Common Linux Commands Collected Over the Years
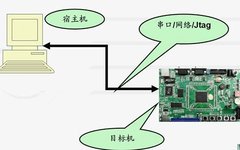
Although most of my work is related to networking, I also deal with Linux systems, especially after using Mac, where I work daily in a command-line environment with a black background. My memory is not very good, and I can’t remember many useful Linux commands. Therefore, I am gradually summarizing them for future reference. Basic … Read more