Today, I will share with you some common knowledge points about TCP network, which you will often encounter in daily work or interviews. Considering the length of the content, I suggest you bookmark it and digest it slowly.
If it helps, please share it with your friends; “It’s better to enjoy together than to enjoy alone.”
First, let’s have a table of contents to give everyone an intuitive understanding of the article’s content.
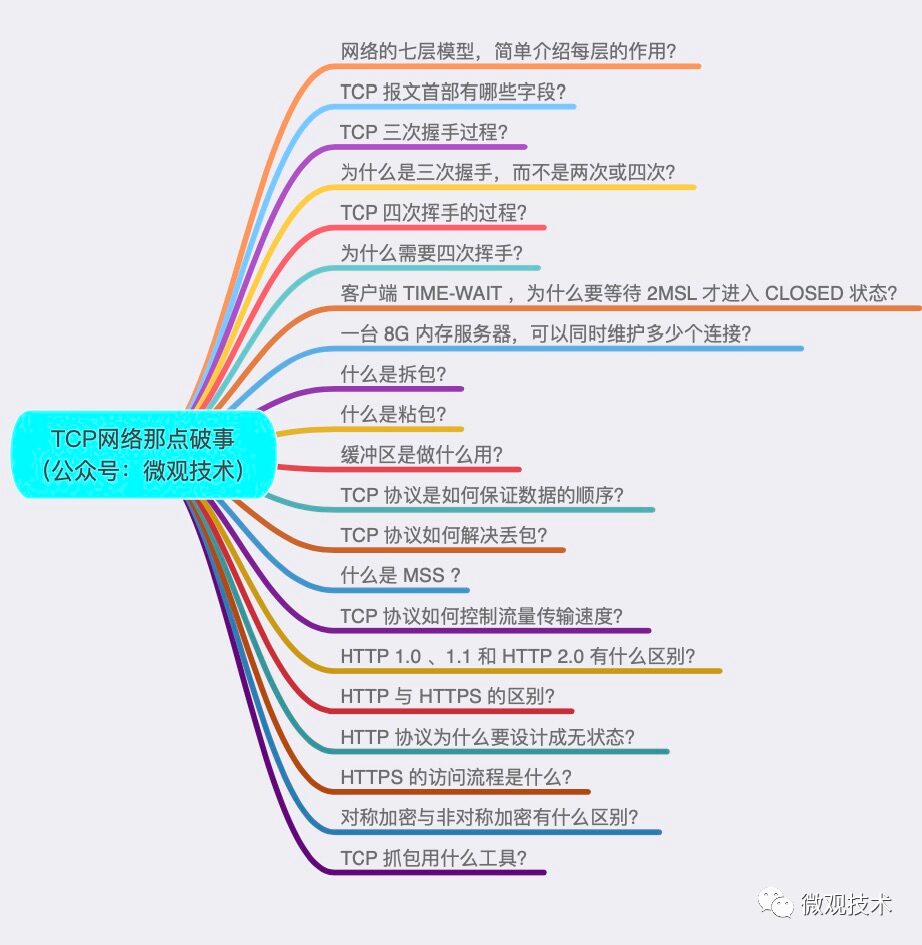
What are the functions of the seven layers of the network model?
Answer: It is divided into 7 layers, from bottom to top:
-
Application Layer: The interface between computer users and the network, common protocols include: HTTP, FTP, SMTP, TELNET. -
Presentation Layer: Data representation, security, and compression. Converts application processed information into a format suitable for network transmission. -
Session Layer: Establishes and manages sessions between a local host and a remote host. -
Transport Layer: Defines the protocol port numberfor data transmission, as well as flow control and error checking, ensuring that messages are transmitted correctly. Protocols include TCP, UDP. -
Network Layer: Routing algorithms for logical addressing, achieving the best path selection between different networks. Protocols include IP, ICMP. -
Data Link Layer: Receives bit stream data from the physical layer and encapsulates it into frames for transmission to the upper layer; similarly, it disassembles data frames from the upper layer into bit stream data to be forwarded to the physical layer. The data at this layer is called frames. -
Physical Layer: Establishes, maintains, and disconnects physical connections. Transmits bit streams (converting 1s and 0s into varying current strengths for transmission, which are then converted back to 1s and 0s upon arrival, commonly referred to as analog-to-digital and digital-to-analog conversion). The data at this layer is called bits.
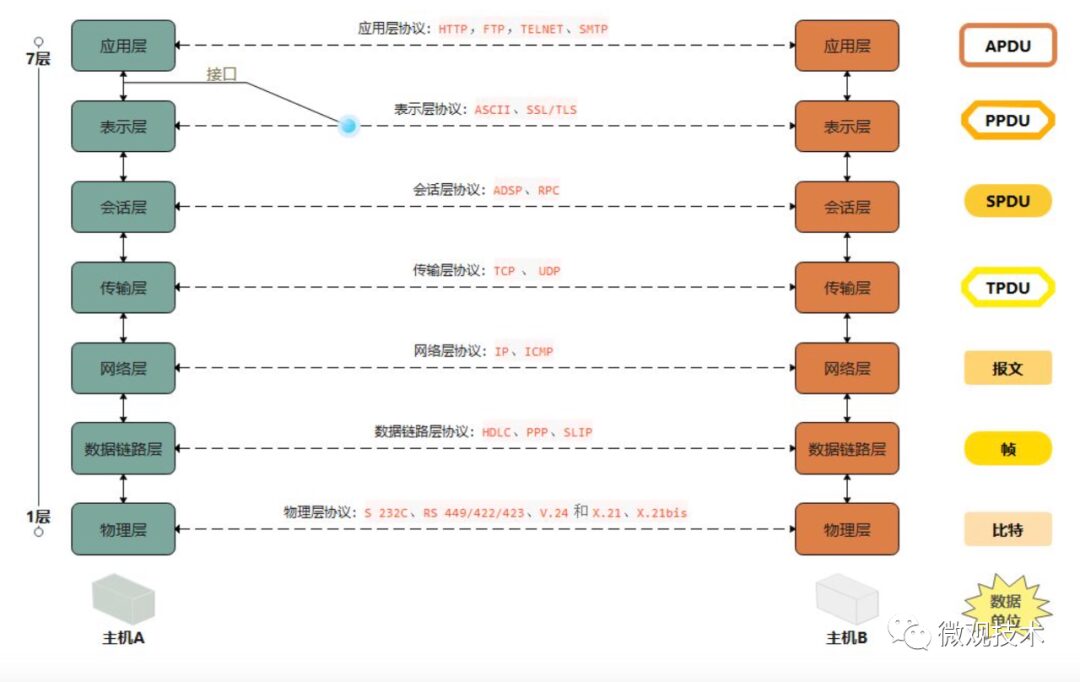
What fields are included in the TCP header?
Answer:
-
Source Port, Destination Port: Each occupies 2 bytes, indicating which process the data comes from and which process it goes to. -
Sequence Number: Occupies 4 bytes; each byte of data transmitted in the TCP connection has a sequence number. -
Acknowledgement Number: Occupies 4 bytes; the response to the TCP segment sent by the other party. -
Data Offset: Header length, occupies 4 bytes, indicating how far the data in the TCP segment is from the start of the TCP segment. -
6-bit Flags: -
URG: Indicates whether the urgent pointer is valid. -
ACK: Indicates whether the acknowledgement number is valid. -
PSH: Notifies the receiving application to immediately read data from the TCP buffer. -
RST: Indicates a request for the other party to re-establish the connection. -
SYN: This is a connection request or acceptance message. -
FIN: Notifies the other party that this side wants to close the connection. -
Window Size: Occupies 4 bytes, used for TCP flow control. It tells the other party how many bytes of data the TCP receiving buffer can still accommodate, allowing the other party to control the sending speed. -
Checksum: Occupies 2 bytes, filled by the sender; the receiver performs a CRC check on the TCP segment to verify whether it has been damaged during transmission. The verification range includes both the header and data, which is an important guarantee for TCP’s reliable transmission. -
Urgent Pointer: Occupies 2 bytes, a positive offset. Its value added to the sequence number indicates the sequence number of the next byte of urgent data sent from the sender to the receiver.
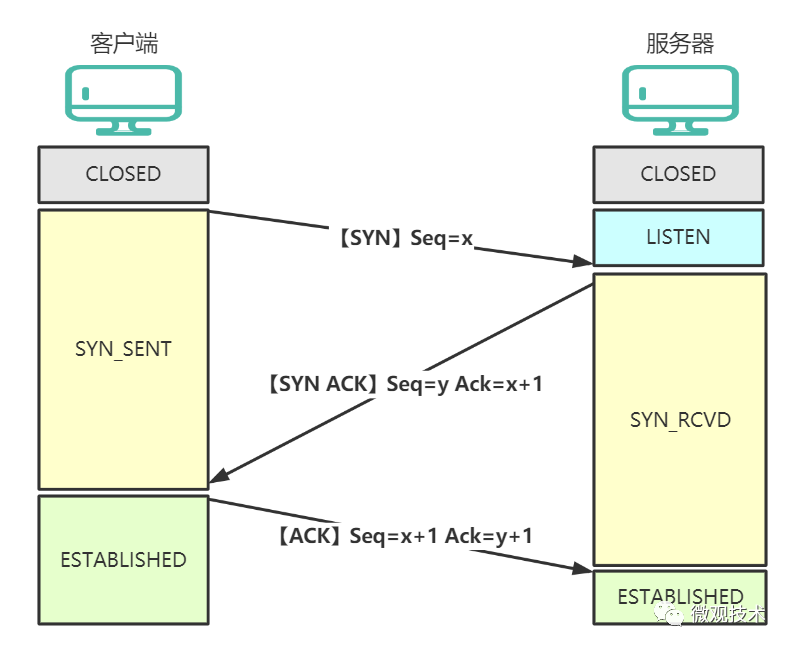
What is the process of the TCP three-way handshake?
Answer: The goal is to synchronize the sequence numbers and acknowledgement numbers of both parties and exchange TCP windows.
-
First handshake, the client sends (seq=x), the client enters <span>SYN_SEND</span>state. -
Second handshake, the server responds (Seq=y, Ack=x+1), the server enters <span>SYN_RCV</span>state. -
Third handshake, after the client receives the server’s confirmation, it sends (Ack=y+1), and the client enters <span>ESTABLISHED</span>state. When the server receives this packet, it also enters<span>ESTABLISHED</span>state.
Why three-way handshake instead of two or four?
Answer:
If there were only two handshakes, after the server sends the <span>SYN/ACK</span> message to the client, it would assume the connection is established. However, if the client does not receive the message, the client has not established a connection, which leads to resource waste on the server.
Using two handshakes cannot establish a TCP connection, while using three handshakes is the minimum required to establish a connection.
What is the process of TCP four-way teardown?
Answer:
-
First teardown: The client sends a connection release message to the server. -
Second teardown: After receiving the connection release message, the server immediately sends an acknowledgment message. At this point, the TCP connection is in a half-closed state, meaning the connection from the client to the server has been released, but the connection from the server to the client has not yet been released. This indicates that the client has no data to send, but the server may still need to send data to the client. -
Third teardown: The server sends a connection release message to the client. -
Fourth teardown: After the client receives the server’s connection release message, it immediately sends an acknowledgment message. At this time, the client enters the <span>TIME-WAIT</span>state. Note that the TCP connection from the client has not yet been released; it must wait for 2*MSL (Maximum Segment Lifetime) before entering the<span>CLOSED</span>state.
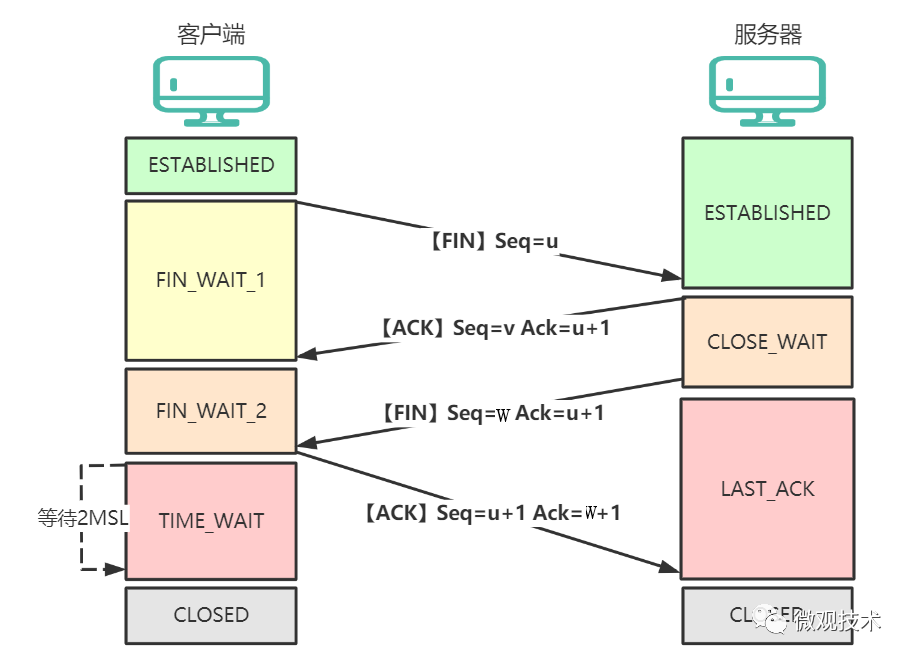
Why is four-way teardown necessary?
Answer: TCP is<span>full-duplex</span>. After one side closes the connection, the other side can continue to send data. Therefore, the four-way teardown separates the disconnection process into two independent processes.
Why does the client wait 2MSL before entering the CLOSED state?
Answer: MSL is the maximum lifetime of a segment in the network.
It ensures that the ACK message can reach the server, allowing the server to close the connection normally. After sending the last ACK segment, the client waits for 2MSL to ensure that all segments generated during the connection’s lifetime disappear from the network. This prevents old connection request segments from appearing in the next connection.
How many connections can a server with 8GB of memory maintain simultaneously?
Answer: Each sending and receiving buffer is 4k, and considering the socket descriptor, the minimum memory occupied by a TCP connection is 8k. Therefore, the maximum number of connections is:<span>8*1024*1024 K / 8 K = 1048576 connections</span>, which is approximately 1 million TCP long connections.
What is packet fragmentation?
Answer: The transport layer cannot have packets that are too large; based on this limitation, data is often split into multiple TCP segments (<span>TCP Segment</span>) for transmission based on buffer size. When receiving data, these TCP segments are reassembled into the original data. In simple terms, it consists of several processes: fragmentation—transmission—reassembly.
What is packet sticking?
Answer: To solve the problem of data being too small and to prevent<span>multiple sends</span> from occupying resources, the TCP protocol merges them into a single TCP segment for sending, which is then restored into multiple pieces of data at the destination.
What is the purpose of the buffer?
Answer: A buffer is a region in memory created for buffering purposes. When applications frequently send and receive data through the network interface card, the card can only process one at a time. When the card is overwhelmed, data needs to queue, which means placing data into the buffer.
Note: The size of the TCP Segment must not exceed the buffer size.
How does the TCP protocol ensure data order?
Answer:
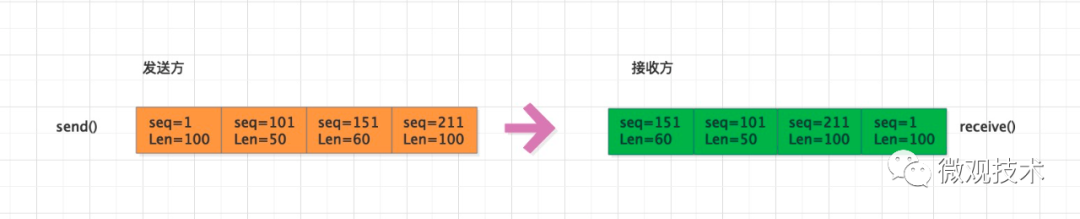
Large data is fragmented into multiple segments for sending, which can ensure order, but due to the complexity of the network environment, it cannot guarantee that they arrive in order. To solve this problem, each segment is numbered with a<span>Sequence Number</span>, and when receiving data, it is sorted by Seq.
Note: seq is the cumulative number of bytes sent.
How does the TCP protocol handle packet loss?
Answer: Packet loss requires retransmission; the key is how to determine whether a packet has been lost!
For each data packet, the receiver sends a response to the sender. Each TCP segment sent indicates how much data has been received by the receiver, represented by the <span>Acknowledgement Number</span> (abbreviated as ACK).
Note: ack is the cumulative number of bytes received, indicating that all packets prior to this one have been received.
What is MSS?
Answer: MSS stands for <span>Maximum Segment Size</span>. It is an optional item in the TCP Header that controls the size of TCP segments and cannot be determined unilaterally; it needs to be negotiated between both parties.
How does the TCP protocol control the speed of data transmission?
Answer: In simple terms, it is controlled through the<span>sliding window</span>. The sizes of the sending and receiving windows can be used to control the flow rate of the TCP protocol. The larger the window, the more data can be sent and received simultaneously, increasing throughput. However, the larger the window, the greater the loss if data errors occur, as more data needs to be retransmitted.
Every TCP request must have a response; if a request does not receive a response, the sender will assume there was a failure in the transmission, triggering a retransmission. To improve throughput, a TCP segment can continue to be sent even if the previous segment has not received a response.
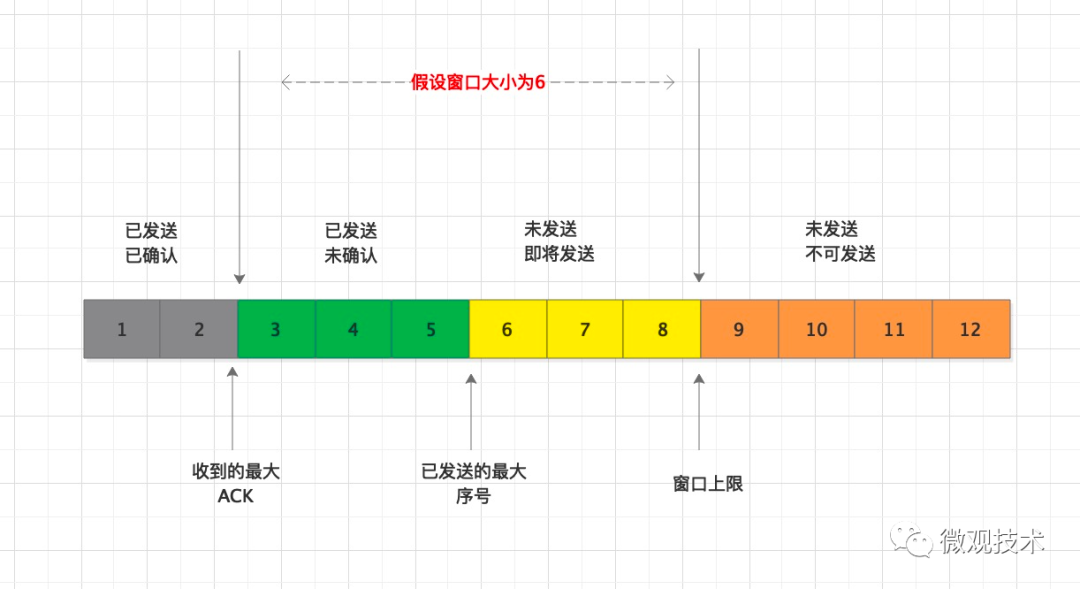
-
The window area contains two types of data: sent but unacknowledged and unsent (to be sent). -
If the group with the smallest sequence number receives an ACK, the window will slide to the right. -
The size specification of the sliding window may change, and the latest value needs to be taken from the ACK data packet in real-time. -
If the group with the smallest sequence number has not received an ACK for a long time, it will trigger the retransmission of all data in the window.
What are the differences between HTTP 1.0, 1.1, and HTTP 2.0?
Answer:
1. HTTP 1.0
-
Defaults to short connections; each interaction with the server requires a new connection.
2. HTTP 1.1
-
Defaults to persistent connections; establishes one connection, and multiple requests are completed through this connection.
3. HTTP 2.0
-
Binary framing: Adds a binary framing layer between the application layer and transport layer, splitting all transmitted information into smaller messages and frames, encoded in binary format. Reduces server pressure, uses less memory, and increases connection throughput. -
Multiplexing: Allows multiple request-response messages to be initiated simultaneously through a single HTTP/2.0 connection. -
Header compression: Uses the <span>Hpack</span>header compression algorithm to compress headers and reduce duplicate transmissions. -
Server push: The server actively pushes some resources to the browser and caches them.
What are the differences between HTTP and HTTPS?
Answer: HTTPS = HTTP + SSL/TLS
-
HTTP uses plaintext communication; port 80. -
HTTPS adds <span>SSL/TLS protocol</span>on top of HTTP, which relies on certificates to verify the server’s identity and encrypts the communication between the browser and server. Port 443.
Why is the HTTP protocol designed to be stateless?
Answer: HTTP is a stateless protocol; each request is executed independently, request/response. The important reason for this design is to reduce architectural complexity. Once a server has a state,<span>scaling, shrinking, and routing</span> will be constrained. Stateless protocols do not require the server to retain user information across multiple requests.
However, you may ask, what if there are login requirements? The HTTP protocol provides an extension mechanism by adding cookies in the header, stored on the client side, and automatically carried with each request, using space to exchange for time, to satisfy the association of requests. Although this wastes some network bandwidth, it reduces complexity. Of course, to lessen the network burden, browsers limit the size of cookies, and different browsers have slightly different standards; for example, Chrome limits to a maximum of 180 cookies, with each cookie size not exceeding 4096 bytes.
What is the access process for HTTPS?
Answer:
-
The client initiates an HTTP request, informing the server of the hash algorithms it supports. -
The server returns its information to the client in the form of a <span>digital certificate</span>(the public key is in the certificate, and the private key is held by the server). -
After the client receives the server’s response, it first verifies the legality of the certificate (whether the address in the certificate matches the address being accessed, whether the certificate has expired). -
If the certificate verification passes, a random <span>symmetric key</span>is generated and encrypted using the certificate’s public key. -
The client sends the encrypted key back to the server. -
The server decrypts it using the private key, obtaining the client’s key. -
Then, the client and server use the key for plaintext encryption, secure communication, and symmetric decryption.
What are the differences between symmetric and asymmetric encryption?
Answer:
-
Symmetric encryption: Uses the same key for both encryption and decryption. Fast. Common examples include: AES, DES. -
Asymmetric encryption: Public and private keys appear in pairs; the public key encrypts data, and the private key decrypts it. Common examples include: RSA, DSS.
What tools are used for TCP packet capturing?
Answer: Wireshark, the most widely used network protocol analyzer. It has very rich functionality.
-
Supports hundreds of protocols. -
Real-time capture, offline analysis. -
Supports Windows, Linux, macOS, Solaris, FreeBSD, NetBSD, and other platforms; -
Graphical interface operations. -
Supports Gzip. -
Supports IPSec.