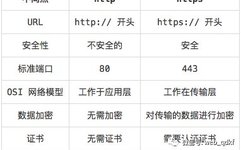
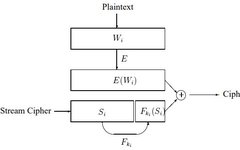
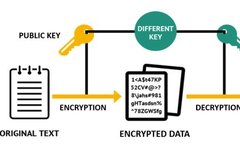
Applications of Asymmetric Encryption Algorithms
In previous articles, we briefly discussed asymmetric encryption, which involves splitting a key into two parts: one part is kept private, known as the private key, while the other part can be publicly shared, known as the public key. The encryption algorithm ensures that data encrypted with one key can only be decrypted with the … Read more