
I don’t know when it started, but learning programming has become a headache. On those late nights, I look up at the bright moon and wonder when I can fully grasp assembly language, becoming the dream of countless girls.
But reality always slaps you in the face….
There are many moments when I feel like smashing the keyboard, but we heroes will never waste time like that; can we learn just by smashing the keyboard? No, we can learn by watching Xue.
If you want to learn more about assembly language and binary vulnerabilities, don’t miss the excellent courses on Xue——
“In-Depth Guide to Assembly Language and Binary Vulnerabilities
This course, which has nearly 3000 students, let’s take a look together~!
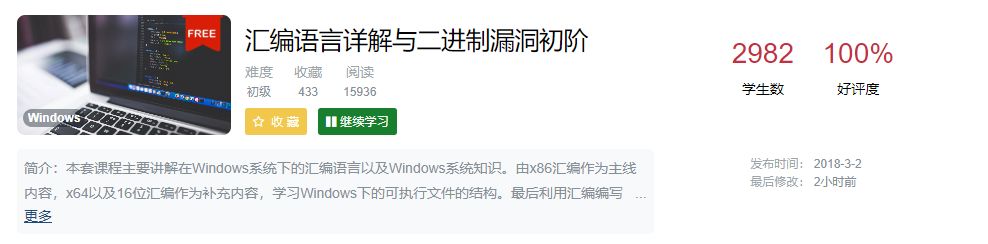
Instructor Introduction

Personal Skills: C/C++, Python, Assembly
Special Skills: Software Debugging, Reverse Engineering
Additional Skills: Teaching
Course Introduction
This course mainly explains assembly language and Windows system knowledge under the Windows system. It uses x86 assembly as the main content, with x64 and 16-bit assembly as supplementary content. It deeply understands the transition from real mode to protected mode. Learn the structure of executable files under Windows. Finally, it explains the techniques of writing shellcode under Windows using assembly, laying the foundation for future security learning.
Course Details
Chapter 1: Basic Knowledge
1.1 Preface and Environment Configuration
1.2 Number Systems and Base Conversion
Chapter 2: Preliminary Understanding of x86 Processor Architecture
2.1 Overview of this Chapter and General Architecture Concepts
2.2 32-bit x86 Processor
2.3 64-bit x86-64 Processor
2.4 John von Neumann
Chapter 3: Basic Syntax of Assembly Language
3.1 Seven Addressing Modes
Appendix: Experimental Environment
Preview
Experimental Environment v1.0
Appendix: Vulnerability Debugging
01. Stack Overflow Experiment – Nearby Variable Flooding
02. Stack Overflow Experiment – Using Flooding to Control Program Execution Flow
03. Stack Overflow Experiment – Initial Exploration of Shellcode
04. Stack Overflow Experiment – Introducing Jumping Board Technology
05. Shellcode Development Techniques in VS Environment – Environment Configuration
06. Shellcode Development Techniques in VS Environment – Eliminating Dependency on Absolute Addresses
……
 Click Read Original to learn for free~
Click Read Original to learn for free~
