1. Physical Memory Layout Formula
When you see an address like 0B3F:0100 in debug, remember the physical address calculation formula:
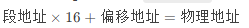
For example, 0B3F*10h+0100=0C3F0. This formula explains why CS:IP always points to strange memory locations (a legacy black magic of old programmers).
2. Core Command Anatomy
Command Prototype: -a [address]Parameter Description: If address is not filled, it defaults to assembly starting from CS:0100
-a 100
0B3F:0100 mov ax,1234 ; Generates machine code B83412
0B3F:0103 push ds ; Generates machine code 1ECommon Mistake Warning: The code generated by the a command may automatically adjust the instruction length, so be sure to manually calculate stack balance when modifying interrupt programs!
Command Prototype: -e address "string"Parameter Description: Directly modify memory with ASCII characters
-e 100 "Hello,Debug!" ; Writes 48 65 6C 6C 6F... to memory 100Unpublished Tip: Modify the interrupt vector table (for example, INT 21h is located at 0000:0084)
-e 84 00 00 00 10 ; Points INT21h to 1000:00003. BIOS Interrupt Debugging Practice
Combo Techniques: t single-step execution vs g breakpoint execution
-g=100 105 ; Stops execution at CS:0105
-t 2 ; Single-step execute 2 instructionsDebugging INT 10h display interrupt:
mov ah,0Eh ; Function number
mov al,'A' ; Character
int 10h ; Set breakpoint hereRegister Tracking Record:
Code PositionBefore Execution: AX=0E41 BX=0000
After Execution: AX=0E41 BX=0041 (Display service may modify BX)4. Environmental Differences Comparison Table
| Command | DOSBox Behavior | VirtualBox Performance |
|---|---|---|
d 0:0 |
Displays real interrupt vector table | May return all zeros |
g=c800:0 |
Executes ROM BIOS code normally | Triggers virtual machine protection mechanism crash |
5. COM Program Cracking Example
Target Program: test.com for password verification (assuming password comparison is at offset 015A)
-u 015A
015A 3A07 CMP AL,[BX] ; Key comparison instruction
015C 7405 JZ 0163 ; Cracking point: 74->75Cracking Steps:
-
-g 015Astops at the comparison point -
Observe AL register (user input) and DS:BX (correct password)
-
-e 015C 75modifies jump condition -
-wwrites back to disk (length of file must be calculated in advance)
6. Engineer’s Ramblings
-
When you see
-dcommand displayingBE 00 01, is it dataBE0001or instructionmov si,0100? It depends on the context! (A classic philosophical question in debug) -
When modifying FLAGS with
-rcommand, remember to use binary bit operations: the 8th bit is the TF flag, setting it to 1 enables single-step trap -
When searching memory with
-scommand, it’s recommended to first use-fto fill a specific pattern (likeCCbreakpoint instruction), then locate the key code segment
Appendix: Complete 11 Command Quick Reference Table (with hidden engineer notes)
-
A – Assemble (be careful of auto-completion of ret instruction)
-
D – Display memory (hexadecimal hell)
-
E – Edit memory (essential for modifying interrupt vectors)
-
F – Fill memory (create a memory pollution scene)
-
G – Execute to breakpoint (pay attention to parameter order)
-
L – Load program (for COM files only)
-
M – Move memory (may overwrite key code)
-
R – Register operations (FLAGS is a bitmask)
-
T – Single-step tracing (will enter INT calls)
-
U – Disassemble (instruction length may be incorrect)
-
W – Write back to disk (dangerous operation! Must calculate CX length)