Authorization is a security mechanism that determines whether to allow users, devices, or applications to access specific resources, operations, or information based on their identity and permissions. In computer systems, networks, web applications, and other environments that require protection of sensitive data and resources, authorization is a key measure for ensuring security and implementing access control.
Authorization is crucial for system security in the following aspects:
-
Data Security: Authorization can prevent unauthorized access to sensitive data. By implementing access control, only authorized users or entities can view, modify, or delete sensitive information.
-
Prevent Unauthorized Operations: Authorization ensures that users can only perform operations they are explicitly allowed to do. This prevents unauthorized users from carrying out malicious actions or interfering with critical business processes.
-
Privacy Protection: In applications and systems that store personal or sensitive information, authorization ensures that only authorized personnel can access and process that data, protecting user privacy.
-
Resource Protection: Authorization helps prevent unauthorized individuals from accessing valuable resources such as files, databases, devices, or services. Unauthorized access to these resources can lead to data breaches, system damage, or service interruptions.
-
Compliance and Regulatory Requirements: Many industries and fields have strict compliance and regulatory requirements for data protection and access control. Proper authorization mechanisms help organizations meet these requirements and avoid legal liabilities.
-
Business Logic Execution: Authorization allows organizations to enforce business rules and logic by controlling access to specific functions within applications or systems.
-
Limiting Damage from Account Compromise: If an account is compromised, proper authorization can limit the actions an attacker can perform, thereby reducing potential damage.
-
Multi-Tenancy Support: In multi-tenant environments, authorization helps ensure that each tenant can only access and manage their own data and resources without affecting other tenants’ data.
-
Scalability and User Management: Authorization systems can centrally control access for a large number of users and resources, simplifying user management and access control administration.
Overall, authorization is essential for ensuring the confidentiality, integrity, and availability of data and resources within an organization’s infrastructure. It ensures that only verified and authorized entities can access specific resources and perform actions permitted by their roles or permissions.
The Difference Between Authentication and Authorization
Before we delve into Access Control Lists (ACL), it is important to clarify the difference between authorization and authentication. Authentication refers to the process of verifying the identity of a user or system. This is typically achieved through usernames and passwords, but can also involve biometrics or other methods. Authorization, on the other hand, refers to the process of determining what actions a user or system is allowed to perform. Authorization is usually based on the user’s role or group membership.
Common Authorization Methods
The following are standard authorization methods used to control resource access in computer systems and web applications. These methods help ensure that only authorized users or entities can perform specific operations or access certain information:
-
Role-Based Access Control (RBAC): RBAC is a commonly used authorization method that assigns access permissions to specific roles, which are then assigned to users based on their job functions or responsibilities. This allows users to access resources based on their assigned roles, facilitating large-scale permission management.
-
Attribute-Based Access Control (ABAC): ABAC is a more granular authorization method that considers multiple attributes or characteristics of users, resources, and the environment when making access control decisions. These attributes include the user’s role, location, access time, and user-defined factors.
-
Discretionary Access Control (DAC): DAC is a simple authorization model where the owner of each resource can decide who can access their resources and at what access level. This method allows users to flexibly control access to their files and directories.
-
Mandatory Access Control (MAC): MAC is a stricter authorization model typically used in high-security environments. Access decisions are based on system-level policies set by administrators, and users cannot change access permissions. This model is often applied in government and military institutions.
-
Rule-Based Access Control: This method uses if-then statements to explicitly define access control rules. These rules specify which users or entities can access which resources or perform which operations.
-
XACML (eXtensible Access Control Markup Language): XACML is an authorization standard that uses ABAC principles to define attribute-based access control policies. It provides a standardized way to express complex access control decisions.
-
OAuth: OAuth is a widely used authorization framework that allows third-party applications to gain limited access to user resources on a server without exposing user credentials. It is commonly used for authorization in modern web and mobile applications.
-
OpenID Connect: OpenID Connect is an authentication and authorization protocol based on OAuth 2.0. It allows applications to authenticate users and obtain basic user information while delegating user authentication to identity providers.
-
JSON Web Token (JWT): JWT transmits authorization information between parties in a compact, self-contained way using JSON objects. JWT is widely adopted in modern web applications, enabling stateless authentication and authorization mechanisms.
-
Biometric Authorization: This method uses biometric features (such as fingerprints or facial recognition) to grant access to specific resources or operations.
It is important to note that the authorization methods used may vary based on the specific needs and security requirements of the system or application.
What is ACL?
An Access Control List (ACL) is a specific implementation of the discretionary access control model that determines which users or groups can access a resource in what manner based on a set of rules associated with each resource.
In an access control list, each resource (such as files, directories, network devices, etc.) has a corresponding list that specifies the access permissions for different users or groups. Access permissions typically include operations such as read, write, execute, and delete.
Managing Access to MQTT Messages Using ACL
In the context of MQTT (Message Queue Telemetry Transport), access control lists are used to control access to various topics and operations within the MQTT Broker. MQTT is a lightweight messaging protocol commonly used in IoT applications and other messaging scenarios. MQTT employs a publish/subscribe model, which differs from the traditional client/server model. It separates the client sending messages (the publisher) from the client receiving messages (the subscriber), eliminating the need for a direct connection between publishers and subscribers.
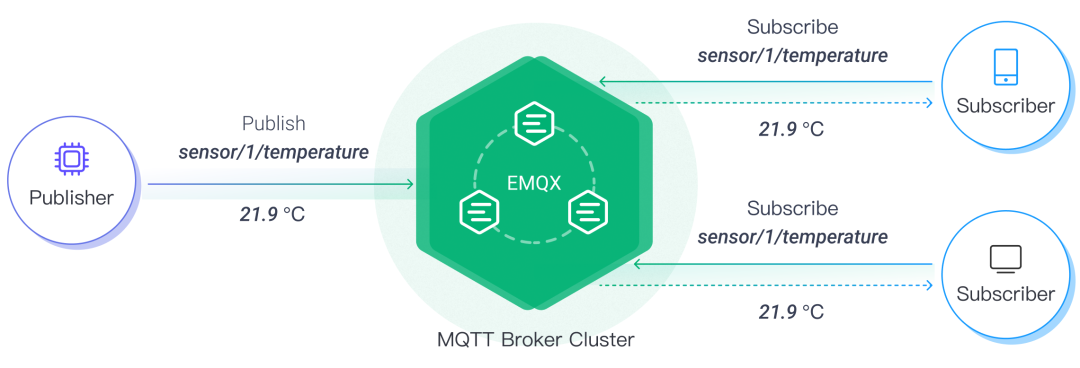
Example of the EMQX MQTT Broker’s Publish/Subscribe Model
The MQTT Broker uses ACLs to ensure security and restrict access to specific topics based on rules. ACLs specify which clients can publish messages to which topics and which clients can subscribe to which topics. By setting ACLs, the MQTT Broker can ensure that only authorized devices or clients can publish and subscribe to specific topics, thereby creating a controlled communication environment.
Key Components of MQTT ACL
-
Topic Patterns: MQTT topic names are hierarchical, and ACLs can use wildcards to define patterns applicable to multiple topics. The two common wildcards in MQTT are the plus sign (+) and the hash sign (#). The plus sign represents one level in the hierarchy, while the hash sign represents any number of levels (including zero levels).
-
Client Identifiers: When MQTT clients connect to the Broker, they must provide a unique client identifier. ACLs can use these identifiers to determine which clients are authorized to perform which operations.
-
Operation Permissions: MQTT ACLs specify the allowed operations for each client on specific topics. Operation permissions include PUBLISH (sending messages) and SUBSCRIBE (receiving messages).
Examples of MQTT ACL Rules
-
Allow the client with identifier “sensor001” to publish messages to the topic “sensors/temperature”:
allow client sensor001 to publish to sensors/temperature2. Allow all clients to subscribe to any topic under the “sensors” topic hierarchy:
allow all clients to subscribe to sensors/#3. Deny the client with identifier “guest123” from subscribing to any topic:
deny client guest123 to subscribe to #Conclusion
Access control lists are very important for IoT systems. They provide a method for managing resource access, ensuring that only authenticated and authorized users can access restricted data. It is important to note that different MQTT Brokers may have different implementations of ACLs, and the syntax and functionality of ACL configurations may vary depending on the MQTT Broker.
Properly configuring MQTT ACLs is critical for ensuring security and maintaining orderly MQTT communication. You can read more to explore how EMQX protects your IoT infrastructure:
-
Overview of EMQX Access Control https://www.emqx.io/docs/zh/v5.0/access-control/overview.html
-
Using Redis and JWT Auth & ACL on EMQX Cloud

Click “Read the original article” to learn more