SentinelOne often discusses the concept of the autonomous SOC with their clients and the fundamental transformation it brings to daily security operations. Today, we take a third-party perspective to see how they define this concept. Additionally, in this article, SentinelOne presents a maturity model for the autonomous SOC. Like much in cybersecurity, what matters is not just the definition of a concept, but its application in the real world.
 Consistency in Common Questions
Consistency in Common Questions
Today’s security teams face increasingly complex challenges, including a surge in sophisticated attacks, rising alert volumes, an expanding attack surface, and a shortage of skilled professionals.
Previous SOC teams have never needed to analyze, investigate, and respond to threats as quickly and effectively as they do today. Moreover, we know that some tasks, such as proactive threat management and threat hunting, are relatively large in scale and are often sidelined due to the time and expertise required.
 Defining the Autonomous SOC
Defining the Autonomous SOC
Some people believe that the autonomous SOC is a futuristic, dehumanized concept where machines can unilaterally protect organizations from attacks.
Will this truly be achievable in the future? Perhaps one day, but that possibility is at best many years away. For now, a better question might be: what kind of autonomy is desirable, and to what extent can we achieve it?
SentinelOne defines the autonomous SOC as a conceptual journey with different stages. In this process, machines automate manual, labor-intensive tasks, fundamentally accelerating detection and response, thereby increasingly enhancing the efficiency of human SecOps teams.
This is a rapidly growing field of behavioral and generative AI security, with a range of types and levels of automation that can drive the work of human SOC analysts. By allowing security experts to focus on strategic, high-value work and decision-making, these tools can maximize the application of artificial intelligence in security operations.
Working in collaboration with humans means that AI and automation become more effective and accurate through continuous feedback loops. This symbiotic relationship amplifies the strengths of both, transforming the SOC into a more efficient, agile, and intelligent team.
 Empowering the Autonomous SOC Journey
Empowering the Autonomous SOC Journey
The future of the SOC lies in providing seamlessly integrated AI and automation tools for every SOC workflow to enhance the efficiency and impact of operators. AI innovations are designed to complement SOC analysts so that security teams can confidently adopt autonomous capabilities in their own way while ensuring their security is future-proof.
Introducing incremental innovations and improvements, including rule-based automation, AI-enhanced detection, and autonomous classification, can help organizations gradually build highly autonomous security, which can be a great option.
This step-by-step approach ensures that every client has the tools they need and can advance their own coherent SOC journey in the direction they choose.
 Mapping the Autonomous SOC Maturity Model
Mapping the Autonomous SOC Maturity Model
SentinelOne views the autonomous SOC through the lens of a maturity model.
They utilize a model that includes five stages, outlining the key role of automation and AI in driving progress and the specific security tasks that security teams can automate.
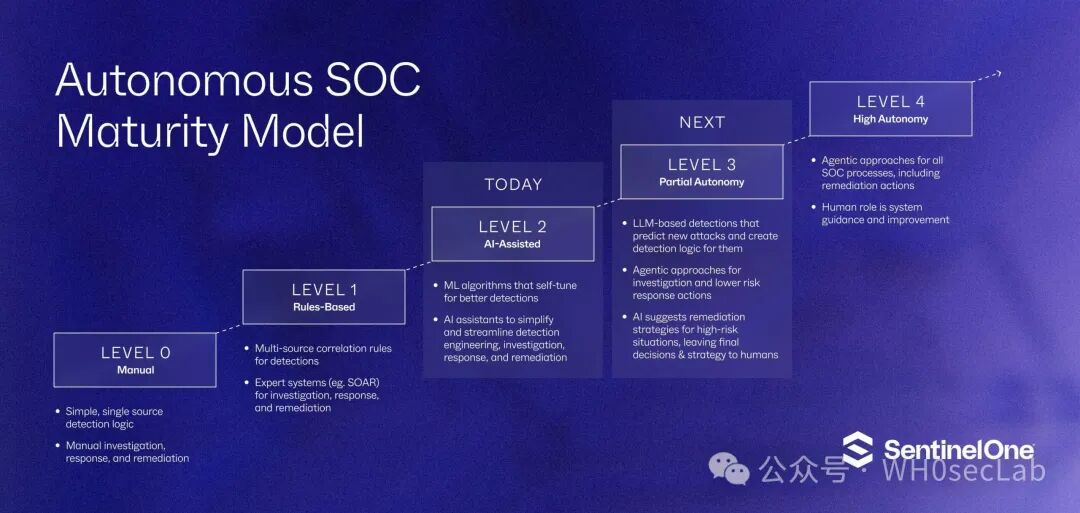
Level 0 | Manual Operations
At Level 0 of this autonomous SOC maturity model, security operations heavily rely on manual processes and simple single-source detection logic.

For example, a typical scenario might involve alerts from a firewall signaling suspicious traffic, triggering a lengthy manual investigation. Analysts need to gather context from various sources (e.g., network logs or endpoint data) to reconstruct the event.
Remedial actions such as blocking IPs or isolating infected computers are all performed manually.
Threat hunting at this maturity level requires deep expertise and extensive, time-consuming analysis, such as sifting through network logs to identify anomalous patterns. Without automation or AI assistance, this labor-intensive approach slows down detection and response, increasing the risk of advanced threats evading detection and escalating into vulnerabilities.
Level 1 | Rule-Based Operations
At Level 1 of this autonomous SOC maturity model, organizations introduce rule-based detection and response systems.

The SOC uses correlation rules to combine data from multiple sources, thereby improving the accuracy of threat detection. Security orchestration, automation, and response (SOAR) platforms begin to automate parts of the investigation and response processes, reducing manual workloads.
At this level, the security team might configure a rule that correlates multiple failed login attempts with a sudden spike in outbound network traffic from the same IP address. This triggers the SOAR system to automatically investigate whether the IP is associated with known threats and isolate endpoints if necessary.
However, despite these improvements, human expertise remains crucial for designing detection rules and managing response playbooks. To keep pace with the evolving threat landscape, SOC teams must continuously refine these rules to maintain the relevance of this Level 1 automation.
Level 2 | AI-Assisted Security Operations
At Level 2 of this autonomous SOC maturity model, AI and machine learning (ML) are introduced to elevate SOC operations beyond static rules.

The AI models in the detection engine can self-adjust based on supervised feedback or unsupervised learning, improving accuracy and reducing false positives.
AI assistants further streamline fundamental tasks such as detection engineering, classification, investigation, and response, allowing analysts to focus on higher-value activities.
For example, an AI assistant or virtual security analyst can conduct natural language-based threat investigations or hunts. Analysts can pose simple questions like, “Are there any anomalous login attempts across the network?” The AI assistant can interpret the query, scan data sources, identify patterns, and provide prioritized results without the end user needing to write complex queries or understand underlying data mappings or fields.
This simplifies the tracing process and makes threat hunting more accessible, even for less experienced teams. By introducing AI, Level 2 can respond faster and more accurately while continuously learning from past events to adapt to evolving threats.
Level 3 | Partial Autonomy
At Level 3 of this autonomous SOC maturity model, security operations move towards partial autonomy, where LLM-based systems can predict new attacks and automatically create detection logic.

This appears to be the logical next stage for the industry. AI systems will utilize agent-based methods to perform low-risk response actions, such as creating tickets or enforcing re-authentication, while human analysts will focus on supervising AI outputs and handling tasks that require deeper contextual judgment.
For instance, during an unseen ransomware attack, an LLM-based system could analyze the behavior of the malware, generate detection rules, propose judgment recommendations, and autonomously respond by creating tickets for asset owners without requiring users to write complex queries or understand data mappings.
Meanwhile, human analysts will review AI-generated results, adjust detection logic as necessary, and validate the overall response strategy. Human experts will manage high-risk decisions, such as determining whether to escalate or engage in broader incident containment efforts, ensuring that AI aligns with security policies.
Level 4 | Highly Autonomous
At Level 4 of this autonomous SOC maturity model, it is considered the ultimate stage that the autonomous SOC maturity model may reach in the future, where security operations achieve a high degree of autonomy.

Generally, there is consensus that the timing and feasibility of achieving this stage remain in question, and the potential of Level 4 depends on whether AI models shift towards reasoning and fully general artificial intelligence (AGI).
However, in this hypothetical future state, agent-based methods would handle all SOC processes, from detection and investigation to response and remediation, with minimal human intervention. Human analysts would also play a more strategic role, guiding and refining AI to adapt to emerging threats and maintain resilience.
Then, this model would enable a 24/7, intervention-free security approach, significantly reducing response times and minimizing the impact of attacks.
For example, in a highly autonomous SOC, AI systems could independently detect threats, investigate threats, and initiate remediation actions, such as rolling back systems infected with malware, revoking leaked credentials, and updating firewall rules.
 The Path to the Autonomous SOC
The Path to the Autonomous SOC
Making progress on the path to the autonomous SOC is the future of cybersecurity, where AI and automation can reduce workloads, improve detection accuracy, and shorten response times. Achieving high autonomy indeed requires a fundamental shift in perspective.
As SOCs evolve, the role of security analysts shifts from monotonous tasks and labor-intensive hands-on investigations to system oversight and optimization.
What we can foresee is that security professionals will view AI and autonomous SOC innovations as amplifications of their expertise rather than replacements, ultimately creating a safer and more resilient digital environment.
 Conclusion
Conclusion
If true autonomy is achieved in the future, will AI autonomy lead to the unemployment of analysts? This question is not only relevant in cybersecurity; I believe anyone has pondered this as AI advances.
In my personal view, the points mentioned above are not only reflected in the SOC; I believe AI will play a key role in any field, rather than a replacement role.
Even if we reach the ideal state of AI autonomy, experts will still be needed to handle more resilient situations with their expertise.