
Why TCP/IP Exists
All around the world, various computers running different operating systems serve their purposes. However, the methods they use to express the same information can vary greatly. It’s akin to how God confused the languages of people in the Bible, preventing them from cooperating. Computer users realized that individual computers would not be very effective on their own. Only by connecting them could they unleash their full potential. Thus, people sought ways to connect computers with wires.
However, simply connecting them is far from enough, just like two people speaking different languages cannot communicate effectively. Therefore, they need to define some common elements for communication, and that is the purpose of TCP/IP.
TCP/IP is not a single protocol, but a collective term for a family of protocols. It includes the IP protocol, ICMP protocol, TCP protocol, and other more familiar protocols like HTTP, FTP, POP3, etc. With these protocols, computers can communicate freely, much like learning a foreign language.
TCP/IP Protocol Layering
When we mention protocol layering, we often think of the classic ISO-OSI seven-layer model, but the structure of the TCP/IP protocol family is slightly different. As shown in the figure.
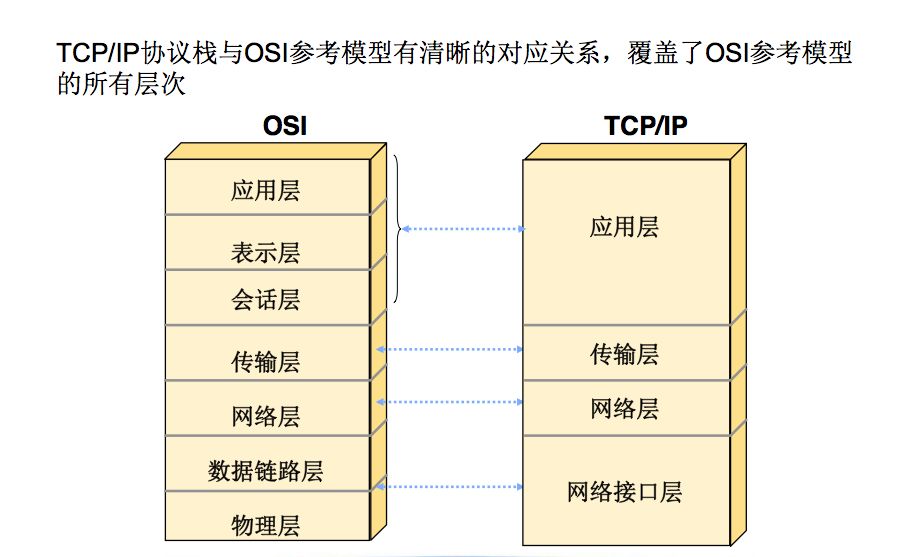
The TCP/IP protocol family is layered from top to bottom, with each layer encapsulating the one below it. The top layer is the application layer, which includes familiar protocols like HTTP, FTP, etc. The second layer is the transport layer, where the well-known TCP and UDP protocols reside (don’t tell me you haven’t used UDP to play StarCraft). The third layer is the network layer, where the IP protocol resides, responsible for adding IP addresses and other data to determine the transmission target. The fourth layer is the data link layer, which adds an Ethernet protocol header to the data being sent and performs CRC encoding to prepare for the final data transmission. Below that is the hardware layer, responsible for network transmission, defining standards for cables, network cards, etc. (we don’t need to worry about this layer since we are not dealing with network cards), which is why some books do not include this layer in the TCP/IP protocol family as it has little to do with the authors of TCP/IP protocols. The sending host encapsulates the data according to the protocol from top to bottom, while the receiving host unpacks the data according to the protocol to obtain the required data. This structure resembles a stack, which is why some articles refer to the TCP/IP protocol family as the TCP/IP protocol stack.
IP Address
Every node on the network must have a unique Internet address (also known as an IP address). Currently, the commonly used IP address is a 32-bit number, which is what we refer to as the IPv4 standard. This 32-bit number is divided into four groups, commonly represented as 255.255.255.255. Under the IPv4 standard, addresses are divided into five classes, with class B being the most commonly used. For specific classifications, please refer to other documents. It is important to note that the IP address is a combination of the network number and the host number.
Domain Name System
The Domain Name System is a distributed database that provides the service of converting hostnames (i.e., URLs) into IP addresses.
RFC
What is RFC? RFC is the standard document for TCP/IP protocols, where we can see a long list of definitions. There are currently over 4000 definitions of protocols, but we only need to learn about a handful of them.
Port Number
Note that this number is a logical number used in TCP and UDP, not a hardware port. When we say that a certain port has been blocked, we are simply filtering out IP packets with that number at the IP layer.
Application Programming Interface
Common programming interfaces now include sockets and TLI. The former is sometimes referred to as “Berkeley socket,” highlighting Berkeley’s significant contribution to network development.
“Learning Linux the Right Way” is a technical book based on the latest Linux system, aimed at readers with no prior knowledge. It starts with basic Linux knowledge and gradually increases the content difficulty, detailing the working principles and configuration methods of various services in the Linux system to meet the real-world requirements for operations personnel, highlighting the practicality of the content. Readers interested in learning the Linux system can click the “Read Original” button to learn more about this book. This book is also suitable for professional operations personnel as a highly valuable reference tool!