Essential Skills for Linux Experts: A Comprehensive Guide to Environment Variables
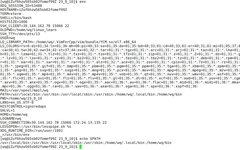
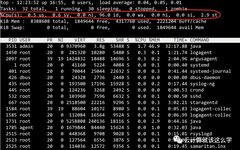
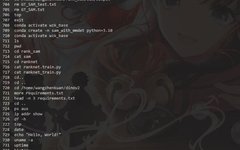
Linux | Red Hat Certified | IT Technology | Operations Engineer 👇 Join the 1000-person technical communication QQ group. Note: [Public Account] for faster approval 1. Basic Concepts Environment variables (environment variables) generally refer to parameters used to specify the operating environment of the operating system. For example: when we write C/C++ code, we never … Read more