Technical Insights: Use Ruijie to Enable WiFi Even When Your Computer is Shut Down!
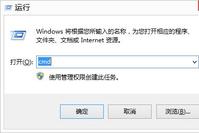
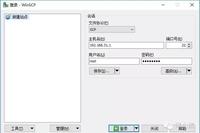
Are you still troubled by poor signals from CMCC or China Unicom? Are you worried about running out of data at the end of the month? Now, you only need a Phicomm K1 router and a Ruijie account password to provide 24-hour WiFi coverage for your entire dormitory! Download the required files: -TFTP32/TFTP64 (depending on … Read more