
Click the blue text above to follow us
Data loss is a common and urgent issue in embedded systems during operation, especially in application scenarios involving frequent data writes (such as database operations).

It manifests in various forms, from minor loss of the latest records to severe issues such as file name corruption, loss of system files, or even complete data clearance of entire partitions, all of which can severely impact system stability and business continuity.
The root causes of data loss typically involve multiple levels, including hardware, system drivers, and application software design.
Therefore, addressing data loss in embedded systems requires a comprehensive strategy that considers the robustness of hardware design, the resilience at the system level, and the optimization at the application software level, to maximize data security and overall system stability.
1
Analysis of Data Loss Phenomena and Root Causes
The specific manifestations of data loss in embedded systems are complex and varied, commonly including:
- Minor manifestations:Recent write records in the database are inexplicably lost, or some data items are empty.
- More serious situations:A significant number of records in the database are lost, compromising data integrity.
- Severe cases:File names in the file system are lost or displayed as garbled text, making files inaccessible.
- Very severe cases:Critical system files are lost, or user data partitions (such as /opt) are cleared, causing the system to fail to boot or function abnormally.
In-depth exploration of the causes of data loss can be summarized into the following aspects:
Hardware Level
- Unstable power supply:The quality of the power supply is the cornerstone of stable system operation. Issues such as insufficient power, excessive ripple, and voltage fluctuations can lead to abnormal system operation, resulting in data read/write errors or loss. Especially during power outages, unstable voltage may interrupt ongoing write operations or corrupt data.
- Storage medium issues:NAND Flash, eMMC, and other storage media have inherent limitations on erase/write cycles (P/E cycles). Frequent write operations accelerate medium aging, increasing the probability of bad blocks, ultimately leading to data being unable to be written or read. The quality of the storage medium and the working environment (temperature, humidity) also affect its reliability.
- Hardware design defects:Improper design of power loss detection circuits, interface signal integrity issues, etc., may also indirectly lead to data loss.
System/Driver Level
- Driver program defects:Unstable or buggy storage device drivers may lead to data write failures, file system corruption, and other issues.
- Improper file system selection:Choosing an inappropriate file system for different storage media and application scenarios may lead to poor performance, data loss, or reduced lifespan.
- Incorrect mount option configuration:Using asynchronous (async) mounts in high-reliability scenarios increases the risk of data loss during system crashes.
- Inadequate handling of power loss by the system:The operating system or driver fails to respond correctly to power loss events, resulting in data in the cache not being promptly written to non-volatile storage media.
Application Software Level
- Software design defects:Issues in application programs regarding data writing logic, error handling, resource management, etc., such as buffer overflows, memory leaks, race conditions, may lead to abnormal data writes or loss.
- Improper database usage:Unreasonable database configuration, improper use of transaction processing mechanisms, or bugs in the database itself may lead to data loss.
- Lack of data verification and backup mechanisms:Applications fail to effectively verify written data and do not implement necessary data backup strategies, leading to irrecoverable data corruption.
- Improper handling of abnormal shutdowns:Applications fail to gracefully handle shutdown or power loss signals, resulting in ongoing data operations being forcibly interrupted.
To solve the data loss problem in embedded systems, a systematic approach must be taken, integrating hardware design, system configuration, and software optimization to build a multi-layered protection system.
2
Hardware Level Optimization
Stable and Reliable Power Design:
- Ensure that the power module provides sufficient power margin to meet the system’s peak power consumption requirements.
- Strictly control power ripple and noise to ensure power quality.
- Select high-quality power components and conduct thorough power stability testing.
Power Loss Detection and Protection Circuits:
- Design precise and fast-responding power loss detection circuits that can issue early warning signals to the system before the main power voltage drops to dangerous thresholds.
- Utilize hardware circuits (such as voltage monitoring chips) or software mechanisms to implement power status monitoring.
Backup Power Solutions:
- For applications where data is extremely critical, consider adding backup power, such as supercapacitors or small lithium batteries.
- Backup power should be paired with power loss detection circuits to ensure that the system has enough time to save critical data and synchronize file systems after the main power fails.
3
System/Driver Level Optimization
Robust and Reliable Driver Programs:
- Select or develop storage device drivers that have been thoroughly tested and are highly stable.
- Ensure that the driver can correctly handle various exceptions and boundary conditions.
System-Level Power Loss Handling Mechanism:
- The operating system kernel or related drivers need to correctly respond to hardware-issued power loss warning signals.
- Upon receiving a power loss signal, new write requests should be immediately stopped, and dirty data in the file system cache should be forced to be written to the physical storage medium.
Selecting an Appropriate File System: (See next section)
- Choose the optimal file system based on the type of storage medium (NAND/eMMC), capacity, performance requirements, and reliability needs (such as power loss safety).
Optimizing File System Mount Options: (See subsequent chapters)
- Choose appropriate mount options (such as sync/async, ro/rw) based on the emphasis on performance and data security in the application scenario.
4
Application Software Level Optimization
Application Response to Power Loss:
- Applications should be able to receive and process power loss notifications sent by the system.
- Upon receiving the notification, they should immediately stop or complete the current data write operations, close file handles, and perform necessary data cleanup and saving tasks.
Data Redundancy and Backup Strategies:
- Local Backup:If storage space allows, maintain dual or multiple backups of critical data locally, stored in different physical areas or partitions.
- Remote Backup:For networked devices, back up critical data to remote servers in real-time or periodically over the network. This method effectively mitigates the risk of total local storage failure.
- Cloud Storage Backup:Utilize the storage capabilities provided by cloud services to synchronize data to the cloud in real-time or near real-time, providing a high level of data security.
Data Integrity Verification:
- Implement data verification mechanisms during data writing and reading, such as using CRC (Cyclic Redundancy Check) or Checksum.
- In case of verification failure, log the error and attempt to recover data from backups.
Transaction Processing:
- For database operations or critical data updates, use transaction mechanisms to ensure the atomicity of operations, either all succeed or all roll back, avoiding data inconsistency.
Reducing Unnecessary Write Operations:
- Optimize data recording logic, merge small write operations, and avoid writing to storage media too frequently.
- For non-essential real-time data, cache first and then write in batches.
5
In-Depth Analysis of File System Selection
Selecting the appropriate file system for specific embedded storage media is a key step in ensuring data security and system performance.
5.1, File Systems Suitable for NAND Flash
Due to its physical characteristics (such as bad blocks and erase/write cycle limitations), NAND Flash requires specially designed file systems for management. Common ones include UBIFS and YAFFS2.

5.2, File Systems Suitable for eMMC
eMMC (embedded MultiMediaCard) integrates a controller internally, masking the complex management details of NAND Flash from the upper layers, appearing as a block device. Common file systems include FAT32 and Ext4.
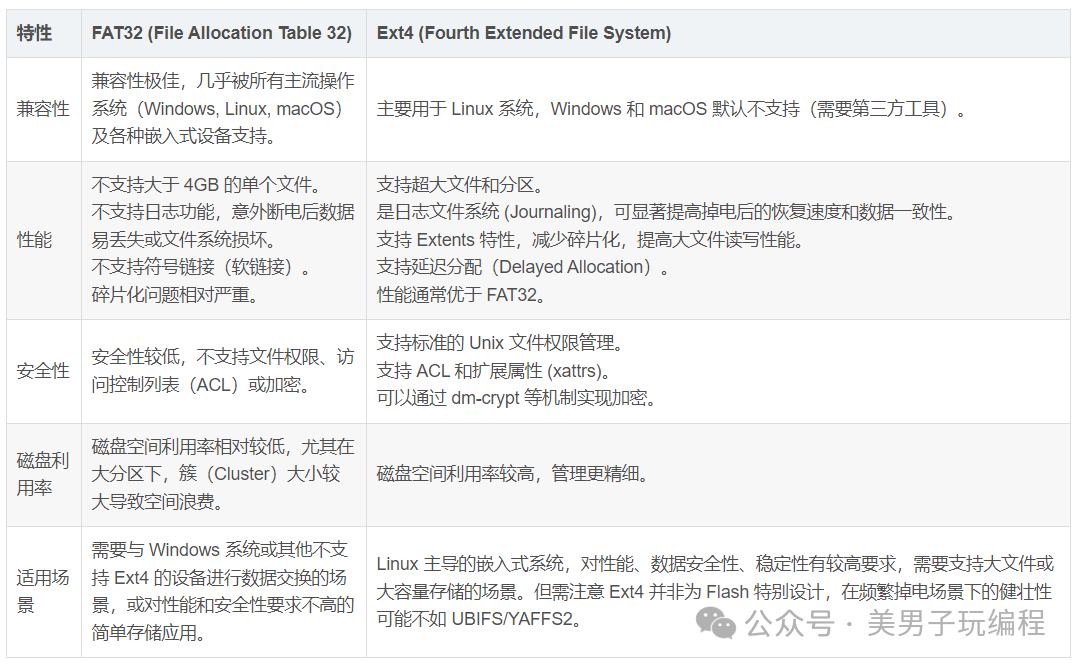
Selection Recommendations
- NAND Flash:If the capacity is large and the power supply is stable, pursuing high performance and scalability, UBIFS is the preferred choice. If the device requires frequent read/write operations, fast boot speed, and occasional power outages are unavoidable, YAFFS2 is more suitable.
- eMMC:If cross-platform compatibility is the primary consideration, choose FAT32. If higher performance, security, and stability are sought, and the system is primarily based on Linux, Ext4 is the better choice.
6
Practical Optimization of System Mount Options
In Linux systems, file systems need to be mounted to specified mount points (directories) using the mount command before they can be accessed. Different options can be specified during mounting, which directly affect the behavior, performance, and data security of the file system.
Basic Syntax of the Mount Command
Basic syntax: mount [-t fstype] [-o options] device dir
- -t fstype: Specifies the file system type, which can usually be omitted as the mount command will automatically detect it.
- -o options: Specifies mount options, with multiple options separated by commas.
- device: The device to be mounted (such as partition /dev/mmcblk0p2 or LVM volume).
- dir: The mount point directory (must exist beforehand).
Key Mount Options
async (Asynchronous Mount – Default Option)
- Behavior:File system I/O operations (such as writes) are first written to the memory buffer (Page Cache/Buffer Cache), and the operating system will asynchronously flush the cached data to the physical disk at a later time.
- Advantages:Significantly improves I/O performance and reduces program wait times.
- Disadvantages:If the system crashes or loses power before the data is flushed to the disk, the cached data will be lost. This is one of the common causes of data loss.
- Applicable Scenarios:Scenarios with high performance requirements but some tolerance for data loss. Caution is advised in production environments.
sync (Synchronous Mount)
- Behavior:Any I/O operation that causes changes to file metadata or data will be immediately and synchronously written to the physical disk, returning only after completion.
- Advantages:Maximizes data security. Even if the system crashes suddenly, the data corresponding to completed write operations has been written to disk and is less likely to be lost.
- Disadvantages:Severely sacrifices I/O performance, as each write must wait for the physical disk operation to complete.
- Applicable Scenarios:Scenarios with extremely high data security requirements (such as financial transaction data) where performance loss can be tolerated.
data=journal (Ext4 Specific Option)
- Behavior:Provides the highest level of data consistency. All data (including file content and metadata) is first written to a journal before being written to its final location.
- Advantages:Even in the event of a crash, the file system can ensure that data is not lost after recovery.
- Disadvantages:Compared to the default data=ordered (which only logs metadata), performance will decrease because data is written twice (once to the journal, once to the actual location).
data=writeback (Ext4 Specific Option)
- Behavior:Only metadata is logged to the journal, while file data is written directly to the disk, without guaranteeing the order of writing data and metadata.
- Advantages:May provide better performance than data=ordered under certain workloads.
- Disadvantages:Lowest data security. After a crash, old data may appear in files corresponding to newly written metadata.
ro (Read-Only Mount)
- Behavior:Mounts the file system in read-only mode.
- Advantages:Effectively protects the contents of the partition from accidental modification or deletion. Suitable for mounting partitions containing critical system files or configurations.
- Disadvantages:No data can be written.
rw (Read-Write Mount – Default Included in Defaults)
- Behavior:Mounts the file system in read-write mode.
- Advantages:Allows modification of the contents of the partition.
- Disadvantages:Risk of accidental or malicious modifications.
defaults
- Behavior:Represents a set of default mount options, typically including rw, suid, dev, exec, auto, nouser, async. The specific options included may vary slightly depending on the system and file system type.
noatime / nodiratime
- Behavior:Prevents updating the access time stamp (atime) of files or directories.
- Advantages:Reduces write operations triggered by read operations, which can improve performance, especially on Flash media, and reduce unnecessary writes.
- Disadvantages:Accurate file access times cannot be obtained.
By carefully selecting file systems and finely configuring mount options, a balance can be achieved between performance and data security, significantly enhancing the stability and data reliability of embedded systems in scenarios with frequent writes.

 Click Read Original for more exciting content~
Click Read Original for more exciting content~