Understanding RSA Algorithm Principles (Part 1)
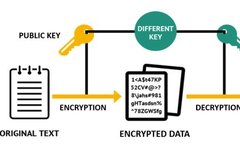
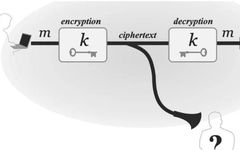
If you ask me, which algorithm is the most important? I might answer “Public Key Encryption Algorithm“. Because it is the cornerstone of computer communication security, ensuring that encrypted data cannot be cracked. You can imagine the consequences if credit card transactions are compromised. Before getting into the main topic, let me briefly introduce what … Read more