
This article is an excellent article from the Kx forum, author ID: wx_莫克斯
PreparationUSB Protocol Specifications
l USB UARTl USB HIDl USB MemoryThe one at the top is the standard serial port implementation, which can connect to MCUs like STM32 or ESP8266 via USB.
In the device descriptor:bDeviceClass, bDeviceSubClass, bDeviceProtocol must all be 0.
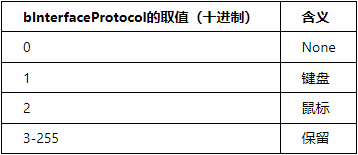
In the interface descriptor:bInterfaceClass must be 0x03, bInterfaceSubClass can be 0 or 1 (1 indicates that the HID device is a boot device, which is generally meaningful for PCs, meaning that the BIOS can recognize the HID device during startup, and only standard mice or keyboards can be called Boot Devices), and 0 indicates that the HID device can only be recognized after the operating system has booted.bInterfaceProtocol values are as follows:
A Question from buu

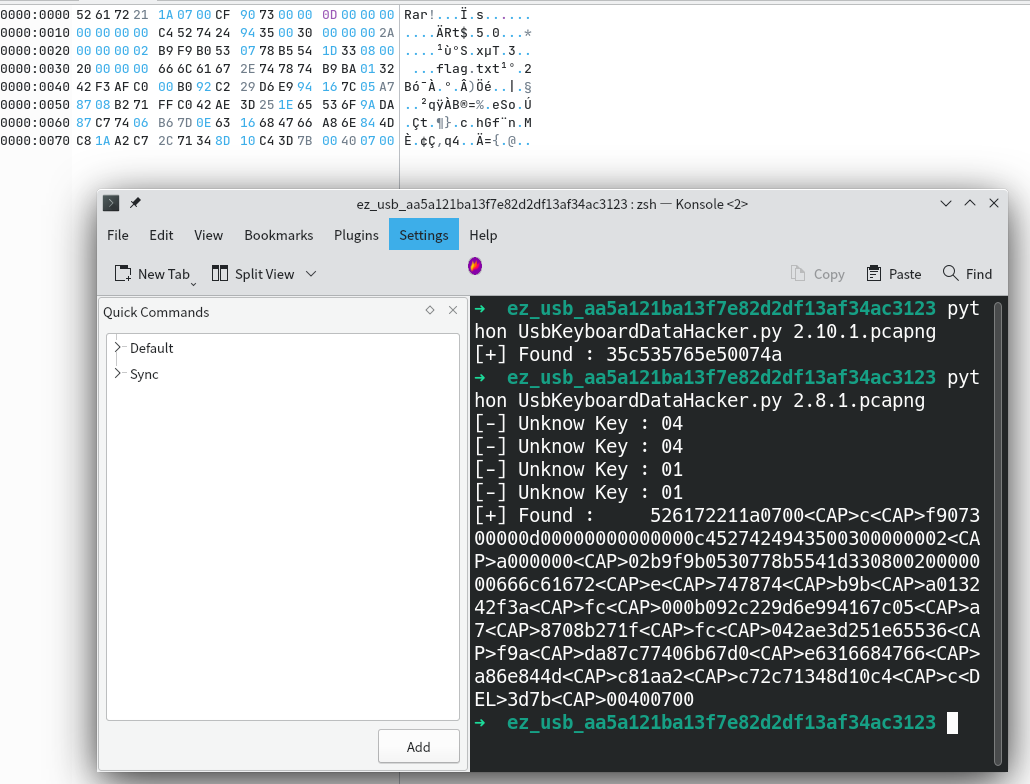
tshark -r key.pcap -T fields -e usb.capdata > usbdata.txt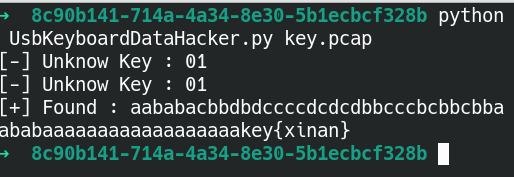
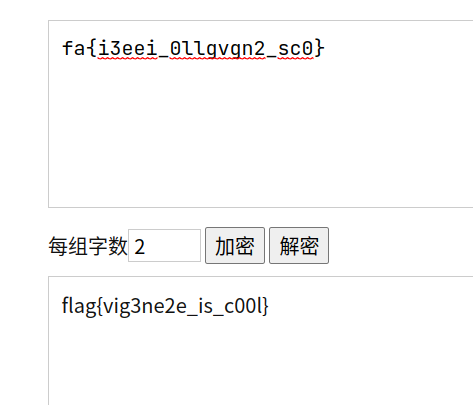
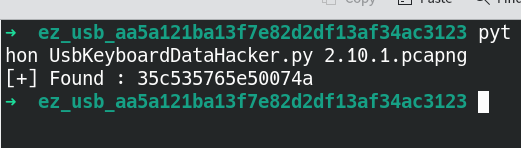
Main Topicusb.addr== "2.8.1"usb.addr== "2.10.1"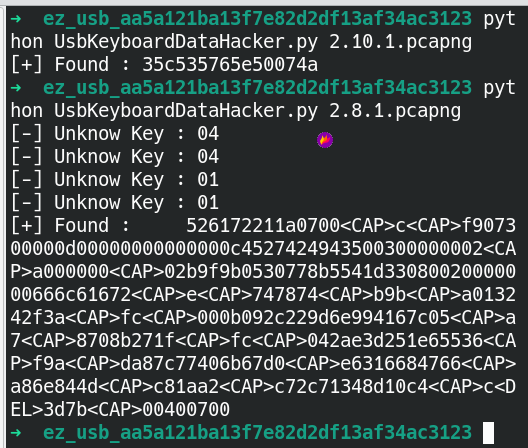
The Path Taken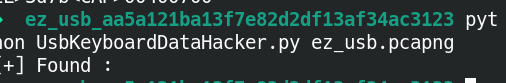
tshark -r ez_usb.pcapng -T fields -e usb.capdata > usbdata.txttshark -r ez_usb.pcapng -T fields -e usbhid.data > usbdata.txt
#!/usr/bin/env python#-*- coding: utf-8 -*-info = '''Run under kali: tshark -r usb.pcap -T fields -e usb.capdata > usbdata.txt to extract traffic packet information, then use this script to filter out spaces and other content, and add colons'''print(info) f_data = input("Please enter the path of the txt file to be processed:")shujian = int(input("For mouse traffic information, please enter 8, for keyboard traffic enter 16:"))f = open(f_data,'r') # Organizing into out.txtwith open('out.txt','w') as f_out: for i in f.readlines(): s = i.strip() # Mouse traffic length is 8, keyboard traffic length is 16 if len(s) == shujian: # Mouse traffic length is 8, keyboard traffic length is 16 nsl = [s[j:j+2] for j in range(0,shujian,2)] ns = ":".join(nsl) f_out.write(ns) f_out.write('\n')//tran.pynormalKeys = {"04": "a", "05": "b", "06": "c", "07": "d", "08": "e", "09": "f", "0a": "g", "0b": "h", "0c": "i", "0d": "j", "0e": "k", "0f": "l", "10": "m", "11": "n", "12": "o", "13": "p", "14": "q", "15": "r", "16": "s", "17": "t", "18": "u", "19": "v", "1a": "w", "1b": "x", "1c": "y", "1d": "z", "1e": "1", "1f": "2", "20": "3", "21": "4", "22": "5", "23": "6", "24": "7", "25": "8", "26": "9", "27": "0", "28": "<RET>", "29": "<ESC>", "2a": "<DEL>", "2b": "\t", "2c": "<SPACE>", "2d": "-", "2e": "=", "2f": "[", "30": "]", "31": "\\", "32": "<NON>", "33": ";", "34": "'", "35": "<GA>", "36": ",", "37": ".", "38": "/", "39": "<CAP>", "3a": "<F1>", "3b": "<F2>", "3c": "<F3>", "3d": "<F4>", "3e": "<F5>", "3f": "<F6>", "40": "<F7>", "41": "<F8>", "42": "<F9>", "43": "<F10>", "44": "<F11>", "45": "<F12>"} shiftKeys = {"04": "A", "05": "B", "06": "C", "07": "D", "08": "E", "09": "F", "0a": "G", "0b": "H", "0c": "I", "0d": "J", "0e": "K", "0f": "L", "10": "M", "11": "N", "12": "O", "13": "P", "14": "Q", "15": "R", "16": "S", "17": "T", "18": "U", "19": "V", "1a": "W", "1b": "X", "1c": "Y", "1d": "Z", "1e": "!", "1f": "@", "20": "#", "21": "$", "22": "%", "23": "^", "24": "&", "25": "*", "26": "(`, "27": ")", "28": "<RET>", "29": "<ESC>", "2a": "<DEL>", "2b": "\t", "2c": "<SPACE>", "2d": "_", "2e": "+", "2f": "{", "30": "}", "31": "|", "32": "<NON>", "33": "\"", "34": ":", "35": "<GA>", "36": "<", "37": ">", "38": "?", "39": "<CAP>", "3a": "<F1>", "3b": "<F2>", "3c": "<F3>", "3d": "<F4>", "3e": "<F5>", "3f": "<F6>", "40": "<F7>", "41": "<F8>", "42": "<F9>", "43": "<F10>", "44": "<F11>", "45": "<F12>"}output = []keys = open('out.txt') # This is the data for plus and colonfor line in keys: try: if line[0]!='0' or (line[1]!='0' and line[1]!='2') or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0' or line[6:8]=="00": continue if line[6:8] in normalKeys.keys(): output += [[normalKeys[line[6:8]]],[shiftKeys[line[6:8]]]][line[1]=='2'] else: output += ['[unknown]'] except: passkeys.close() flag=0print("output :" + "".join(output))for i in range(len(output)): try: a=output.index('<DEL>') del output[a] del output[a-1] except: passfor i in range(len(output)): try: if output[i]=="<CAP>": flag+=1 output.pop(i) if flag==2: flag=0 if flag!=0: output[i]=output[i].upper() except: passprint ('output :' + "".join(output))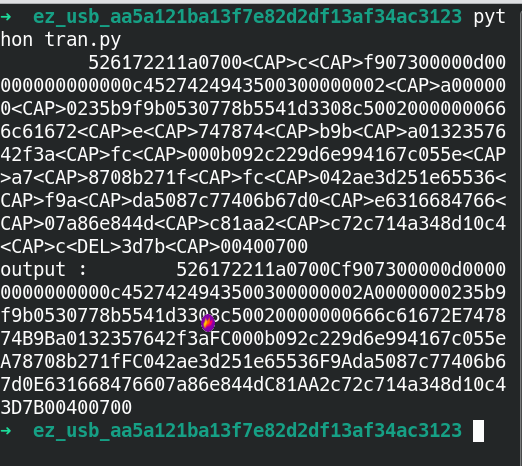
EpilogueSupplementUsed EXP
References
Supplementary & Consolidation Exercises

Kx ID: wx_莫克斯
https://bbs.pediy.com/user-home-916399.htm

# Previous Recommendations
1. Flutter APP Reverse Engineering Practice
2. APT Turla Sample Analysis
3. CVE-2021-24086 Vulnerability Analysis
4. In-depth Analysis of BattlEye Kernel Driver Detection Module
5. Seccomp BPF and Container Security
6. “Controlling” a Router Device with U-Boot
Share
Like
Watching