1. What Is the Task State Machine Model?
The task state machine model describes the lifecycle and state transitions of a task. Typical states include:
(1) Ready: The task can execute but is waiting for the scheduler to allocate CPU.
(2) Running: The task is currently using the CPU to execute.
(3) Blocked: The task is waiting for an event (such as a semaphore or message queue) to occur.
(4) Suspended: The task is suspended and will not be scheduled.
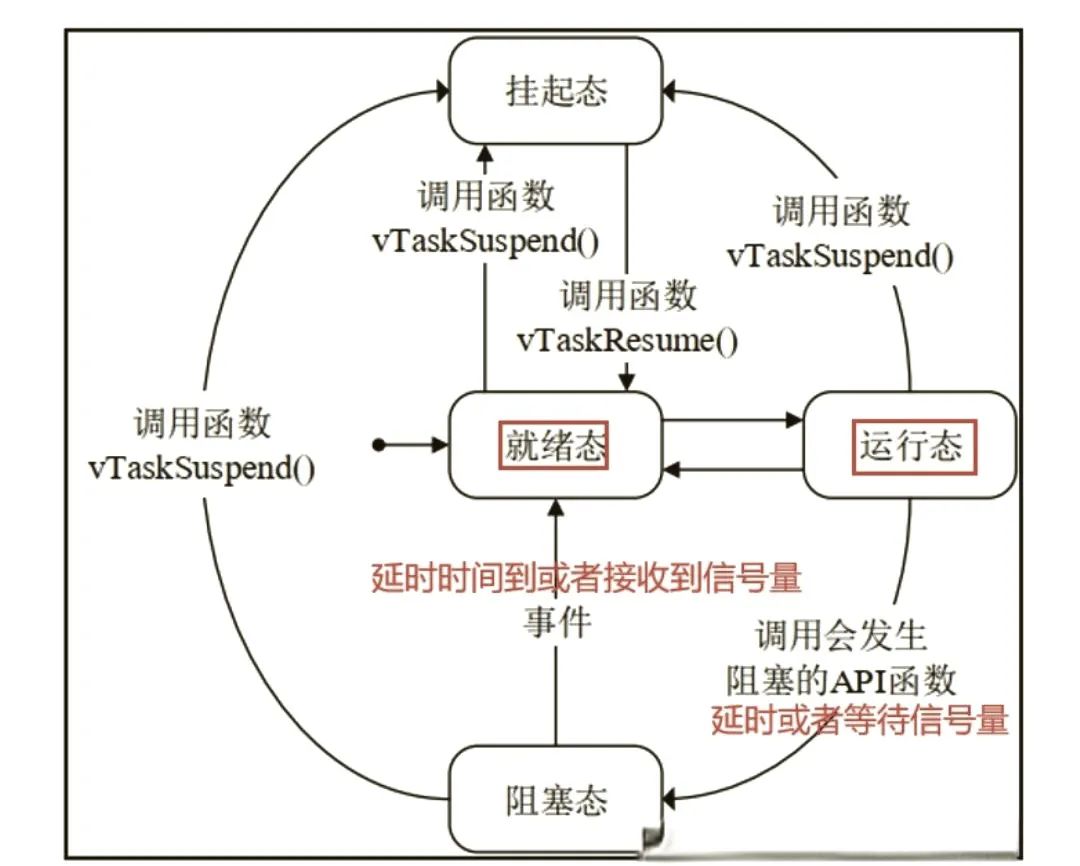
The transitions between states are controlled by the scheduler based on the changes in the task’s state.
2. How Does RTOS Manage Task Stacks?
(1) Stack Creation Static Allocation: In some RTOS, developers can statically define the size and location of the task stack before compilation. For example, in uC/OS-II, a fixed-size stack space can be allocated for each task by defining an array, and the task will use the pre-allocated stack area upon system startup. Dynamic Allocation: Some RTOS support dynamically allocating stack space when creating tasks. In FreeRTOS, when using the xTaskCreate() function to create a task, the stack size can be specified, and the system will allocate the corresponding stack space in the heap memory, allowing for more flexible resource allocation based on the actual needs of the task.
(2) Stack Initialization Setting the Stack Pointer: After a task is created, RTOS initializes the task stack, with the critical step being the setting of the stack pointer (SP). Typically, the stack pointer is set to the end address of the stack, allowing the stack to grow from high to low addresses, or vice versa, depending on the hardware architecture and RTOS design. Filling Initial Values: Some RTOS may fill the stack area with specific initial values, such as 0xAA or 0x55, to facilitate debugging by checking if the stack is correctly used. If a non-initial value area is found, it may indicate a stack overflow or other anomalies.
(3) Stack Usage Managing Task Switching Protection: When RTOS performs task switching, it saves the current task’s registers and other context information into its task stack, then restores the context information of the task that is about to run. For example, in RTOS running on ARM Cortex-M series chips, PUSH and POP instructions are used to save and restore registers, ensuring the task can continue executing correctly after switching. Function Calls and Returns: During task execution, function calls push return addresses and other information onto the stack, which are popped off when the function returns. RTOS must ensure there is enough stack space to handle these operations to avoid stack overflow leading to system errors.
(4) Stack Overflow Detection Hardware-Assisted Detection: Some hardware platforms provide stack overflow detection mechanisms, such as chips with stack pointer boundary checking features. When the stack pointer exceeds the preset boundary, an exception is triggered, and RTOS can handle the error in the exception handling function, such as logging the error or resetting the task. Software Detection Methods: RTOS can set protection data at the boundaries of the task stack and periodically check if the protection data has been modified during task execution. If the protection data is corrupted, it indicates a potential stack overflow. For example, FreeRTOS’s configCHECK_FOR_STACK_OVERFLOW configuration option can enable stack overflow detection functionality.
(5) Stack Optimization Adjusting Size Based on Task Needs: RTOS can dynamically adjust the task stack size based on the actual usage of the stack by the task. For example, by analyzing the function call depth and local variable usage during task execution, if it is found that a task’s stack usage rate is consistently low, its stack size can be appropriately reduced to save memory resources. Memory Fragmentation Management: For RTOS that dynamically allocate stacks, effective management of memory fragmentation is crucial to avoid performance degradation caused by frequent stack allocation and deallocation. Suitable memory allocation algorithms, such as buddy system or SLAB allocation algorithms, can be employed.
3. What Is Context Switching?
Context switching refers to the process where the operating system pauses the currently executing task, saves its current execution state (context), and then loads the context of another task to begin execution. Through this method, the operating system can create the effect of multiple tasks running concurrently, providing users with multitasking capabilities.
4. What Is Time-Slice Round-Robin Scheduling?
The time-slice round-robin scheduling algorithm divides the CPU time into fixed-length time slices, with each process taking turns to occupy the CPU for a time slice to execute tasks. When the time slice expires, regardless of whether the current process has completed its task, the operating system pauses the execution of that process and allocates the CPU to the next process in the ready queue, allowing it to execute for a time slice. This cycle continues, enabling all ready processes to gain a certain amount of CPU time to advance their execution.
5. How Do Tasks Share Data?
In embedded systems or multitasking operating systems, there are several ways for tasks to share data. Here are some common methods: (1) Global Variables: Define global variables that multiple tasks can access and modify. For example, in C language, define an integer variable global_var outside of functions, which can be read and written by various task functions. (2) Message Queues: Tasks can encapsulate data into messages and send them to a message queue, from which other tasks can read messages to obtain data. For example, in FreeRTOS, the xQueueSend() function can be used to send messages, and the xQueueReceive() function can be used to receive messages. (3) Shared Memory: Multiple tasks can access the same memory region to share data. In some operating systems, specific functions can be used to map a segment of physical memory to the address space of multiple tasks, such as using the mmap() function in Linux systems. (4) Semaphores: Semaphores are primarily used to control access to shared resources. A binary semaphore can be created for mutual exclusion access to shared data, where a task must acquire the semaphore before accessing the data and release it afterward. For example, in uC/OS-II, use OSSemPend() to acquire the semaphore and OSSemPost() to release it.
(5) Mailboxes: A mailbox is a special type of message queue typically used to transmit small amounts of critical data or notification information. One task can send data or messages to the mailbox, and another task can read from the mailbox. In some RTOS, there are dedicated mailbox operation functions OSMboxPost() and OSMboxPend().