What is MQTT?MQTT is a lightweight communication protocol for the Internet of Things (IoT), based on a publish-subscribe model, widely used for real-time communication between devices. The MQTT Broker is the central hub for messages, responsible for receiving, storing, and distributing messages.
Risks of Unauthorized Access to MQTT:
- Data Leakage: Attackers may subscribe to sensitive topics and obtain information that should not be public.
- Message Forgery: Attackers may publish false messages, disrupting the normal operation of devices.
- Denial of Service (DoS): Attackers may send a large number of junk messages, consuming network bandwidth or exhausting Broker resources.
- Device Control: Attackers may remotely control devices by publishing control commands.
Verification of Unauthorized Access to MQTTDownload the MQTTX Client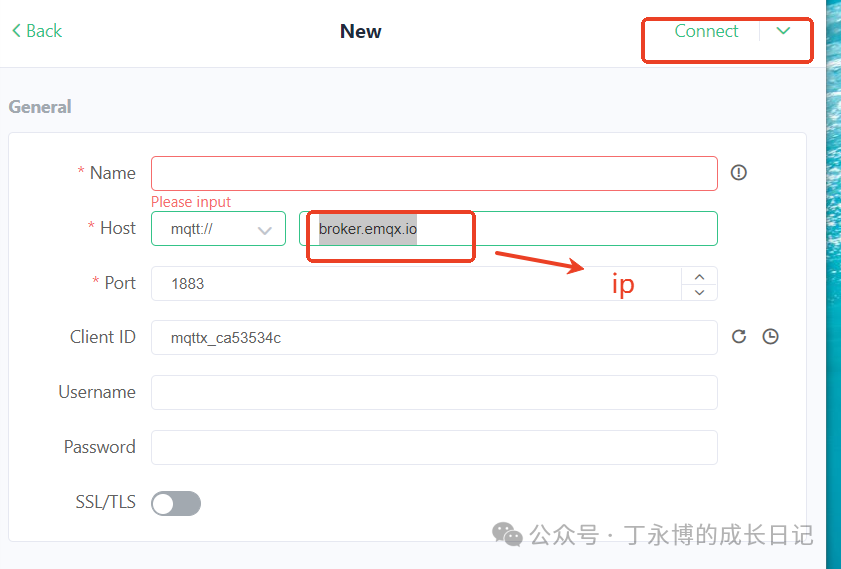 Successful Connection Screen
Successful Connection Screen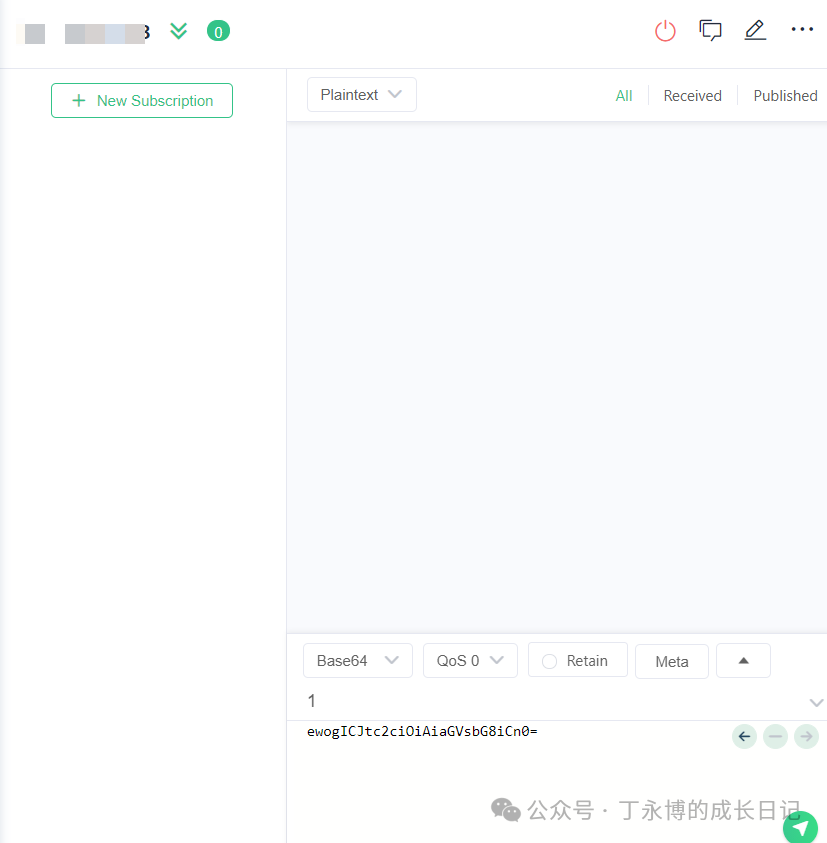 Detection PoC
Detection PoC
from rich import print
from rich.panel import Panel
from rich.text import Text
panel = Panel(Text("Hello, I am Ding Yongbo. Welcome to follow the WeChat public account: Ding Yongbo's Growth Diary!", justify="center"))
print(panel)
import socket
import paho.mqtt.client as mqtt
from concurrent.futures import ThreadPoolExecutor
# Configuration parameters
PORT = 1883
TIMEOUT = 5 # Timeout (seconds)
THREADS = 50 # Number of concurrent threads
def check_mqtt(ip): """Check if the specified IP has unauthorized access to MQTT""" try: # First check if the port is open with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s: s.settimeout(TIMEOUT) if s.connect_ex((ip, PORT)) != 0: return None # Initialize MQTT client client = mqtt.Client() client.connect(ip, PORT, keepalive=TIMEOUT)
# Set callback function result = {"status": False} def on_connect(client, userdata, flags, rc): result["status"] = (rc == 0) # 0 indicates successful connection
client.on_connect = on_connect client.loop_start() client.loop_stop() return ip if result["status"] else None except (mqtt.WebsocketConnectionError, ConnectionRefusedError, TimeoutError): return None except Exception as e: print(f"An exception occurred while checking {ip}: {str(e)}") return None
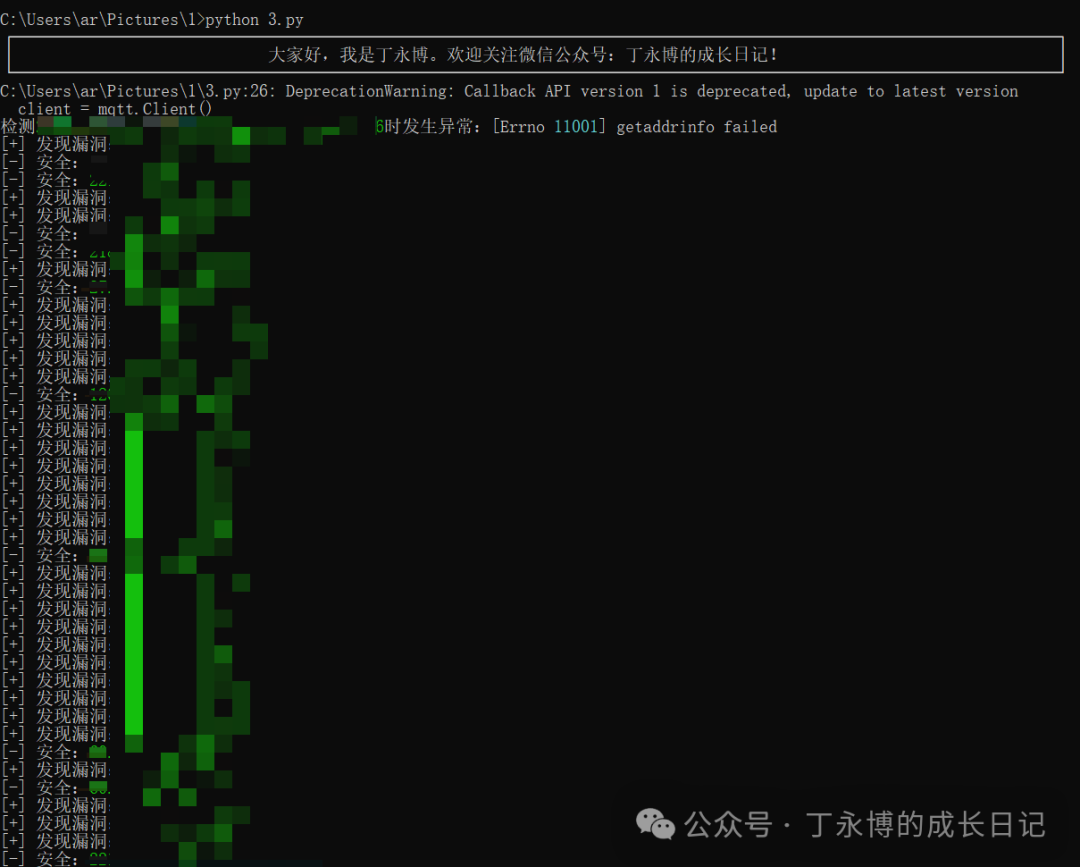
def main(): # Read target IP list try: with open("1.txt", "r") as f: ips = [line.strip() for line in f if line.strip()] except FileNotFoundError: print("Error: 1.txt file does not exist!") return # Use thread pool for concurrent detection vulnerable = [] with ThreadPoolExecutor(max_workers=THREADS) as executor: results = executor.map(check_mqtt, ips) for ip, status in zip(ips, results): if status: print(f"[+] Vulnerability found: {ip}") vulnerable.append(ip) else: print(f"[-] Safe: {ip}") # Save results if vulnerable: with open("2.txt", "w") as f: f.write("\n".join(vulnerable)) print(f"Found {len(vulnerable)} vulnerabilities, results saved to 2.txt") else: print("No unauthorized access vulnerabilities found in MQTT")
if __name__ == "__main__": # Check dependencies try: import paho.mqtt except ImportError: print("Please install paho-mqtt first: pip install paho-mqtt") exit(1)
main()Usage:
-
Install dependencies:
<span>pip install paho-mqtt</span> -
Install dependencies:pip install rich
-
Create target file:
<span>1.txt</span>(one IP address per line) -
Run the script:
<span>python 3.py</span> -
View results:
<span>2.txt</span>(contains hosts with unauthorized access)
Notes:
-
This tool is for authorized testing only
-
It is recommended to adjust the
<span>THREADS</span>parameter (recommended 50-100) before large-scale scanning -
In corporate intranet environments, the
<span>TIMEOUT</span>can be shortened to 2 seconds -
In sensitive environments, it is recommended to use a proxy pool

Small Knowledge
According to Article 285, Paragraph 3 of the Criminal Law, those who provide illegal intrusion or control of computer information systems shall be sentenced to imprisonment for not more than three years or criminal detention, and shall be fined or solely fined; if the circumstances are particularly serious, they shall be sentenced to imprisonment for not less than three years but not more than seven years, and shall be fined.
Disclaimer
The technical parameters provided in this article are for reference only for learning or operational personnel to test internal systems. Please do not use the techniques provided in this article for destructive testing without authorization. Any direct or indirect losses caused by the use of the information provided in this article shall be borne by the user. Welcome to view丨leave a message丨share to friends Three connections
Welcome to view丨leave a message丨share to friends Three connections
Good articlerecommendation
-
Read others’ WeChat chat records without logging in
- Practical | Secrets in monitoring
- Trojan tool | Control others’ computers, very simple!
- BlueLotus links with DVWA to achieve XSS cookie theft
- Practical | Logic vulnerability bypass
- Do not pick up USB drives on the roadside, the woman at the foot of the mountain is a tiger~
- Eternal Blue Rainbow Cat linkage
- 5min learn penetration | WiFi disconnection attack, brute force attack
- 5min learn penetration | How is your phone monitored?
- 5min learn penetration | Simple production of phishing WiFi 01
- Practical small tool | Crack office suite encryption passwords