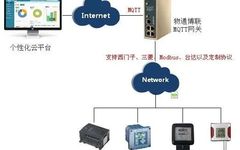
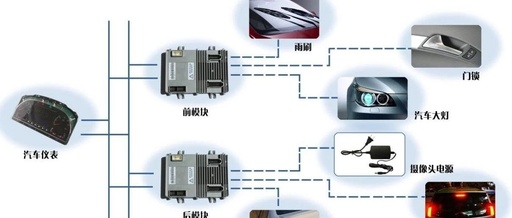
Safety Risks of Shared Power Banks Using Raspberry Pi
Last night, while going out for dinner, I stumbled upon this: This must be the so-called “shared power bank” right? I don’t know how you feel about it, but this thing has been all over my feed in the past few days… Shared bikes, another member of the “sharing family,” have not been doing well … Read more