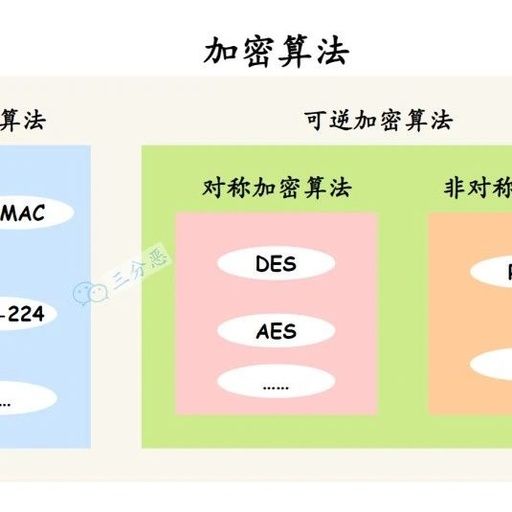
The Safest Encryption Algorithms to Date
An encryption algorithm that can only be cracked by computing power 1 The History of Human Encryption In the 5th century BC, the ancient Greeks used a stick called scytale to transmit encrypted messages. To encrypt, one would wrap a strip of paper around the stick and write the message horizontally along the stick, rotating … Read more