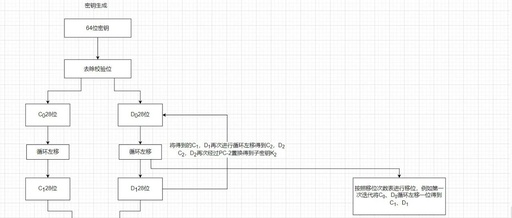
Encrypting Database Connection Information and YAML Configuration Properties in Spring Boot Using the SM4 National Encryption Algorithm (Automatic Decryption on Read)
Click on the “Business Card” above to follow our public account You can obtain programming materials from the menu bar Hello, I am Coder-Wen Xiaobai,a post-95 Java backend developer. 1. Introduction In the process of developing business systems, we inevitably use databases. During application development, database connection information is often configured in plain text in … Read more