In previous articles, we briefly discussed asymmetric encryption, which involves splitting a key into two parts: one part is kept private, known as the private key, while the other part can be publicly shared, known as the public key.
The encryption algorithm ensures that data encrypted with one key can only be decrypted with the other key (including the key used for encryption). The reverse is also true.
Today, we will discuss the applications of this algorithm, temporarily concluding this series of articles.
In simple terms, asymmetric encryption (public key/private key encryption) is widely used in modern information security due to its unique security features (public key is public, private key is confidential).
01 Secure Communication and Data Transmission
In fact, this is the most fundamental application of any encryption algorithm—ensuring the security of data during transmission, preventing unauthorized eavesdropping.
For example, if I want to send my bank card number and password over the internet, without proper encryption measures, if a malicious person is eavesdropping on my network, my data security would be compromised.
Asymmetric encryption solves this problem—by using asymmetric encryption, a secure channel can be established between a personal computer and the server for the first communication, preventing unauthorized eavesdropping and effectively ensuring the security of data transmission. This is the cornerstone of technologies such as online shopping and online finance.
Common usage scenarios include the following:
a HTTPS/SSL/TLS and other secure browsing
Friends who frequently browse the internet must be familiar with HTTPS.
For instance, when we enter certain websites, we see ‘Https’ and a small lock icon in the address bar, indicating that communication with the website is protected by the HTTPS (HyperText Transfer Protocol Secure) protocol, preventing eavesdropping. (There is also a signature to ensure the website’s credibility, which I will discuss later.)
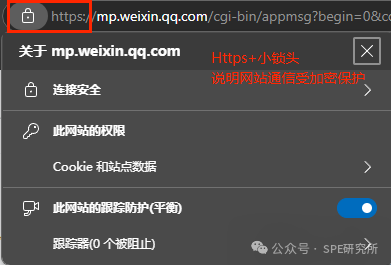
Generally speaking, HTTPS actually uses multiple encryption algorithms to achieve confidentiality during communication, such as key exchange algorithms, symmetric encryption algorithms, hash algorithms, and digital signature algorithms. Some of these algorithms utilize asymmetric keys, such as digital signatures.
b SSH (Secure SHell)
Those who play with Linux should be familiar with this.
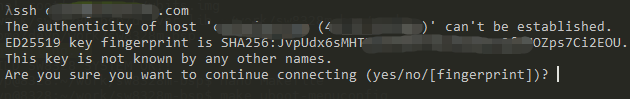
SSH, or Secure SHell, is a secure remote login protocol commonly used for remote login to the command line interface of Linux systems.
The common method is for the client to sign with the private key, and the server verifies the identity with the public key. During transmission, the data is also encrypted to prevent information leakage.
c End-to-End Encrypted Communication
In fact, some end-to-end encrypted communications also use asymmetric encryption algorithms to ensure the security of message transmission, which I will not elaborate on here.
02 Digital Signatures
Another use of asymmetric encryption is for digital signatures.
First, let’s briefly explain what a digital signature is.
In previous articles, we discussed that one characteristic of asymmetric keys is the separation of public and private keys. Information encrypted with the public key must be decrypted with the corresponding private key. Conversely, information encrypted with the private key must be decrypted with the corresponding public key. Now, let’s imagine a scenario:
Suppose A encrypts a file with their private key and sends it to recipient B. When B receives the file, they use A’s public key to decrypt it.
If the file can be decrypted and opened normally, it indicates that the file has not been modified during transmission and indeed comes from A.
If the file cannot be decrypted with A’s public key, it indicates that someone modified the file and encrypted it with a different key; or someone sent the file using A’s identity, making the file untrustworthy.
This method of encrypting with the private key and verifying with the public key is known as a digital signature.
Common usage scenarios include:
a Software/Document Signing
Similar to the example above, the most common usage scenario for digital signatures is signing software and documents for users.
The common practice is for developers to sign the hash value of the software with their private key, and users verify the source and integrity using the public key (such as Microsoft driver signatures, npm package signatures, and APK signatures).
Of course, some smartphone manufacturers also perform similar processing on their ROM packages, such as signing the ROM before release, and checking the signature during the internal Fastboot flashing process to prevent unauthorized installation of third-party firmware or harmful firmware.
Additionally, signature verification can also be performed on firmware or kernel modules to prevent the loading and tampering of malicious code.
b Digital Certificates (PKI System)
A common usage is that a Certificate Authority (CA) issues digital certificates using its private key, binding the entity’s identity to the public key, and browsers verify the legitimacy of the website’s certificate using the CA’s public key.
In this case, the CA acts as a guarantor, ensuring that the public key obtained from here indeed comes from the corresponding entity organization (such as a company).
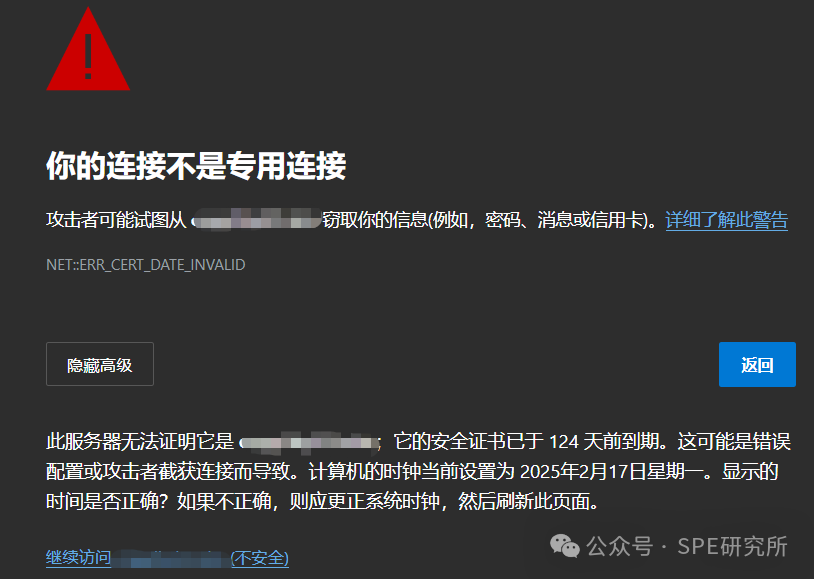
If there is an issue with the certificate while browsing the web (such as untrusted source, expired certificate, etc.), an error message will appear, similar to this (I used an example of my own website that I forgot to update the certificate for):
03 Conclusion
In addition, asymmetric encryption has many other applications, such as encrypting files, securely transmitting files, conducting currency transactions, and multi-party computations.
The advantages of asymmetric encryption are as follows:
- Simplified key management: Communication parties do not need to share keys in advance.
- Non-repudiation: Private key signatures ensure actions are traceable.
- Trust chain construction: Extends to large-scale networks through the PKI system.
In practical use, asymmetric encryption is often combined with symmetric encryption to balance security and efficiency, forming the cornerstone of modern digital trust systems.
Of course, encryption algorithms and decryption algorithms always complement each other. With such algorithms, there will naturally be more attack methods, such as man-in-the-middle attacks, etc.
However, these attack methods will further promote the development and application of encryption methods. The advancement of these technologies will bring more changes to our lives.
This article ends here~~
About Me:
This public account focuses on programming, photography, and the geek world.
The author is an ordinary person who loves various technologies and is also interested in various interesting gadgets and cats.
I share some strange geek gadget reviews, programming design ideas, photography-related knowledge, and some quirky trivia from time to time (and of course, cats).
If you are interested in my articles, please follow.
And don’t hesitate to like and share, thank you!!