Linux | Red Hat Certification | IT Technology | Operations Engineer
👇 1000 people technical exchange QQ group, note [public account] for faster approval

Shell
Linux is an open-source, Unix-based operating system that is widely used in servers, embedded systems, supercomputers, and desktop computing due to its flexibility, stability, and high performance.
The Linux Kernel is the core of the operating system, responsible for direct interaction with hardware and providing an interface for resource management and system services to user space (applications and services).
The main responsibilities of the Linux Kernel are:
Hardware Abstraction: Abstracting low-level hardware resources (such as CPU, memory, hard drives, etc.) into more user-friendly interfaces. Resource Management: Allocating and managing CPU time, memory space, file systems, and other resources. System Call Interface: Providing a set of APIs for user programs to access hardware or operating system functions through system calls. Device Drivers: Managing various hardware devices (such as keyboards, displays, network cards, etc.).Generally, users cannot directly interact with the Linux Kernel, but instead interact with it indirectly through the Shell.
The Shell is the interface between the user and the kernel, acting as a command interpreter (shell program). It translates user-entered commands into system calls that the kernel can understand, thus controlling the behavior of the operating system.
Main Functions:
Command Parsing: Interpreting and executing user-entered commands (such as file operations, program execution, etc.). Script Support: Running pre-written Shell scripts for task automation. User Environment Provision: Allowing users to execute programs, manage files, and configure the system.Analogous to the Windows operating system, the Windows GUI corresponds to the Shell in Linux; we do not directly operate its kernel but complete various operations through a graphical interface.
User Permissions
In the Linux system, the root user and ordinary users are two different permission levels, each responsible for system management and regular operations, respectively.
Root User: The super administrator in the Linux system, possessing the highest permissions for all resources in the system and able to perform any operation. Ordinary User: Users with limited permissions in the system, mainly for daily operations.The command prompt for the root user is “#”, while the prompt for ordinary users is “$”.
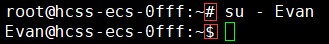
Switching Users
Switching from an ordinary user to the root user:
Using the su command:
suEnter the root password to switch.
Note that this switch directly changes from the current directory to the ordinary user.
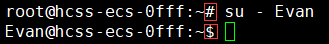
As can be seen, the directory for the root user is LinuxCode, and after switching to an ordinary user, the directory remains LinuxCode.
Switching from the root user to an ordinary user:
Exit the root user:
exitSpecify switching to a certain ordinary user:
su usernamesu – command
The su – command acts as a re-login when switching users and will not switch in the original directory.
Default directory for the root user:
/rootDefault directory for ordinary users:
/home/usernamesudo
Ordinary users have limited permissions and can perform fewer operations, but sometimes it is necessary for ordinary users to perform privileged operations, which requires using the sudo command.
sudo (Superuser DO) is a tool in Linux and Unix systems used to execute commands as the root user or another privileged user. It allows ordinary users to temporarily elevate permissions without directly logging in as the root user, thus reducing the risk of misoperations and enhancing system security.
Normally, for an ordinary user to use sudo, they need to be added to the whitelist, and the specific configuration file is in /etc/sudoers. We can open it with vim and add the ordinary user to the whitelist.
vim /etc/sudoers
(The demonstration environment is Ubuntu 20.04.6)
Usage Example:
sudo apt updateThe system will prompt for the current user’s password (not the root user’s password), and then execute the command with root permissions.
File and Directory Permissions
Visitors
Each file and directory in Linux is primarily composed of the following three parts:
User (Owner): The owner of the file or directory. User Group (Group): A group of users that can share permissions for the file or directory. Others (Others): Users other than the file owner and user group.Permission Representation
Linux uses the rwx mode to represent permissions:
r (read): Read permission.
For files: Can view content.
For directories: Can list directory contents.
w (write): Write permission.
For files: Can modify content.
For directories: Can create, delete, or rename files within the directory.
x (execute): Execute permission.
For files: Can run as a program.
For directories: Can enter the directory.
The permissions for each file are represented by 10 characters, for example:
-rwxr-xr--The first character:File type
- indicates a regular file d indicates a directory l indicates a symbolic link b indicates a block device file (e.g., hard drives, optical drives, etc.) p indicates a pipe file c indicates a character device file (e.g., screen, serial devices) s indicates a socket fileThe next 9 characters:are divided into three groups (user, user group, others).
User (Owner): rwx indicates readable, writable, executable User Group (Group): r-x indicates readable, not writable, executable Others (Others): r-- indicates readable, not writable, not executableFile permissions can also be represented in octal and binary:
Permission Octal Binary rwx 7 111 rw- 6 110 r-w 5 101 r– 4 100 -wr 3 011 -w- 2 010 –x 1 001 — 0 000Use the ls -l (ll) command to view file and directory permissions:
ls -lOutput Example:
-rw-r--r-- 1 user group 1234 Dec 1 10:00 file.txt-rw-r--r--: Permission bits. user: File owner. group: File's associated user group.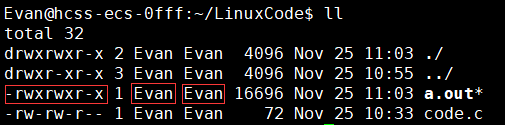
Modifying Permissions
The chmod command is used to modify file or directory permissions.
Symbolic Mode:
chmod u+x file.txt # Add execute permission for the owner chmod g-w file.txt # Remove write permission for the user group chmod o+r file.txt # Add read permission for others chmod o=r filename # Set others' permission to read-only (overrides other permissions)Numeric Mode (each permission corresponds to a number):
r = 4
w = 2
x = 1
No Permission = 0
Permission Combinations: rwx = 7, rw- = 6, r– = 4, etc.
chmod 754 file.txt # Set permissions to rwxr-xr---R Recursive Permission Modification:
// Modify permissions for directory and its subdirectories and files chmod -R 755 /path/to/directorychown command and chgrp: Modify file owner and user group.
chown user file.txt # Change file owner chgrp group file.txt # Change file user group chown user:group file.txt # Change file owner and user group-R Recursive Modification:
chown -R user:group /path/to/directory
umask
umask (User File Creation Mode Mask) is a command or configuration used to set default permissions for files and directories. It defines the permission mask for newly created files or directories, thereby controlling the initial value of default permissions.
Default Permissions for Files and Directories
In Linux, the permissions for newly created files and directories are based on the following default values:
File: 666 (readable and writable, no execute permission).
Directory: 777 (readable, writable, executable).
However, these default permissions will be masked by umask, and the final permissions are:
Final Permissions = Default Permissions - umaskumask Representation
The value of umask usually has 4 digits, but the first digit of 0 indicates special permissions and can be ignored, so it can be viewed as a 3-digit octal number, with each digit representing a permission mask:
The first digit: User (Owner).
The second digit: User Group (Group).
The third digit: Others (Others).
Masking Rules:
4: Mask read permission (r).
2: Mask write permission (w).
1: Mask execute permission (x).
0: Do not mask any permissions.
For example, if the umask value is 0002, it means masking write permission (w) for others; 0033 means masking write (w) and execute (x) permissions for user group and others.
Viewing and Setting umask
To view the current umask value:
umask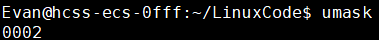
To set umask:
umask 0xxx // Set umask code to 0xxxDirectory Permissions
In the Linux system, directory permissions (Directory Permissions) determine the user’s access and operational capabilities regarding directories. The permissions for directories are similar to those for files, but their specific functions are slightly different since directories are primarily used to organize files rather than directly store content.
Read Permission (r, read)
Allows viewing the list of files and subdirectories within the directory. Without execute permission, one cannot enter the directory, even if read permission exists, they cannot view the directory contents.Write Permission (w, write)
Allows writing operations within the directory, including: Creating new files or directories. Deleting or renaming files/subdirectories. Requires execute permission to be effective.Execute Permission (x, execute)
Allows entering the directory. Without read permission, one can enter the directory but cannot list its contents.Sticky Bit
The Sticky Bit is a special permission in Linux and Unix systems, primarily used for directory permission management. It ensures that files within a directory can only be deleted or modified by the file owner or users with administrative privileges, even if the directory itself has write permissions open to other users.
Effects of the Sticky Bit
Under normal permission settings, if a user has write permission on a directory, they can delete or modify any file within that directory, regardless of whether those files belong to them. The Sticky Bit limits this behavior, providing finer permission control:
Only the file owner, directory owner, or superuser (root) can delete or modify the file.
Other users, even with write permissions on the directory, cannot delete or modify files they did not create.
Typical Use Cases for the Sticky Bit
Public Directory:
For example, in the /tmp directory, all users can create files, but cannot arbitrarily delete other users’ files.
The permissions for /tmp are usually set to:
drwxrwxrwt # Note that the last t indicates that the sticky bit is enabledCollaborative Environment:
In shared directories, different users can create their own files but cannot affect other users’ files.
Viewing and Setting the Sticky Bit
Use the ls -ld command to view the permission status of a directory:
ls -ld directory_nameExample Output:
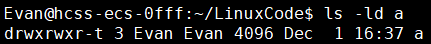
The last character t indicates that the sticky bit is enabled for that directory.
rwxrwxr- are the basic permissions (user, group, other users).
Use the chmod command to set or remove the sticky bit.
// Add sticky bit chmod +t directory chmod 1775 directory // The octal value corresponding to the sticky bit is 1000 // Remove sticky bit chmod -t directory chmod 0775 directoryCourse inquiries add: HCIE666CCIE
↓ Or scan the QR code below ↓
What technical points and content would you like to see?
You can leave a message below to tell us!