This article is a submission from a friend, Han Shijun. If you have excellent articles you would like to submit, feel free to contact me.
Everyone relies on network communication every day, but how do these devices communicate with each other? I wrote this article so you can read it from thousands of miles away. Today, I will briefly discuss communication protocols.
Network Communication Protocols
Network communication protocols mainly establish standards for information transmission rates, transmission codes, code structures, transmission control steps, error control, and more.
Protocols are mainly composed of the following three parts:
-
Semantics: Required control information and actions to be executed
-
Syntax: The format and structure of exchanged data or control information
-
Timing: The response relationship between parties, including speed matching and order
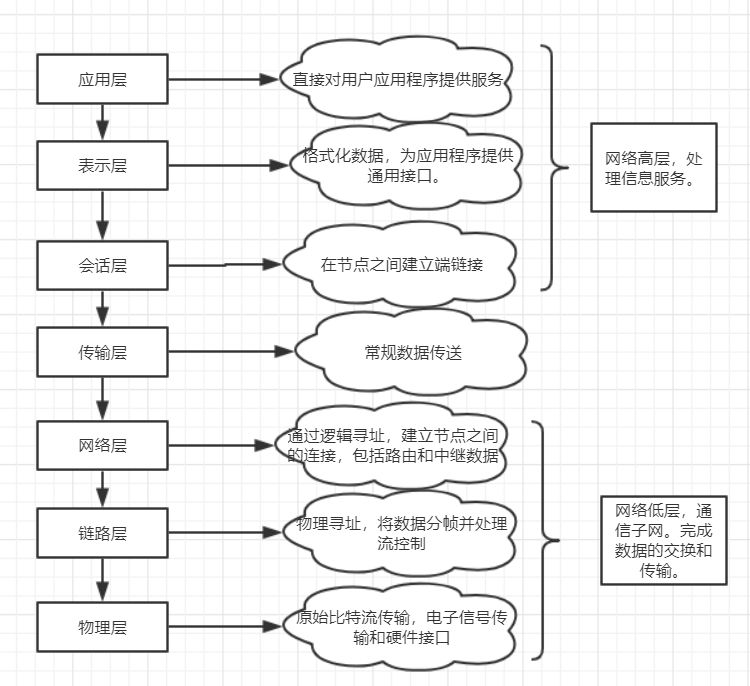
OSI Reference Model
The OSI model is not a standard; rather, it is an abstract reference model that does not provide any specific implementation standards. Most existing networks can be analyzed using the OSI model, and understanding the OSI model helps in analyzing and managing networks.
The OSI model is a layered structure with seven layers:
TCP/IP Protocol Suite
Introduction
The TCP/IP protocol suite was developed before the OSI reference model, so its layers do not completely correspond to the OSI model. It integrates different communication functions into different network layers, forming a four-layer architecture.
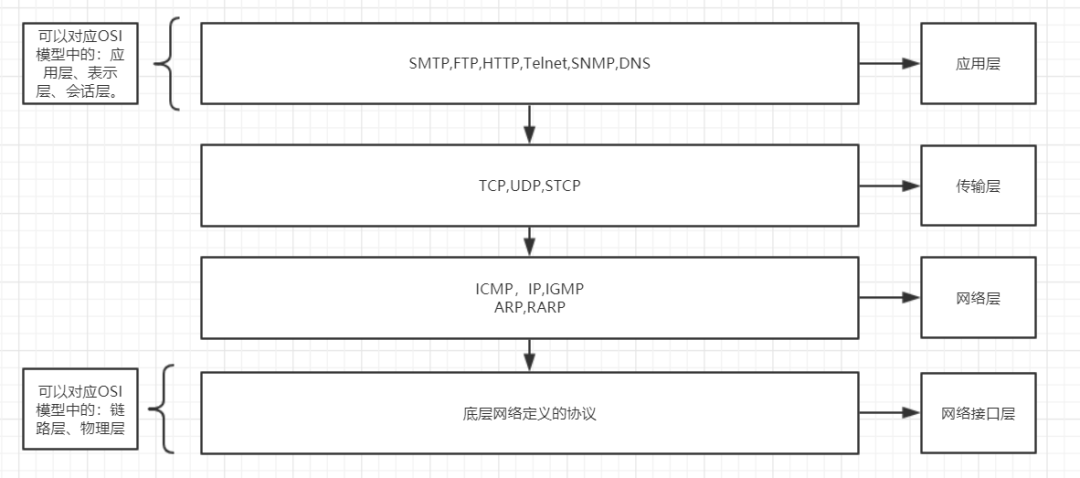
Some also divide it into five layers, separating the link layer from the network interface layer.
Responsibilities of Each Layer
-
Network Interface Layer: Primarily responsible for sending/receiving data packets to/from the physical network medium. Since TCP/IP does not define the physical layer and link layer, it supports various underlying network technologies and standards.
-
Network Layer: Responsible for processing the transmission, routing, flow control, and congestion control of IP packets. The ARP/RARP protocols are used to convert IP addresses to and from underlying physical addresses. The IP protocol is both the core protocol of the network layer and the core protocol of the entire TCP/IP protocol suite.
-
Transport Layer: Provides end-to-end communication for two hosts. The transport layer mainly includes the Transmission Control Protocol (TCP), which provides reliable connection-oriented transmission services, and the User Datagram Protocol (UDP), which offers simple and efficient connectionless services. The choice can be made based on the actual needs of higher-level applications.
-
Application Layer: Directly provides services for specific applications, such as File Transfer Protocol (FTP), Simple Mail Transfer Protocol (SMTP), and Hypertext Transfer Protocol (HTTP).
Important Concepts
Connection-oriented vs. Connectionless:
To communicate between two hosts using a connection-oriented protocol, a connection must first be established between the two hosts. How to establish/disconnect a connection? This involves the three-way handshake and the four-way handshake, which will be discussed later.
In contrast, a connectionless protocol does not require establishing a connection before communication, similar to sending a letter; you only need to know the destination address (note that this is just a metaphor; sending an email does not use a connectionless protocol, as connectionless protocols are typically unreliable).
Reliable vs. Unreliable:
Reliable protocols ensure that data can be transmitted to the destination without changes. TCP is an example of a reliable protocol.
Unreliable protocols cannot guarantee that data will reach the destination, but they will do their best and check whether the data received at the destination is complete. UDP is an example of an unreliable protocol.
Some may ask: Since there are reliable protocols, why do we need unreliable ones? Isn’t that redundant? Not at all; I will explain the advantages and disadvantages of TCP and UDP below.
Byte Stream vs. Datagram:
Byte stream protocols treat the data sent from the sender to the receiver as a continuous stream of bytes. Data that is sent first will be received first. TCP is a byte stream protocol.
Datagram protocols transmit data one by one without order. UDP is a datagram protocol.
Socket:
In the network layer, IP uses protocol numbers to specify transmission protocols, and in the transport layer, TCP/UDP uses port numbers to distinguish applications. Combining an IP address with a port number forms a socket, which indicates a unique network process in the network.
Advantages and Disadvantages of TCP and UDP
TCP:
-
Advantages: Reliable and stable. TCP’s reliability is reflected in the fact that it establishes a connection through a three-way handshake before data transmission, and during data transmission, it has mechanisms for acknowledgment, windowing, retransmission, and congestion control. After data transmission is complete, it also disconnects to save system resources.
-
Disadvantages: Slow, low efficiency, and high resource consumption, making it vulnerable to attacks. TCP requires establishing a connection before data transmission, which consumes time. Moreover, the acknowledgment, retransmission, and congestion control mechanisms during data transmission also consume a lot of time, and each device must maintain all transmission connections, which consumes CPU, memory, and other hardware resources. Additionally, due to TCP’s acknowledgment mechanism and three-way handshake, it can be exploited for DOS, DDOS, CC, and other attacks.
UDP:
-
Advantages: Fast and slightly more secure than TCP. UDP lacks TCP’s handshake, acknowledgment, windowing, retransmission, and congestion control mechanisms, making it a stateless transmission protocol that transmits data very quickly. Without these mechanisms, UDP is less vulnerable to exploitation than TCP. However, UDP is still susceptible to attacks, such as UDP Flood attacks.
-
Disadvantages: Unreliable and unstable. Because UDP lacks the reliable mechanisms of TCP, it is more prone to packet loss if the network quality is poor.
So, in which scenarios should TCP and UDP be used?
TCP: Email, remote login, etc. UDP: NDS, broadcasting, instant messaging, video calls, etc.
TCP’s Three-Way Handshake and Four-Way Handshake
Three-Way Handshake to Establish Connection:
Theoretically, establishing a TCP connection could be done with just one request and one response, but in practice, requests or responses may be lost, necessitating retransmission to establish the connection. If only one request and one response are used, the following issues may arise (images credited to Zhihu user @大闲人柴毛毛):
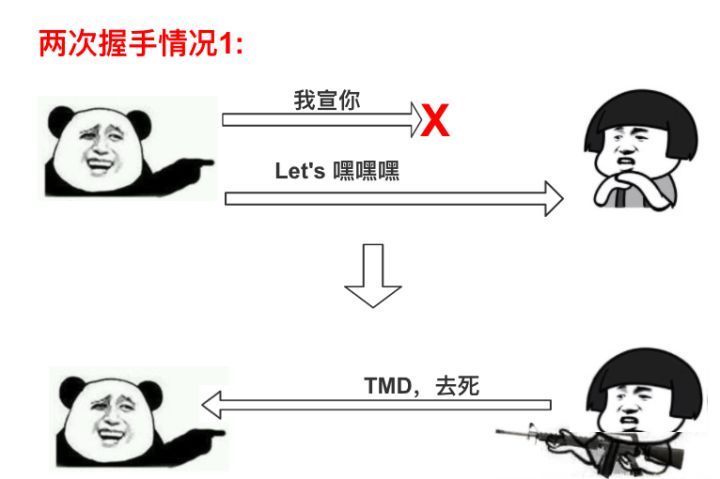
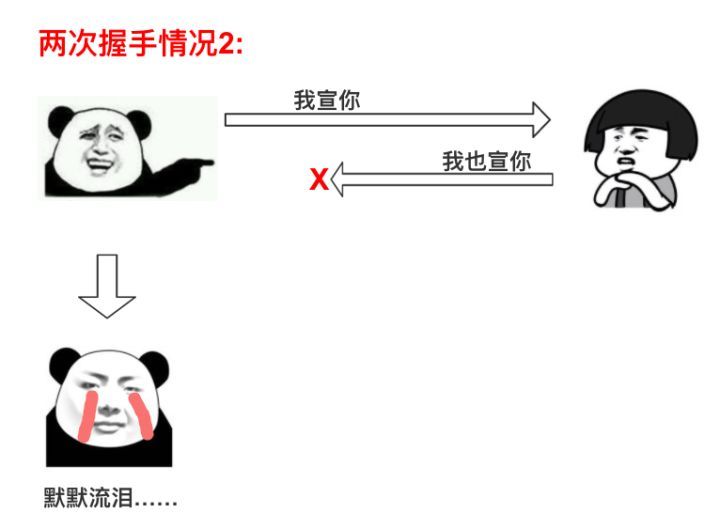
To address this issue, the “three-way handshake” during connection can effectively resolve it. (In fact, regardless of how many handshakes are performed, a channel cannot be guaranteed to be completely reliable; it can only indicate that it is usable. The three-way handshake allows both parties to clearly understand each other while minimizing overhead, which is why it is commonly used to establish connections.)
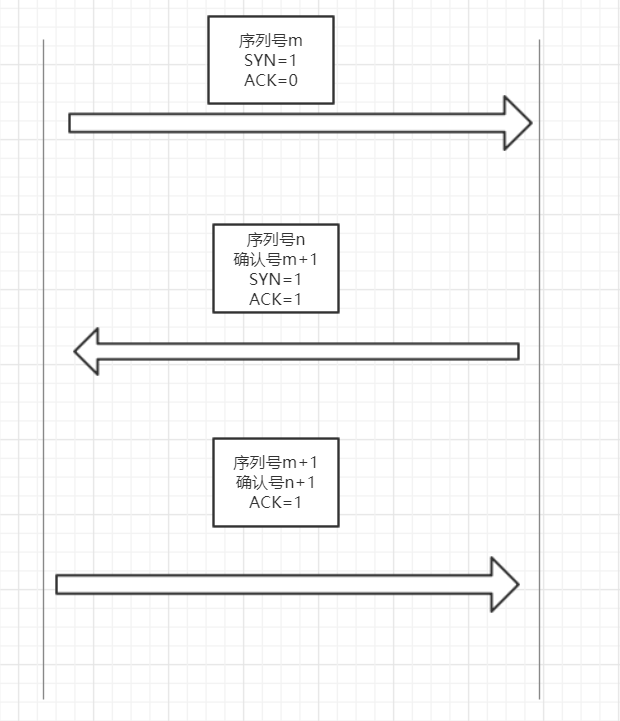
Next, I will draw a diagram to describe this process:
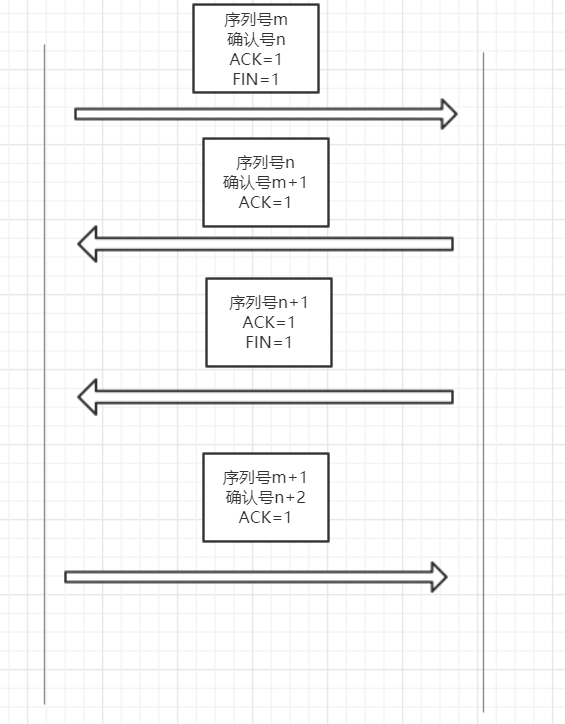
Four-Way Handshake to Disconnect:
Layered Analysis and Troubleshooting
During a phone interview, the interviewer asked me: If there is no data returned when calling a third-party service, what could be the problem? I initially answered that we could determine the issue based on the returned status code. The interviewer added that even the status code was not returned. I was momentarily speechless, unsure what the interviewer was trying to assess, and awkwardly moved on (I was quite inexperienced).
Later, I realized that a layered analysis of the protocol suite could effectively troubleshoot issues.
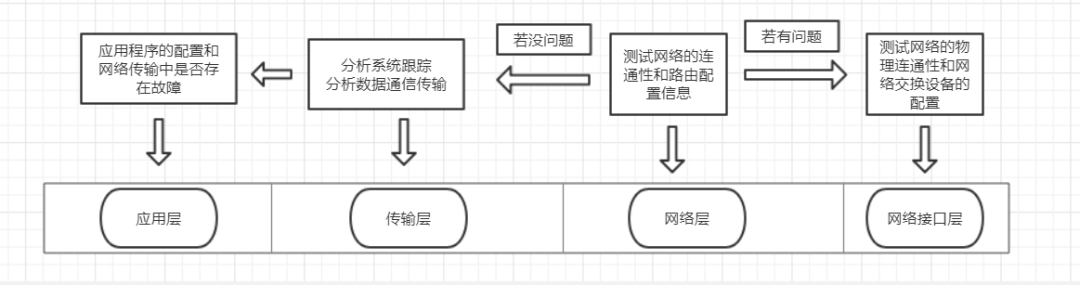
There are generally two troubleshooting approaches:
-
Start from the lower layers, first check the physical layer, such as whether the network cables are loose or damaged. This is generally used when a network has just been established or when network cables have been adjusted. Otherwise, it is too inefficient.
-
Start from the higher layers, first check the application layer, such as whether the browser is properly configured. This is generally used when the network environment is relatively stable.
To efficiently resolve issues, in practice, it is often more effective to start testing from the middle layer, which seems somewhat similar to the binary search concept.
Returning to the initial question:
If there is no data returned when calling a third-party service, what could be the problem?
1. Ping the target remote computer.
If successful, it indicates that the network is functioning normally, and further considerations can be made for higher layers, requiring testing of services or applications.
If failed, proceed to step 2.
2. Ping the gateway on the same subnet to confirm whether the host being used is connected to the local network.
If successful, it indicates that there is a connectivity issue between the local gateway and the remote target computer, and routing tests can be performed.
If failed, proceed to step 3.
3. Ping the loopback address 127.0.0.1.
If successful, it indicates that there is a communication issue between the local gateway and the current computer.
If failed, check if there is an issue with the IP address, and if there is, check if there are problems with the local TCP/IP protocol software, etc.
 (Author’s WeChat public account)
(Author’s WeChat public account)