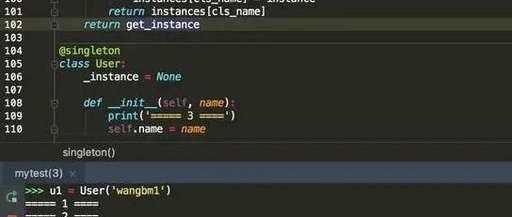
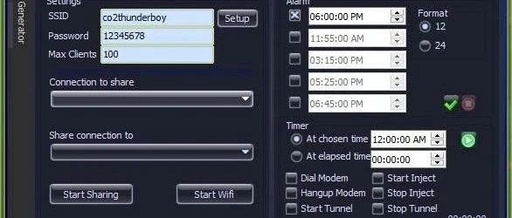
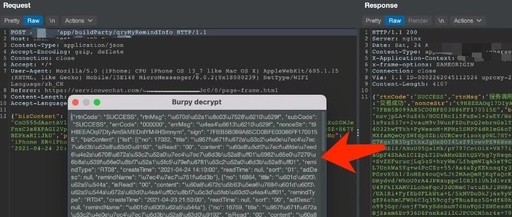
Hotspot Observation | Focusing on Power Grid Attack Incidents: Analyzing Vulnerabilities and Security Testing in Industrial Control Systems
As cyber attack methods continue to evolve, industrial control systems, represented by power systems, are gradually shifting from being a “secondary impact area” to a core target in the cyber attack chain. Especially in the context of the ongoing advancement of the industrial internet and the continuous integration of “cloud-edge-end” collaborative systems into key business … Read more