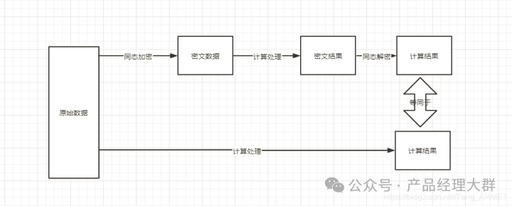
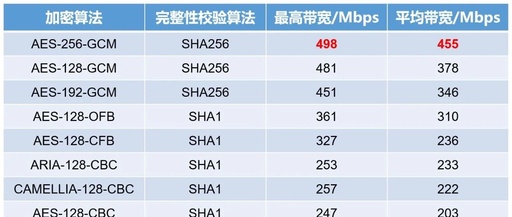
RSA: A Classic Asymmetric Encryption Algorithm
RSA (Rivest-Shamir-Adleman) is a classic asymmetric encryption algorithm proposed by three cryptographers Ron Rivest, Adi Shamir, and Leonard Adleman in 1977. Its core function is to achieve secure communication through public key encryption and private key decryption, widely used in digital signatures, SSL/TLS protocols, data encryption, and other fields. Key Generation Principle of RSA Significance … Read more