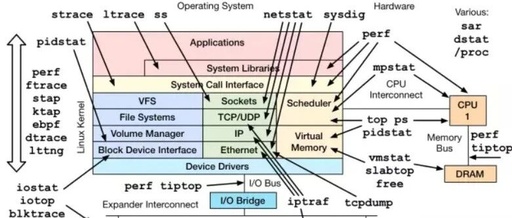
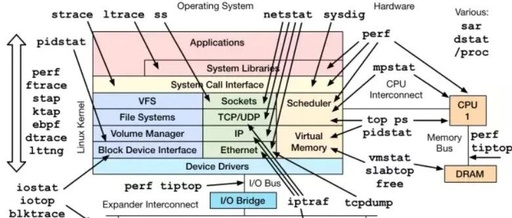
Eight Commonly Used Linux Performance Monitoring Commands: How Many Have You Used?
Image source: Internet In Linux systems, there are many performance monitoring tools. Below, I will introduce several commonly used command-line tools. 1. top/htop top: Function: Real-time monitoring of processes, displaying information about CPU, memory, load, swap space, etc. Common Shortcuts: Shortcut Description M Sort by memory usage P Sort by CPU usage k Kill a … Read more