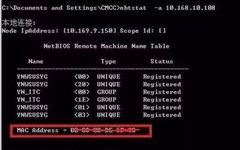
Modifying MAC Address on Embedded Linux Network Interface
Hello everyone, I am the Intelligence Guy~ Modifying the MAC address is a common development requirement in network management and privacy protection. 1. Why Change the MAC Address? For example, when we replace a damaged network card, we need to restore the original MAC address to maintain IP allocation, firewall policies, and device authentication; there … Read more