Abstract
1
Background
With the continuous development and advancement of science and technology, especially with the popularization of 5G technology, the Internet of Things is becoming more mature and has broader development prospects. As the number of mobile devices accessing IoT networks significantly increases, wireless LAN technologies such as Bluetooth and Wi-Fi are widely applied in IoT.
Moreover, industrial control systems, as a crucial component of national infrastructure, are now widely used in industries such as energy, transportation, water conservancy, and municipal services. However, with the continuous expansion of industrial control systems, challenges such as wiring difficulties and high costs in harsh industrial environments have emerged. Therefore, wireless network technology is gradually being widely applied in the field of industrial control.
Wireless LAN technology brings convenience to the IoT and industrial fields, but in practical applications, its open wireless channels are more susceptible to security threats. To enhance the security of wireless technology applications in the IoT and industrial fields, it is necessary to study the security threats and protection strategies faced by wireless LANs in different application scenarios.
2
Wireless Technology Security in IoT
2.1 Applications of Wireless Technology in IoT
Data transmission in the IoT can occur through either wireless or wired methods. Although wired technologies offer better stability, faster transmission speeds, and more reliable transmission, their convenience and practicality are relatively lacking. With technological advancements, the stability and reliability of wireless technologies have been continuously improving, leading to their broader application in the IoT field. Various types of wireless technologies exist, such as wireless RF technology, NFC, Wi-Fi, and Bluetooth.
Wi-Fi technology, as a form of wireless LAN technology, can connect a greater number of nodes and, since the introduction of the 802.11ac standard, supports the 5GHz frequency band, significantly enhancing connection speeds and further optimizing user experience. Meanwhile, in IoT application scenarios, devices generally require not only to connect to the network but also to communicate and exchange data with each other, which Wi-Fi technology meets well.
NFC (Near Field Communication) is a near-field communication technology evolved from the integration of network interconnection and RFID, based on point-to-point communication, allowing identification and data exchange among devices within effective distances. Applications of NFC technology include identity recognition and smart tags.
Bluetooth technology, as a short-range wireless communication technology, provides convenient, fast, and low-power data exchange between devices at a low cost. Bluetooth technology is commonly used in smart wearable devices and smart homes, making it one of the most prevalent IoT technologies in daily life. With the development of mobile smart terminals, Bluetooth technology continues to expand.

Figure 1: Wireless Technology in IoT
2.2 Network Security Issues of Wireless Technology in IoT
Firstly, there is the issue of wireless network intrusion. Compared to wired networks, wireless technology expands the openness of network systems, allowing attackers to intrude into wireless communication networks without physical links, greatly increasing the likelihood of system attacks. Attackers can exploit Bluetooth protocol vulnerabilities to send forged malicious messages to nearby Bluetooth users and can even invade Bluetooth-enabled smartphones to make calls and steal users’ personal data.
Secondly, data transmission security is a concern. Many IoT devices have data collection and upload capabilities; however, due to the instability of wireless transmission channels, some unencrypted or weakly encrypted data transmission methods pose risks to data transmission security. For example, for Wi-Fi using weak encryption methods like WEP and WPA, attackers can easily crack plaintext information using freely available hacking tools without requiring high technical skills or extended time, thus stealing sensitive information.
Thirdly, privacy security is an issue. For instance, the NFC function commonly found in smartphones can read bank card information. If maliciously exploited by attackers, this could reveal users’ bank card numbers, electronic wallet balances, recent spending bills, and other private data. Additionally, many non-encrypted access cards in daily life can be easily copied by malicious actors using simple NFC tag cloning techniques, allowing them to create clone cards that generally have the same permissions as the original cards, enabling identity fraud and unauthorized access to controlled areas.
2.3 Security Protection Strategies for Wireless Technology in IoT
The application of wireless technology is a trend and innovative driving force in the development of the IoT. To address the network security issues of wireless technology in the IoT, the following protection strategies are proposed:
Firstly, strengthen access control for wireless networks. The inherent openness of wireless networks is not the fundamental reason for their susceptibility to attacks. To reduce and mitigate security risks in wireless IoT networks, scientific management of shared information such as keys—regarding their generation, distribution, modification, and destruction—is necessary; employing strong encryption security transmission modes to protect data transmission; and formulating more comprehensive network access control strategies to ensure dedicated network usage.
Secondly, enhance security authentication. A robust identity authentication model can prevent unauthorized user devices from accessing the IoT network in advance, serving as a fundamental security defense method. In the IoT network, various access or operational permissions are typically determined by user identity or device type. Identifying the true identity of accessors and employing secure encryption authentication can effectively protect the security of the IoT network. In practical applications, wireless access points can be configured outside of firewalls and other network security devices, and when using Wi-Fi for wireless transmission, more secure encryption methods such as WPA-PSK/WPA2-PSK and WPA/WPA2 should be employed.
Thirdly, regularly audit access points. With the increasing complexity of wireless IoT network applications, the number of devices accessing the network has increased, and the types of devices have become more complex and dynamic. Security management and auditing must also have corresponding requirements, necessitating regular audits of various access points in the IoT network. Consider implementing detection systems for unauthorized internal connections to assist network security administrators or users in promptly identifying illegal access points for effective blocking measures.
3
Wireless Network Security in the Industrial Field
3.1 Wireless Network Technology in Industrial Control Systems
The application of wireless network technology in industrial control systems also has many advantages.
Firstly, it is cost-effective. Compared to traditional wired networks, wireless networks can be placed anywhere without spatial constraints and do not incur wiring costs. Wireless network technology can reduce installation and maintenance costs for industrial control networks by up to 90%, making it key to cost control in industrial control systems.
Secondly, it offers high networking flexibility. During the networking process, devices connected via wireless technology exhibit significantly increased mobility, allowing users to quickly, conveniently, and flexibly restructure systems when industrial application needs change.
Thirdly, it provides high reliability. In wired networks, damage to cables and connectors can easily cause network failures, leading to higher maintenance costs. The use of wireless network technology in industrial control sites can mitigate such issues, improving the reliability of device networking to some extent.
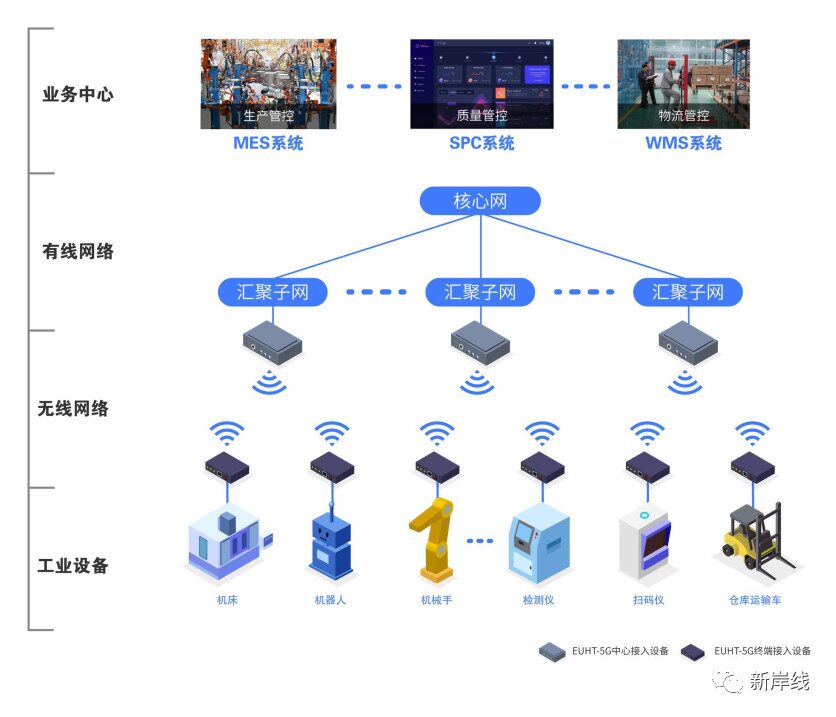
Figure 2: Wireless Network Technology in Industrial Control Systems
3.2 Security Issues of Wireless Networks in Industrial Control Systems
Establishing a comprehensive and practical security protection system is crucial for the application of wireless networks in industrial control systems. Currently, the main wireless network security standards for industrial control systems both domestically and internationally include ISA100.11a, Wireless HART, and WIA-PA. Among these, the Wireless HART standard has higher security, implementing identity authentication, key management, and other protective measures, making it the most widely applied industrial wireless network standard globally. However, the Wireless HART protocol still has certain vulnerabilities that attackers can exploit. The current security issues of wireless networks in industrial control systems can be summarized as follows.
Firstly, there are inherent security risks in wireless networks.
-
Network Architecture: With the integration of wireless networks, closed network systems transform into open systems, and the lack of effective maintenance and updates for protective measures reduces the overall security of the network. -
Data Flow: There is a lack of effective control over data flow, making it impossible to restrict accessing mobile devices. -
Network Devices: The configuration rules for firewalls and ACLs lack scientific rigor, increasing security risks.
Secondly, industrial control networks face external threats.
-
Information Sniffing and Eavesdropping: Attackers can launch specific network attacks against monitored applications using specific methods. -
Flood Attacks Blocking Channels: Attackers can congest wireless networks by attacking with a large volume of invalid information. -
Identity Fraud Intrusion: Attackers can intrude into networks using identity fraud by masquerading as legitimate identities, such as impersonating a gateway to control devices. -
Human Security Risks: Attackers can obtain usernames and passwords for wireless networks through human factors, intruding into wireless networks to launch attacks.
3.3 Security Protection Strategies for Wireless Networks in Industrial Control Systems
Firstly, establish a layered defense structure in industrial control areas. The layered defense structure in industrial control areas divides the entire network system into different security domains based on various structural functions. The external network is treated as an independent area, categorized as an external domain; for enterprise-level systems, enterprise-level LANs and firewalls are categorized as enterprise domains; database servers, industrial firewalls, and IPS are categorized as data domains; and field device-level firewalls are categorized as control domains. Firewalls are deployed between the data and control domains to prevent attacks across different levels.
Secondly, implement information security protection strategies in industrial control areas. Limit access permissions for devices, introduce identity authentication requirements; employ tiered encryption to reduce the risk of breaches; deploy network intrusion detection devices for effective monitoring and early warning; design auditing and measurement systems for industrial control networks to ensure good control of network traffic; and formulate security monitoring and emergency response plans to enforce security accountability.
4
Conclusion
Wireless network technology is increasingly applied in the fields of IoT and industrial control. Therefore, addressing the data communication security issues of wireless networks is a crucial approach to ensuring the steady advancement of the IoT era and safeguarding the security development of industrial control systems in our country. This article introduces wireless network technologies in the IoT and industrial control fields, explores the security threats faced in their application scenarios, and finally provides corresponding protection strategies. It is hoped that this will offer some safety suggestions for the future construction of wireless network technology in the IoT and industrial control fields.
References
[1] Wang Tiansen. Analysis of Network Security Issues and Countermeasures for Wireless Technology in the IoT. Journal of Network Security and Information Technology, 2021(11):27-30.
[2] Qu Jiaxing, Zhou Ying, Wang Xizhong, Zhang Qingjiang. Research on the Wireless Network Security System of Industrial Control Systems. Information Technology, 2013, 37(01):36-38+42. DOI:10.13274/j.cnki.hdzj.2013.01.025.
[3] Li Jun, Gao Rui, Hang Xiao. Analysis and Suggestions for Network Security Issues of Wireless Technology in the IoT. Network Security Technology and Applications, 2021(08):84-85.
[4] Zhang Meilan, Cai Xinyuan, Wang Xiaofei. Security Analysis of Industrial Wireless Communication Technology Based on Wireless HART Protocol. Information Security and Communication Confidentiality, 2016(09):44-45.
[5] Chen Yibin. Research on Information Security Design and Protection in Industrial Wireless Network Environments. Electronic Testing, 2021(06):61-62+42. DOI:10.16520/j.cnki.1000-8519.2021.06.026.
China Association for Confidentiality
Science and Technology Branch
Scan to follow us

Author: Li Shuang
Editor: Xia Tian
Top 5 Exciting Articles of 2021 Review
Insights on Shredding Recovery Technology for Carrier Destruction
Recent Exciting Articles Review