Authors:Zhao Yiqiang,Song Kaiyue,He Jiajie,Ma Haocheng
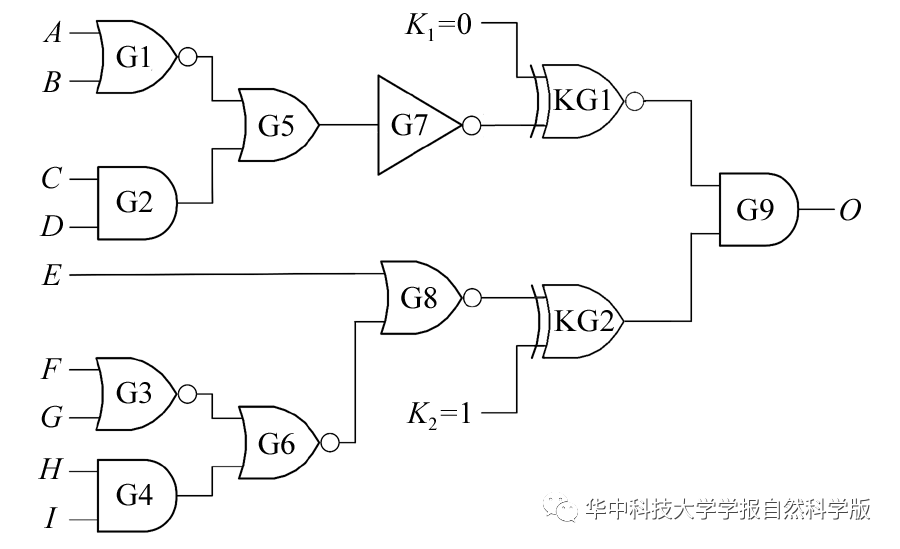
Abstract:In response to current hardware security threats such as integrated circuit (IC) counterfeiting and intellectual property (IP) theft, we propose an enhanced logic encryption algorithm based on secure authorization keys. This algorithm locates the insertion point of the “key gate” through a rare node analysis method, using the fully correlated secondary key generated by the key logic module as the input to the key gate;it resists attacks by implanting key security pairs to thwart attackers from breaking the key using path-sensitive attacks,which enhances the robustness of the logic encryption method and improves the security of the circuit. Using ISCAS’85 and ISCAS’89 benchmark circuits as research subjects for simulation verification, results show that the correlation between the primary key and the secondary key reached 100%,and the output damage rate of the incorrect key compared to the correct key reached 48%,effectively ensuring that the authorized key cannot be cracked;with a reasonable key size selected, the additional area of the circuit can be controlled to below 10%.
Keywords:Logic Encryption; Authorization Key; Fully Correlated; Rare Node; Key Gate; Path-Sensitive Attack; Output Damage Rate
Source:Zhao Yiqiang,Song Kaiyue,He Jiajie,Ma Haocheng.Enhanced Logic Encryption Algorithm Based on Secure Authorization Keys[J].Journal of Huazhong University of Science and Technology(Natural Science Edition),2020,48(5):1-6
DOI:10.13245/j.hust.200501