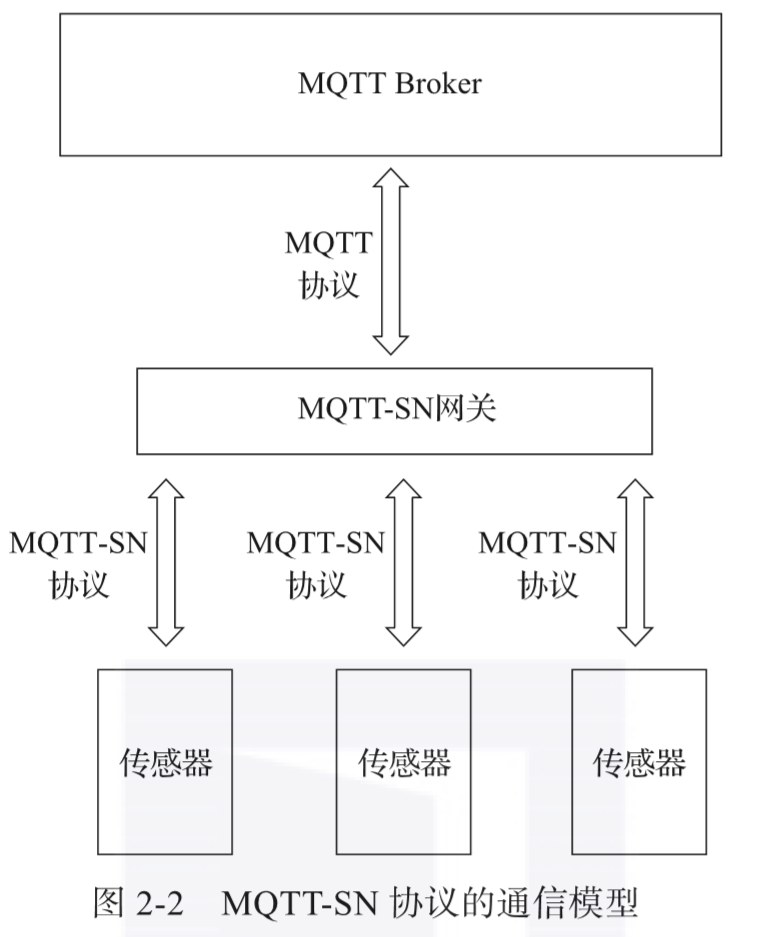
MQTT-SN runs on UDP while retaining most of the signaling and features of the MQTT protocol, such as subscription and publishing. The MQTT-SN protocol introduces the MQTT-SN gateway, which is responsible for converting the MQTT-SN protocol to MQTT and communicating with remote MQTT Brokers. The MQTT-SN protocol supports automatic discovery of gateways. The communication model of MQTT-SN is shown in Figure 2-2.
3. CoAP Protocol
The CoAP (Constrained Application Protocol) is a protocol that runs on resource-constrained devices. CoAP typically runs on UDP.
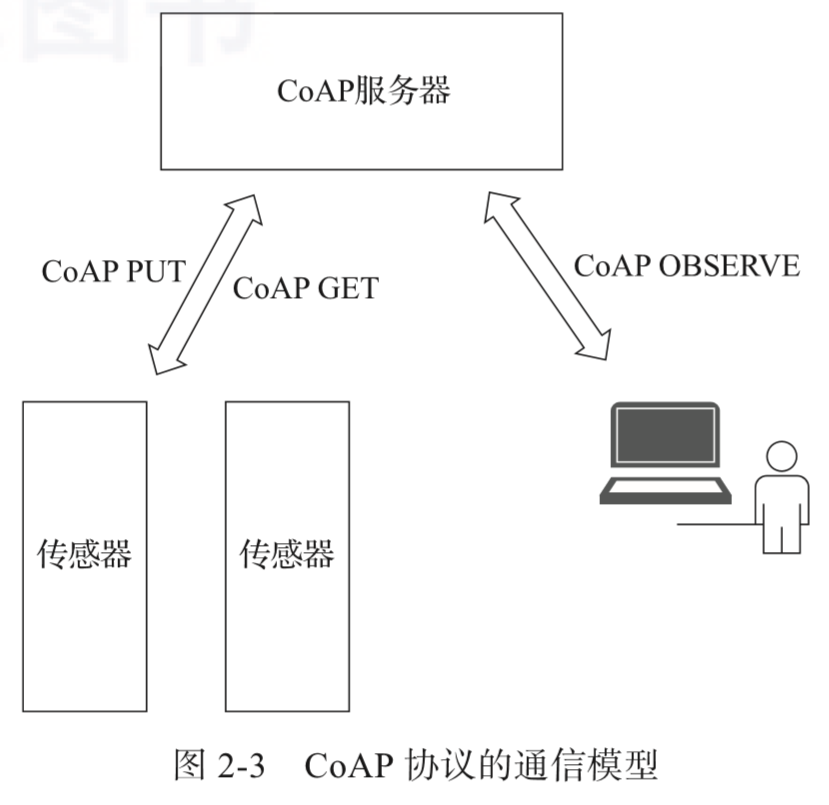
CoAP is designed to be very compact, with the smallest data packet being only 4 bytes. CoAP uses a Client/Server architecture and employs a request-response interaction pattern similar to HTTP. Devices can identify an entity using a URL like coap://192.168.1.150:5683/2ndfloor/temperature and use HTTP-like PUT, GET, POST, DELETE commands to get or modify the entity’s state.
Additionally, CoAP provides an observation mode, where observers can indicate the entity objects they wish to observe via the OBSERVE command. When the state of the entity object changes, the observer can receive the latest state of the entity, similar to the subscription feature in MQTT. The communication model of CoAP is shown in Figure 2-3.
4. LwM2M Protocol
The LwM2M (Lightweight Machine-To-Machine) protocol is a lightweight protocol defined by the Open Mobile Alliance (OMA) suitable for IoT. It uses RESTful interfaces to provide device access, management, and communication functions, and is also suitable for resource-constrained devices. The architecture of the LwM2M protocol is shown in Figure 2-4.
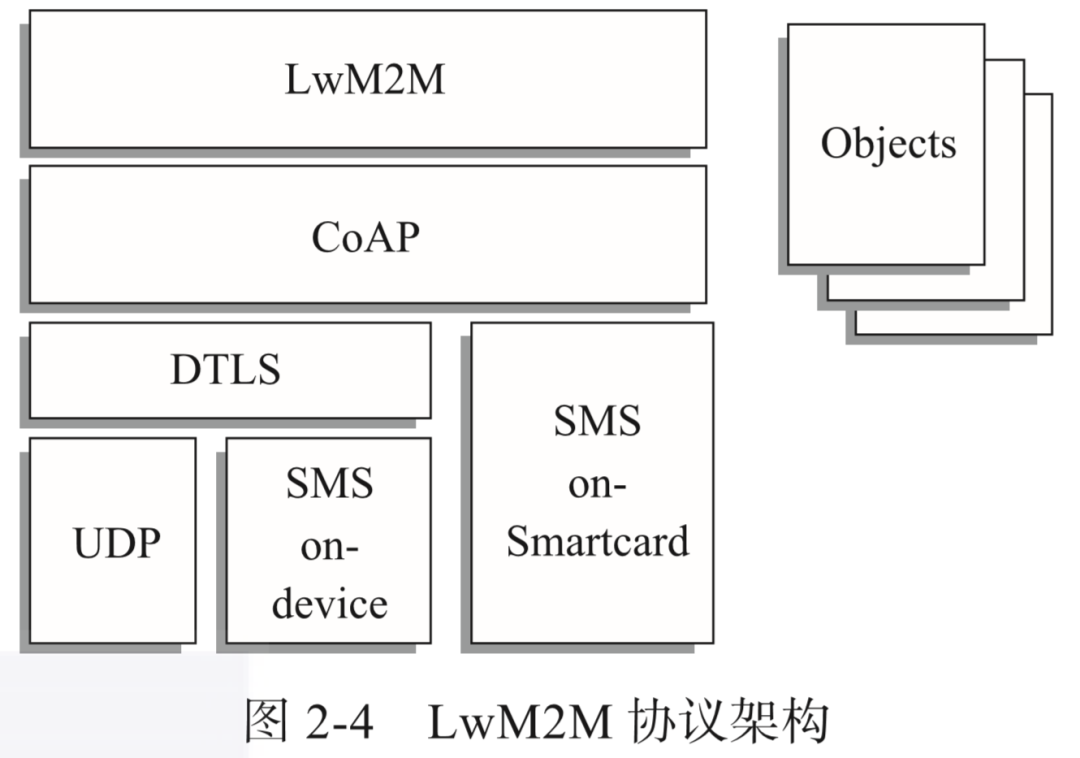
The LwM2M protocol uses the CoAP protocol for data and signaling transmission. In the LwM2M protocol architecture, the CoAP protocol can run on top of UDP or SMS (Short Message Service) and achieve secure data transmission through DTLS (Datagram Transport Layer Security).
The LwM2M protocol architecture mainly includes three entities: the LwM2M Bootstrap Server, the LwM2M Server, and the LwM2M Client.
The LwM2M Bootstrap Server guides the LwM2M Client to register and connect to the LwM2M Server, after which the LwM2M Server and LwM2M Client can interact through the protocol-specified interfaces.
5. HTTP Protocol
As mentioned earlier, the Internet of Things is also part of the internet; the HTTP protocol, widely used in the internet, can also be applied to IoT in appropriate environments.
On devices with ample computing and hardware resources, such as those running the Android operating system, HTTP can be used to upload and download data, just like in mobile app development. Devices can also use WebSockets running on HTTP to actively receive data from the server.
6. LoRaWAN Protocol
The LoRaWAN protocol is a low-power wide-area network protocol proposed and promoted by the LoRa Alliance. It differs from the previously introduced protocols. MQTT and CoAP protocols operate at the application layer, using TCP or UDP for data transmission, with the entire protocol stack running on IP networks. In contrast, the LoRaWAN protocol is a physical/data link layer protocol that addresses how devices connect to the internet and does not operate on IP networks.
LoRa (Long Range) is a wireless communication technology that features long-range communication and low power consumption. In the above scenario, users can set up networks using LoRaWAN technology by installing LoRa-supporting modules on engineering equipment.
Data can be sent through LoRa relay devices to a LoRa gateway with internet access located outside the tunnel. The LoRa gateway then encapsulates the data into a protocol packet (such as MQTT) that can be transmitted via TCP or UDP in the IP network and sends it to the cloud data center.
7. NB-IoT Protocol
The NB-IoT (Narrow Band Internet of Things) protocol, like the LoRaWAN protocol, is a physical/data link layer protocol for connecting devices to the internet.
Unlike LoRa, the NB-IoT protocol is built and operates on cellular networks, consuming less bandwidth, and can be directly deployed on existing GSM or LTE networks. Devices equipped with NB-IoT chips and corresponding IoT cards can connect to the NB-IoT base station to access the internet. Additionally, the NB-IoT protocol does not require gateways for protocol conversion, allowing connected devices to use IP networks for data transmission directly.
Compared to traditional base stations, the NB-IoT protocol has improved gain by about 20dB, covering areas previously difficult to reach, such as underground garages, pipelines, and basements.
For more methods on building an IoT platform from scratch, we recommend reading “IoT System Development: Building an IoT Platform from Scratch”.
About the Author: Fu Qiang, a senior IoT technology expert with over 10 years of experience, focuses on the design and development of IoT platforms and products, and is very familiar with various IoT protocols and system architectures. He is currently the co-founder and CTO of a smart community solution company, having previously worked at Trend Micro, Nokia China, and startups in Germany and Silicon Valley.
This article is excerpted from “IoT System Development: Building an IoT Platform from Scratch”.
-END-
Source: Big Data DT
Disclaimer: The above content is forwarded; if there are any infringements, please contact the editor! For contact information, please click on the image link below ☟

