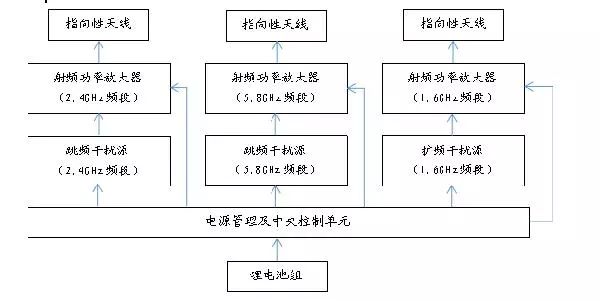
The device consists of a handheld main unit and a battery pack. The handheld main unit features an integrated design with a tri-band transmitter antenna, capable of simultaneously generating 2.4GHz/5.8GHz frequency drone control interference signals and satellite positioning interference signals. By blocking the uplink control channel and satellite positioning channel of the drone, it causes the drone to lose control commands and satellite positioning information, preventing normal flight. Depending on the drone’s design, this can result in return, landing, or crash control effects.
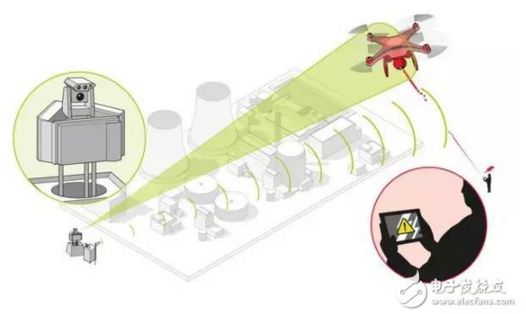
In an offensive and defensive situation, there is usually a certain distance between the drone operator and the sensitive area that needs protection. The drone takes off near the operator and gradually approaches the protected area. When the drone reaches the vicinity of the protected area and can effectively conduct reconnaissance or destructive activities, the distance from the drone to the protected area is usually much closer than its distance to the operator.
In this situation, all uplink signals sent by the operator (from the ground to the drone) will be relatively weak due to the greater distance. With the same power, the defender’s signals will be stronger as they are closer to the drone. The downlink signals received by the defender will also be stronger than those received by the operator. However, the goal of defending against downlink signals is to prevent the operator from receiving them, and at this point, the distance from the drone to the operator is roughly the same as that from the defender to the operator, so blocking downlink signals does not have a geographical advantage.
From the analysis above, it can be seen that interfering with uplink signals is more advantageous. Coincidentally, uplink signals are usually remote control signals, directly related to the control of the drone. If the uplink signal is interfered with, the drone will lose immediate control and can only operate according to pre-set steps (usually landing or hovering). Downlink signals mainly include telemetry and images, which may also contain sensitive information, but compared to control signals, they are less critical. Moreover, since the defender does not have a geographical advantage, they usually adopt a laissez-faire approach to downlink signals.
GPS relies on medium-earth orbit satellites. In simple terms, the signal travels thousands of kilometers to reach the Earth’s surface and is already very weak. Therefore, it is relatively easy to interfere with GPS signals when the drone is very close to the defender. If one wants to deceive it, more complex methods are needed to simulate GPS satellites, which is much more difficult.

Currently, the control of drones mainly uses radio communication technology. By transmitting high-power interference signals to the target drone, the control signals can be suppressed, forcing the drone to land or return automatically.
The United States utilizes this principle. This rifle has an electronic jammer installed in its frame. Once the trigger is pulled, the jammer emits interference signals across all frequency bands towards the drone, causing it to lose control from the operator and automatically land on the ground.
Once the drone’s signal is in a chaotic state, it typically has three choices: fall to the ground, return to the operator, or descend smoothly. The effective range of this rifle reaches 500 to 2000 meters.
Currently, under normal circumstances, the vast majority of consumer drones prioritize GPS navigation for flight control, and civilian GPS signals are unencrypted, leaving room for exploitation.
The main principle of GPS spoofing is to send false geographic coordinates to the drone’s control system, thereby manipulating the navigation system and inducing the drone to fly to the wrong location. GPS signals can be generated by a signal generator or can be pre-recorded and then replayed. Since the drone receives GPS signals based on the strongest signal source, as long as the ground-based artificial GPS signal is strong enough, it can cover the genuine GPS signals coming from space, thus deceiving the drone’s GPS receiver module.
Currently, various countries have established no-fly zones in core areas, and many drone manufacturers have set up restrictions in the firmware of drones, preventing them from taking off within these zones. Even if they reach a no-fly zone, they will automatically land. Therefore, as long as the ground-based artificial GPS signal simulates the coordinates of the no-fly zone, it can force the drone to land automatically.

Now, the control signals used by drones are mostly in conventional civilian frequency bands such as 1.2GHz, 2.4GHz, and 5.8GHz. With the rapid development of open-source hardware like Arduino and Raspberry Pi, as well as the popularity of software-defined radio (SDR) technology, ordinary enthusiasts can use hardware purchased online and software source code obtained from forums to simulate remote controllers to send control signals to drones, thereby overriding the signals from genuine remote controllers and gaining control of the drones.
Many drones allow users to control them using mobile devices like smartphones and tablets, directly using Wi-Fi for interaction. This way, some well-established hacking techniques available on the internet can be directly applied to drones.
For instance, by exploiting open ports in the drone control system or using password guessing techniques, one can gain access to the control system and take control of the drone. The legendary hacker Samy Kamkar, who developed the “Samy Worm Virus,” utilized this principle to create a drone hijacking software called “SkyJack,” which he installed on a specially configured drone. SkyJack flies in the air and searches for other drones within Wi-Fi range, then hijacks those drones and takes control.
Professionals engaged in anti-drone applications in the industry indicate that current domestic anti-drone technology is still in the exploratory stage. Radio hijacking technology is difficult to implement due to the encryption of radio signals by various drone manufacturers, and hacking techniques are challenging to commercialize due to high barriers to entry. Therefore, the technology currently employed mainly focuses on interference and disruption.
This is a serious dividing line
For purchase, please click here



Typesetting|Lala
Source|Electronic Enthusiast Network
AOPA, it’s more exciting with you
Long press the QR code to follow us