Introduction
This article covers the basics of the TCP/IP protocol, focusing on the content, functions of the TCP/IP protocol suite, and foundational knowledge related to the three common network protocols: TCP, UDP, and IP.
Content
The TCP/IP protocol suite is developed from the OSI seven-layer model. The existence of the OSI reference model has the following benefits:1. Solving interoperability issues among devices from different vendors: compatibility considerations;2. Strong independence of hierarchical structures; high scalability;3. Unified standards facilitate learning;
TCP/IP ModelThe relationship between the TCP/IP model and the OSI model is shown in the following diagram: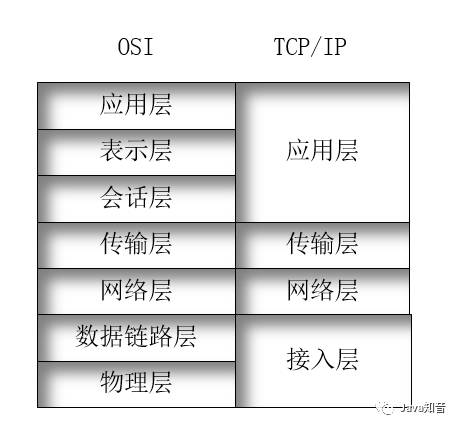
Notes
1. Application Layer: Corresponds to the application layer, presentation layer, and session layer of the OSI model, primarily providing an interface for user applications to access the network;2. Transport Layer: Also known as the host-to-host layer, corresponds to the transport layer of the OSI model, specifies the control protocols for the network layer, defines whether the data transfer method is TCP or UDP, and establishes an end-to-end connection between two devices; both the transport layer and data link layer define flow control and error control mechanisms, with the distinction that the data link layer protocol emphasizes controlling the flow on the data link, i.e., the physical medium connecting two devices, while the transport layer controls the flow on the logical link, i.e., the end-to-end connection between two devices, which may span a series of data links;3. Network Layer: Defines the packet format and address format, primarily responsible for IP addressing and routing;4. Access Layer: Includes the data link layer and physical layer, where the data link layer defines how to access and share the medium, how to identify devices on the medium, i.e., layer 2 addressing (MAC address), and how to frame data before sending it over the medium. Common layer 2 protocols include Ethernet, PPP, HDLC, Frame Relay, ATM, etc.; the physical layer defines protocols related to the physical medium, i.e., electronic/optical protocols (voltage, light intensity, encoding, signal waveform), mechanical protocols (size, metal composition of wires), functional protocols (describing what to do), and procedural protocols (describing how to do it, e.g., 1 indicates voltage less than -3V).
TCP Protocol
Explanation
The Transmission Control Protocol (TCP): is a reliable, connection-oriented service. It provides a point-to-point-like connection.
Mechanism
1. Marks packets using sequence numbers;2. Provides reliability using acknowledgment, checksums, and timers, along with retransmission mechanisms;3. The sliding window mechanism adjusts the flow of packets: reducing the likelihood of packet loss due to the receiver’s buffer being full.
Packet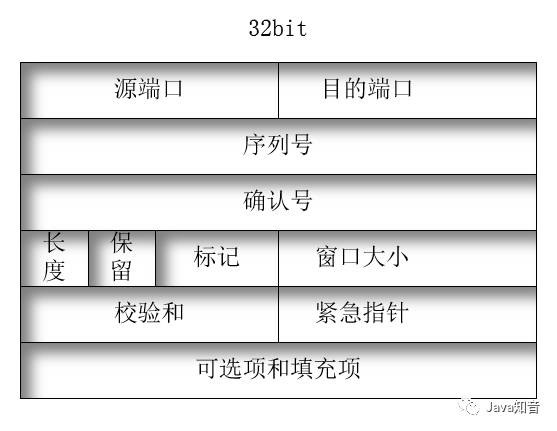
Notes
1. Source and Destination Ports: Each 16 bits long, specifying the source and destination applications for the encapsulated data; the combination of the application’s port number and the IP address of the host where the application resides is called a socket. The socket uniquely identifies each application on the network.(Supplement: Common port numbers corresponding to services: FTP: TCP21; TELNET: TCP23; SMTP: TCP25; BGP: TCP179; DNS: TCP/UDP53; TFTP: UDP69; SNMP: UDP161; RIP: UDP520;)2. Sequence Number: 32 bits long, indicates the position of the encapsulated data in the data stream sent by the sender;3. Acknowledgment Number: 32 bits long, indicates the next expected sequence number from the target, implicitly acknowledging receipt of the previous packet with that number;4. Header Length: 4 bits long, specifies the header length in units of 32-bit words.5. Reserved: 4 bits long, usually set to 0;6. Flags: 8 bits, used for flow and connection control. From left to right: CWR, ECE, URG, ACK, PSH, RST, SYN, FIN;7. Window Size: 16 bits long, primarily used for flow control. The window size indicates the size of the receiver’s buffer;8. Checksum: 16 bits long, checks the header and encapsulated data;9. Urgent Pointer: Used only when the URG flag is set. 16 bits added to the sequence number to indicate the end of urgent data;10. Options: Used to specify options requested by the TCP sending process; a common option is the maximum segment size, which notifies the receiver of the maximum segment size the sender is willing to receive, using 0 to pad the remaining part of this field to ensure the length of the packet is a multiple of 32 octets.
UDP Protocol
Explanation
User Datagram Protocol (UDP): is a connectionless, best-effort data forwarding service.
Advantages
Does not spend time establishing a connection, directly sends data, which means lower overhead, allowing applications that send small amounts of data to achieve better performance advantages.
Packet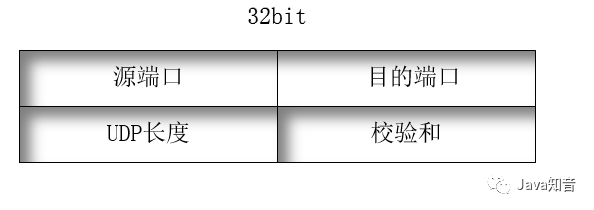
Notes
1. Source and Destination Ports: Each 16 bits long, specifying the source and destination applications for the encapsulated data;2. UDP Length: The total length of the entire segment in octets; includes the total length of the data segment;3. Checksum: 16 bits long, the checksum is an optional field, and if not used, it is all set to 0.
IP Protocol
Explanation
IP: The most common network layer protocol, is an unreliable, best-effort forwarding service that can work with layer 4 and layer 2 to ensure reliable data transmission;
IP Addressing
1. The length of the IP address is 32 bits, represented in dotted decimal notation, used to identify the logical address of the device; IPV4 addresses consist of a network number and a host number, where the network number uniquely identifies a physical or logical link, and the host number uniquely identifies the specific device connected to that link. This hierarchical address design helps in quick lookup, easy maintenance, and address conservation;Supplement: Subnet Mask: All network bits are 1, all host bits are 0, composed of continuous 1s and continuous 0s.Broadcast Address: The network bits remain unchanged, and all host bits are 1.Network Number: The network bits remain unchanged, and all host bits are 0.2. IPV4 Address Classes:Class A: The first bit is fixed at 0, ranging from 1 to 126, subnet mask 255.0.0.0;Class B: The first two bits are fixed at 10, ranging from 128 to 191, subnet mask 255.255.0.0;Class C: The first three bits are fixed at 110, ranging from 192 to 223, subnet mask 255.255.255.0;Class D Address: The first four bits are fixed at 1110, ranging from 224 to 239, multicast address, no subnet mask;Class E Address: The first four bits are fixed at 11110, ranging from 240 to 255, reserved for research and reserved.Special Addresses: Unusable addresses, including: local loopback address: 127.0.0.1; local link address: starting with 169.254, subnet mask is 255.255.0.0; network address: the address where the network bits remain unchanged and all host bits are 0; broadcast address: where the network bits remain unchanged and all host bits are 1, can be transmitted on layer 3 devices (routers); limited broadcast address: where both network and host bits are all 1, i.e., 255.255.255.255, terminating at layer 3 devices (routers).Private Addresses: Certain addresses are extracted from public addresses as private addresses, which will not be allocated and cannot be used on the network; for communication on the network, NAT must be used to convert private addresses to public addresses;Class A private address: 10.0.0.0 to 10.255.255.255;Class B private address: 172.16.0.0 to 172.31.255.255;Class C private address: 192.168.0.0 to 192.168.255.0;3. Subnetting and SupernettingSubnetting: Variable-length subnet mask division beyond the main class network; method of use: borrowing bits;Supernetting: Aggregating multiple network addresses into one network address; method: taking the same bits, discarding different bits;
Packet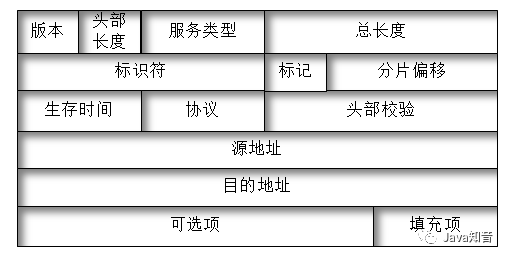
Notes
1. Version: 4 bits, 0100 indicates IPV4, 0110 indicates IPV6.2. Header Length: 4 bits, indicating the length of the IP header in 32-bit words. The minimum length of an IP packet is 20 bytes, and it can be extended to a maximum of 60 bytes (15*4);3. Type of Service TOS: DSCP 6 bits + ECN 2 bits. The 6-bit DSCP can define up to 64 different service classes, and ECN=11 indicates congestion indication. The TOS field in the IP header is reserved and generally used in QOS to set the priority of packets;4. Total Length: 16 bits, the total length of the IP packet minus the IP header length determines the size of the data payload. The maximum length of an IP packet is 65535;5. Identifier: 16 bits in length, usually used together with the flags and fragment offset fields for packet segmentation. If the original length of the packet exceeds the maximum transmission unit of the data link it will pass through, packet fragmentation is required. The device will mark each fragment of the packet with the same identifier so that the receiving device can identify the segments belonging to one packet;6. Flags: 3 bits long, reserved bits, don’t fragment bit (DF), more fragments bit (MF); if DF=1, it indicates that the router cannot fragment the packet; MF=0 indicates the last fragment of the packet;7. Fragment Offset: 13 bits long, in units of 8 octets, used to indicate the starting point of the fragment relative to the start of the packet, allowing the receiver to reassemble the packet in the correct order;8. Time to Live (TTL): 8 bits long, when the packet is transmitted through routers, TTL decreases by 1. When TTL=0, the router will discard the packet and send an error report to the source. This method prevents packets from being transmitted indefinitely. The default is recommended to be 64; you can use the traceroute command to see the routers the packet passes through during transmission;9. Protocol: 8 bits long, specifies the type of information in the packet. Common protocol numbers: 1-ICMP; 6-TCP; 17-UDP; 47-GRE; 88-EIGRP; 89-OSPF;10. Header Checksum: 16 bits long, does not include the encapsulated data part. Because TTL decreases during transmission, each router must recalculate the checksum;11. Source and Destination Addresses: 32-bit IP addresses;12. Options: Variable-length fields, including information generated by the source and information added by other routers, commonly used for testing. Common optional fields include: loose source routing, strict source routing, record route, timestamp;13. Padding: Added 0s to the end of the optional field to ensure the header length is a multiple of 32 bits;
Recommended Reading
-
“TCP/IP Routing Technology Volume 1”
Source: Blog Garden
Link: http://www.cnblogs.com/zhaoyujiao/p/4906518.html
Recommended Reading
Spring Boot Series Tutorial Learning
Java Web Practice Project Source Code Download
Selected Java Web Related Video Tutorials
100 Sets of IT Resume Templates Download

