In the process of using Linux, we often encounter issues related to users and groups. For example, the most common situation is when you want to execute a command in a certain path, and you frequently see this error message.
permission denied
Anyway, I often encounter this error while using FTP to transfer files. After waiting for a long time, the transfer percentage is still zero. I wonder, is the network so slow? Why isn’t it transferring at all? Actually, I didn’t know that this is due to permission issues.
My usual fix is to directly grant 777 permissions, or to log in as an administrator using su…
You may not know what I’m talking about, and some experts may think my method is too low. Regardless, encountering this problem means that your permissions are insufficient. Why is that? Below, we need to understand users and groups in Linux.
Users and Groups
In Linux, file ownership is divided into three categories: file owner, group, and others. Here are explanations for these three concepts:
-
File Owner
Linux is a multi-user, multitasking system, which means that files created by some users may or may not be visible to others. This is a visibility issue and also a privacy issue. To consider everyone’s privacy rights, Linux has designed the role of file owner. If you have some data and files with high privacy, you can set the files to be “visible only to me”; that’s the role of the file owner.
-
Group
The concept of groups is often used in team development, especially for setting project permissions. For example, if you work in an outsourced department of a bank, and you and other outsourced departments jointly serve a bank, all outsourced teams use the same server. This involves group permission issues. If your outsourced department develops a project that you don’t want other outsourced departments to see, you can set that project to be group-visible. However, the bank is the overall responsible party, so all banks have the permission to view all your outsourced department’s projects. Therefore, you also need to set permissions for the bank.
-
Others
Others are relative to groups. Others are outside the group and do not have permission to view files within the group.
In addition to the three concepts above, there is also a top-level authority known as root, which has the highest permissions.
Linux File Permissions
After discussing the concepts of users and groups, let’s talk about how to set file permissions. This content is very important because it is key to solving the permission denied issue.
Permission Attributes
First, log into the Linux system, and using su - can switch to root identity, then execute ls -al to see the following:
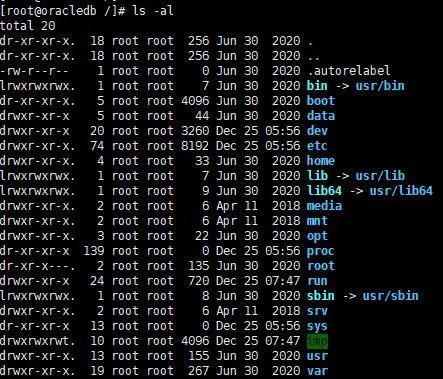
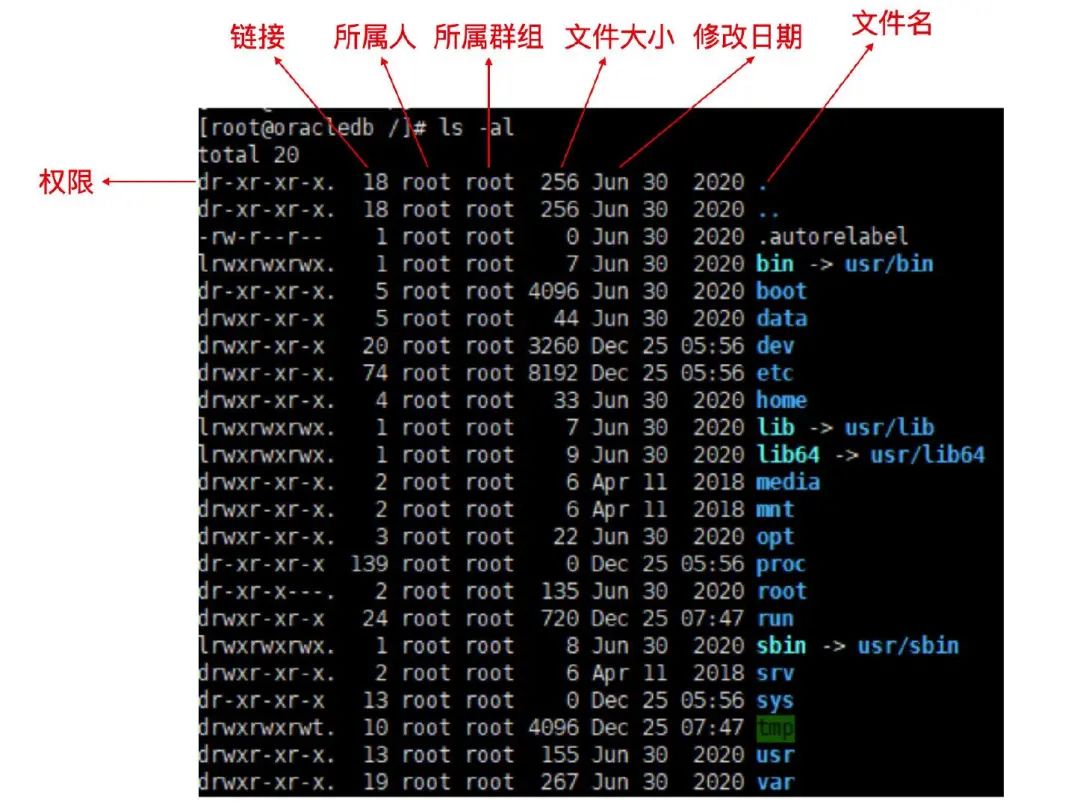
There are a total of seven columns, as shown in the image below.
When learning, you can directly use root, as subsequent commands like chgrp, chown, etc., require root to process. However, it is strongly recommended not to use root permissions in work.
You can exit root identity using exit.
In the above command, ls means list, and the option -al indicates detailed file permissions and attributes.
-
Permissions: The first column represents permissions, which are indicated by 10 characters. Taking home permissions as an example, we can list the meanings of each character.
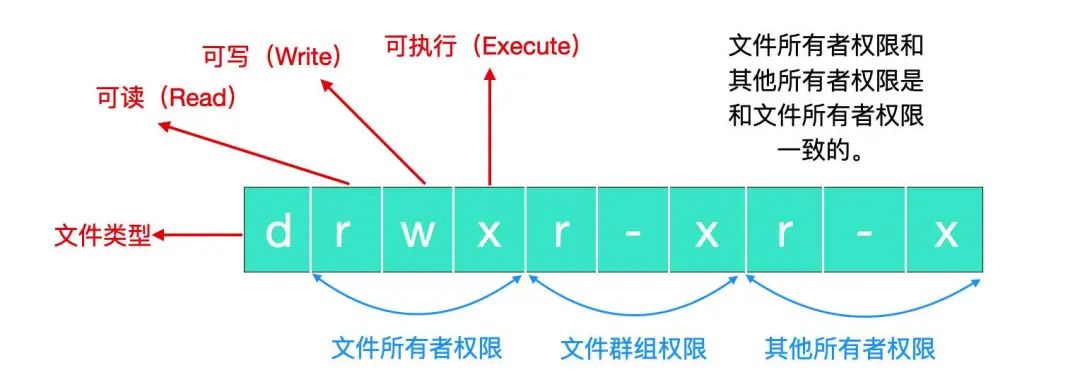
The first character indicates the file type. There are many types of files; generally, [d] indicates a directory, which can be entered using the cd command. As seen in the image, almost all are directories.
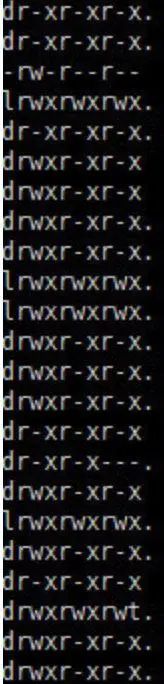
If it is [-], it indicates a file. If it is [l], it indicates a link file. If it is [b], it indicates a block device file. If it is [c], it indicates a character device file (keyboard, mouse).
The next nine characters are divided into three groups, each group of three represents the permissions of the owner, group, and others. Within each group, the permissions are a combination of three rwx. [r] means readable, [w] means writable, and [x] means executable. Note that if there is no permission, it will be replaced by –.
-
Links: This column indicates how many file names link to this node (i-node). Each file records its permissions and attributes in the file system’s
i-node. However, the directory tree we use records it by file name, so each file name is associated with an i-node, and this attribute records how many files are linked to the same i-node.
What is an i-node?
The description of i-node is very similar to what we discussed before about Sockets. A Socket is a four-tuple, sometimes with the protocol type becoming a five-tuple. If you are not familiar with what I’m talking about, you can check out my article: This Is What a Socket Is!
We know that the smallest storage unit on a disk is a sector. The operating system does not read sectors one by one because it is too inefficient, but reads in blocks, which are composed of multiple sectors.
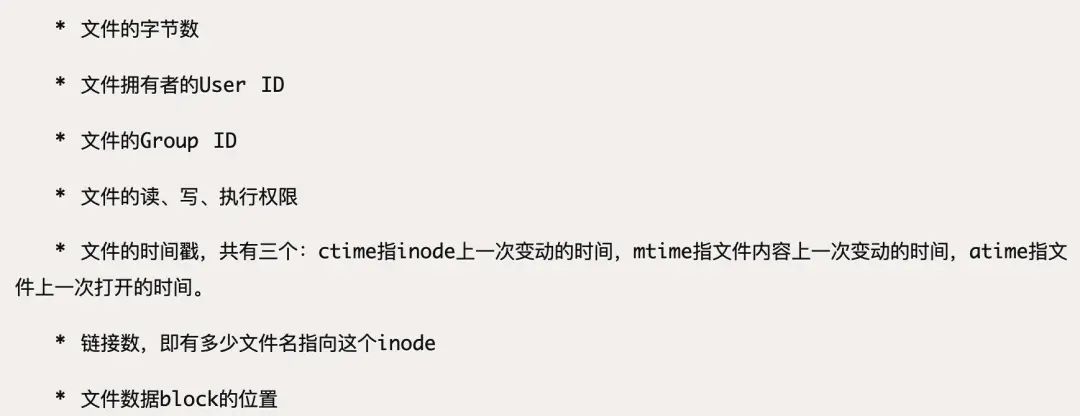
Data in files is stored in sectors, but we don’t know which block of data we need. To store some metadata about files, such as file creator, creation date, file size, developers proposed i-node, which is the index node. Generally, i-nodes contain the following content:
We will discuss the specific content of i-nodes later.
-
Then the third column indicates the owner of this file. As seen in the image, most files are owned by the root user.
-
The fourth column represents the group to which this file belongs. In the Linux system, your logged-in account will be added to one or more groups, and this column indicates the corresponding group permissions.
-
The fifth column indicates the file size, with the default unit being bytes.
-
The sixth column shows the date the file was created and the date of the most recent modification. From the image, you can see that this date format may not be what we want. To display the full date format, you can use ls -l –full-time, which includes the year, month, day, and time.
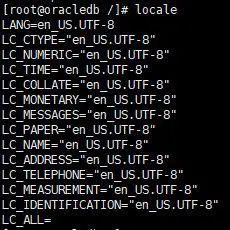
If you want to change the default locale to English, you can modify the system configuration file /etc/locale.conf. First, we can check which languages are supported by the system.
To change the default language, enter
vi /etc/profile
At the end of the document, enter
export LANG="en_US.UTF-8"
to switch to English. If you want to use Chinese, you can enter
export LANG="zh_CN.GB18030"
Then use esc + :wq to save. After saving, use
source /etc/profile
to complete the settings.
-
The seventh column is the file name. There is a special type of file name that indicates a hidden file. If the file name has a
.in front of it, it indicates a hidden file.
The Importance of Permissions
-
Provides system protection: Unauthorized users cannot operate functions and data with certain permissions.
-
Suitable for team development and data sharing: All team members and individuals can share projects.
If system permissions are not set appropriately, it may lead to data leaks or other serious consequences, so everyone should pay attention to permission issues. Next, let’s discuss how to set system permissions.
Changing System Permissions and Attributes
Now that we know the importance of file permissions for system security, let’s talk about how to modify file permissions. Common commands for modifying file permissions include:
-
chgrp: Change file group
-
chown: Change file owner
-
chmod: Change file permissions
chgrp
chgrp is short for change group. I think Linus has taken abbreviations to the extreme, which may be why abbreviations are so popular now. chgrp can change the file group, but to change the group, the group name must exist in the /etc/group file; otherwise, an error will be displayed.
chown
Since chgrp can change the file group, chown can change the file owner. It should also be noted that the file owner must be an existing account in the system, meaning the user name must be recorded in the /etc/passwd file. Additionally, chown can also directly modify the group name.
chmod
To change file permissions, the command is chmod. However, there are two ways to set permissions, which can be done using numbers or symbols.
-
Using numbers to change file permissions
Linux has 9 basic file permissions, which are the read/write/execute permissions for owner/group/others. These nine permissions are grouped into three. We can use numbers to represent each permission.
Generally, r represents 4; w represents 2; x represents 1. The permissions for each identity need to be summed up. For example, rwx represents 4 + 2 + 1 = 7. For instance, our most common chmod 777 grants all permissions, meaning anyone can read/write/execute, which poses significant security risks. Using numbers to change file permissions is the most common method.
-
Using symbols to change file permissions
The nine file permissions correspond to: (1) user (2) group (3) others, so we can use u, g, o to represent the permissions of the three identities. Additionally, a represents all identities.
For example, if we want to set permissions for -rwxr-xr-x, the command should be
chmod u=rwx,go=rx .filename
If we want to grant write permission to everyone, we can do this
chmod a+w .filename
If we want to remove write permission from everyone, we can write the command as follows
chmod a-w .filename
We have listed three commands: =, +, -; = indicates assigning specified permissions, + indicates adding permissions, and – indicates removing certain permissions. In the case of + and -, if the specified permission is not found, that permission will not change.
Linux Directory and File Permissions
We have discussed file permissions; files are places that contain data, including general text files, database files, binary files, etc. The significance of permissions for files is:
-
r (read): Can read the actual content of the file, such as reading the text content of a text file.
-
w (write): Can add, edit, or modify the content of the file (excluding deleting the file).
-
x (execute): Grants the file permission to be executed by the file system.
In Windows, the factor for determining whether a file can be executed is based on the file extension, such as .exe, .bat, .com, etc. However, in Linux, the determination of whether a file has executable permissions is based directly on whether it has the x permission, regardless of the file name.
However, in Linux, not only files have permissions, but directories also have permissions. Files are places that store actual data, while directories are lists that record the locations of files. We can only find out where files are located through directories! Permissions for different directories also represent different concepts.
-
r (read contents in directory): Indicates that you have permission to read the directory structure list. Therefore, if you have permission to read a directory, it means you can check the files under that directory, allowing you to use ls to display the contents of the directory.
-
w (modify contents of directory): Write permission indicates that you have the ability to modify files in the directory and the directory itself, mainly including:
-
Deleting existing files and directories.
-
Creating new files and directories.
-
Renaming existing files or directories.
-
Moving files and directories within the directory.
-
x (access directory):What’s the use of execute permission? Can’t directories also be executed?Actually, that’s not the case; execute permission indicates whether you have permission to enter the specified directory, i.e.,
cd(change directory).
Types of Files and Extensions in Linux
As everyone has probably heard, the saying goes: every device is a file in Linux, but files also come in various types. Besides the general files (-) and directory files (d) mentioned above, there are also the following file types:
-
Regular files: Regular files are the attributes shown when we use ls -al, which is the first character listed above.

File types can also be divided into:
-
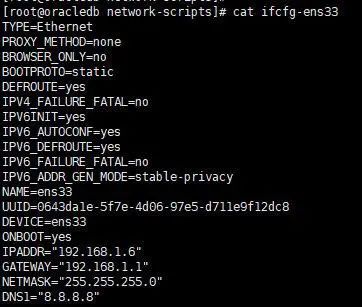
Plain text files (ASCII): This is the most common file type in Linux, and plain text files are the data we can see directly. You can use
catto directly see this content. For example, the file used to set the static IP in Linux, ens33, can be output using the cat command.
cat ifcfg-ens33
-
Binary files: In Linux, you can use
xxdorodto format and output binary files. -
Data format files: Reading data files directly with cat will show garbled text, but it can be output using the
lastcommand.
-
Directories: There’s nothing much to say; it just indicates a file list. The representation of directories is [d], which stands for directory.
-
Link files: Link files are a type of file that requires linking with certain programs to execute.
-
Device and device files: Devices in Linux are divided into two types: block devices and character devices:
Block devices are devices that can store fixed-size blocks of information and support reading and (optionally) writing data in fixed-size blocks, sectors, or clusters. Each block has its own physical address. The size of blocks is usually between 512 and 65536. All transmitted information is in continuous blocks. The basic feature of block devices is that each block is relatively independent and can be read and written independently. Common block devices include hard disks, Blu-ray discs, USB drives.
Block devices are generally located under /dev/sda, with the first attribute being [b].
The other type of I/O device is the character device. Character devices send or receive a stream of characters one character at a time, without considering any block structure. Common character devices include printers, network devices, mice, and most devices different from disks.

The biggest feature of character devices is that they read one character at a time and cannot truncate output. For example, you cannot make the mouse jump to another place at once; it must move smoothly.
The first attribute of character devices is [c].
-
Data interface files (sockets): Data interface files are used to receive network data via sockets, and their attribute is [s], usually found in directories like /run or /tmp.
-
Data transport files (FIFO, pipe): FIFO is also a special type of file, mainly aimed at solving errors caused by multiple programs accessing a file simultaneously. Its first attribute is [p].
Linux Extensions
Speaking of extensions can be quite troublesome; Linux does not have the concept of file extensions, but there are some naming conventions for extensions that make it awkward, so let’s call them extension types for now. The common ones include:
-
*.sh: This is an executable script or batch script, also known as a shell script, containing some shell syntax commands.
-
.tar, .tar.gz, .zip, *.tgz: These extension types are compressed files based on different packaging methods.
-
.html, .php: Web-related files, representing HTML and PHP syntax web files, respectively.