Follow+Star Public Account Number, don’t miss out on exciting content
Author | strongerHuang
WeChat Public Account | strongerHuangTrustZone, translated as: secure zone, trusted zone.TrustZone is a hardware-level security technology introduced by ARM, aimed at providing stronger security protection for embedded systems by isolating sensitive resources from non-secure operations.The latest Arm Cortex-M85 core includes TrustZone functionality, which has been around for over a decade. The Renesas RA8 microcontroller we previously shared also incorporates this technology.
Renesas RA8 Series Tutorial | Generating Keil Project Based on RASC
2025-03-16
About TrustZone
TrustZone is a hardware-enforced isolation mechanism that divides CPU, memory, peripherals, and other resources into a secure world (Secure World) and a non-secure world (Non-secure World).Through hardware-level permission control, it ensures that non-secure code cannot directly access critical resources in the secure world (such as encryption keys, firmware, etc.), thereby defending against software attacks or physical side-channel attacks.In the Cortex-M85 (RA8 microcontroller), TrustZone is implemented based on the Armv8.1-M architecture and optimized for the RA8 (MCU) scenario, providing low-latency, low-overhead security isolation suitable for high real-time embedded applications.Key Functions of TrustZone1. Hardware-level Resource IsolationMemory and Peripheral Partitioning: Each memory block and peripheral can be marked as secure or non-secure, and hardware will intercept non-secure code attempting to access secure resources.Secure State Switching: Switching between secure and non-secure states using dedicated instructions (such as SG/NSG) ensures that critical operations (like key processing) are executed only in a secure environment.2. Isolation of Security ServicesThe secure world can run trusted code (such as encryption algorithms, secure boot, firmware updates), while the non-secure world runs regular applications, preventing malicious code from stealing sensitive data.Supports a secure callback mechanism, allowing non-secure code to call secure services (such as signature verification) through controlled interfaces, avoiding direct exposure of security logic.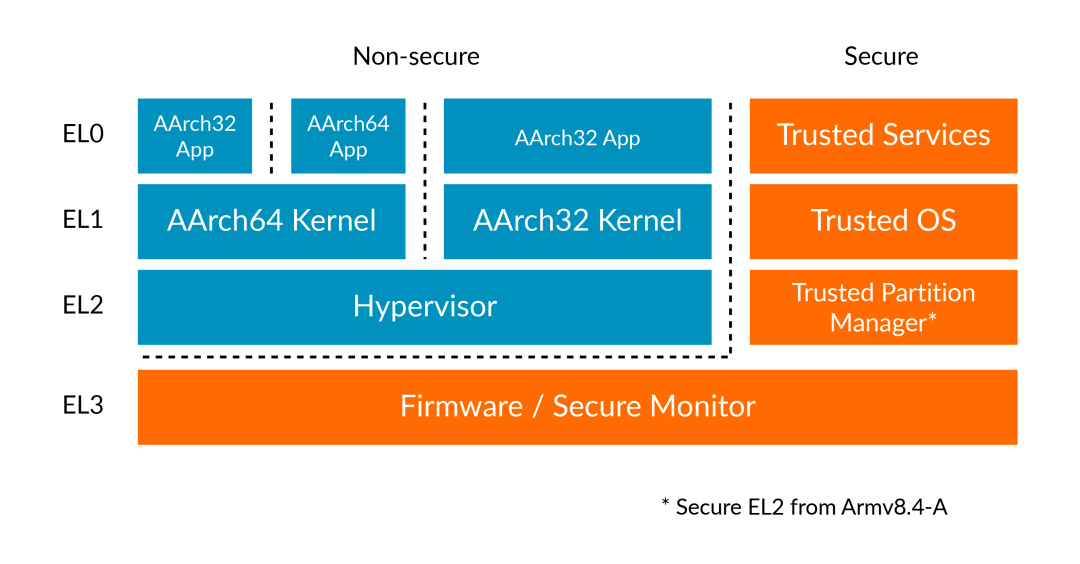 3. Defense Against Various AttacksPrevents unauthorized access to the secure world due to software vulnerabilities (such as buffer overflows).Combined with physical protection measures (such as tamper detection), it enhances resistance to hardware attacks.
3. Defense Against Various AttacksPrevents unauthorized access to the secure world due to software vulnerabilities (such as buffer overflows).Combined with physical protection measures (such as tamper detection), it enhances resistance to hardware attacks.
The Important Role of TrustZone in Projects
Many of you present are likely involved in embedded development and have encountered software bugs at some point.In fact, many bugs in embedded development are often caused by memory issues. Simply put, they are due to “illegal” operations on memory addresses. Some bugs also arise from illegal operations on hardware.At this point, introducing a feature like TrustZone can significantly reduce the occurrence of bugs. So, what are the important roles of TrustZone in projects?
1. Enhancing System Security
Protection of Sensitive Data: Keys, certificates, etc., stored in the secure world cannot be directly read by attackers even if the application layer is compromised.
Secure Boot and Firmware Updates: Ensures that only signed firmware can execute in the secure world, preventing malicious firmware injection.

2. Reducing Development and Deployment Costs
Single-chip Integration of Security Features: No need for external security elements (SE), reducing hardware complexity and costs.
Modular Development: Security and non-security code can be developed independently, making team collaboration more efficient (e.g., security teams handle the secure world, application teams handle the non-secure world).
3. Enhancing Product Competitiveness
Adaptation to Harsh Scenarios: Suitable for high-security-demand fields such as smart homes, medical devices, and the Internet of Vehicles.
Extending Product Lifespan: Through trusted remote firmware updates, vulnerabilities can be continuously patched, reducing recall risks.
RA8 TrustZone Project
Based on Renesas e2 studio, a RA8D1_TrustZone project can be quickly created.The main step is to select TrustZone Secure Project when creating the project: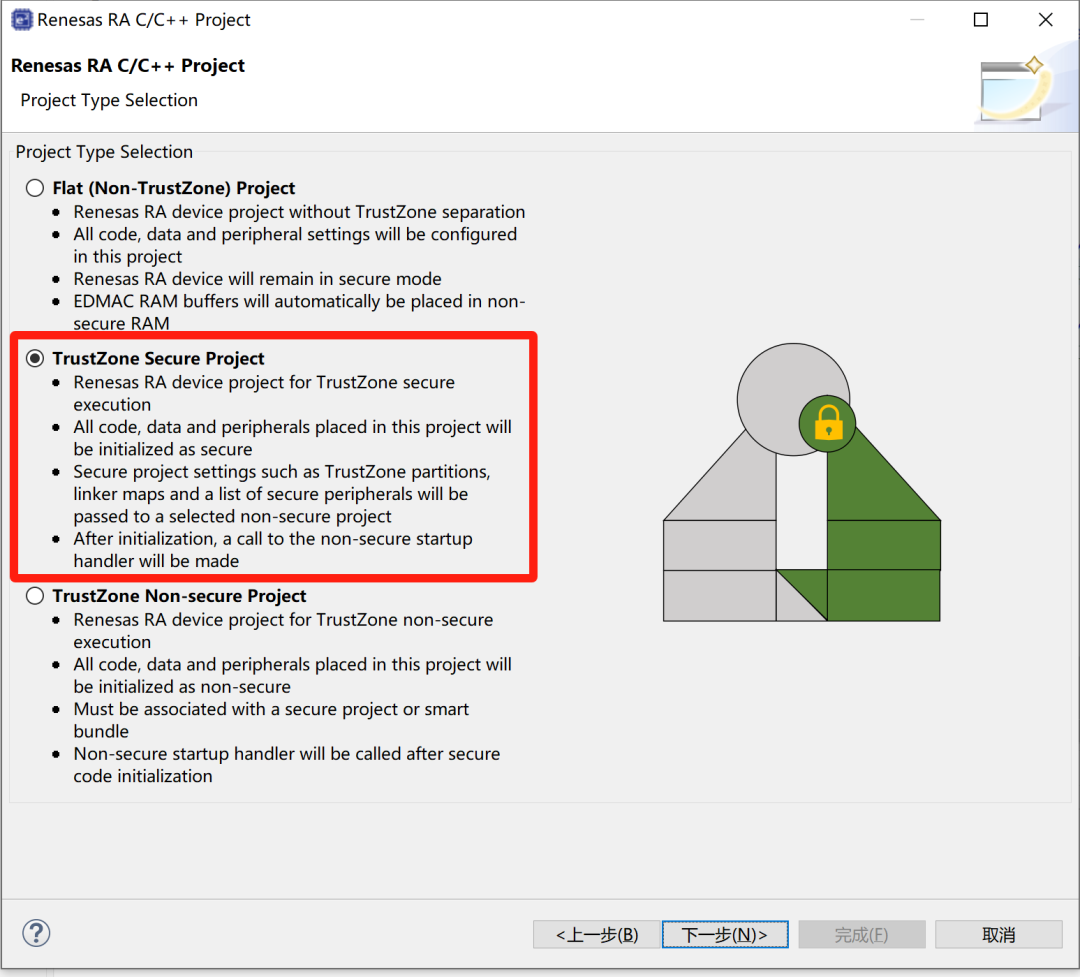 Additionally, the official also provides project examples:
Additionally, the official also provides project examples: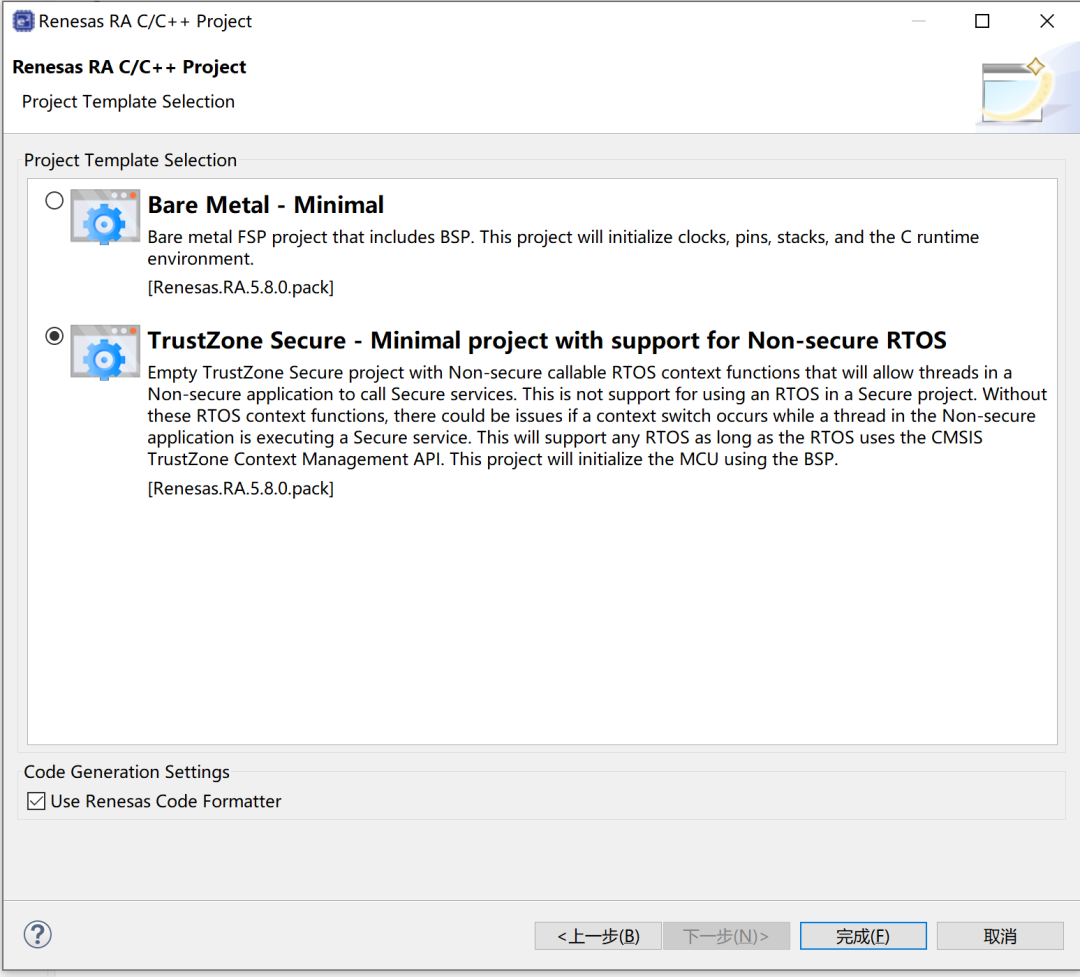 The generated project looks no different from a regular project, but there are changes at the lower level. A noticeable difference is the memory addresses. Tools can actually reveal some changes in information.
The generated project looks no different from a regular project, but there are changes at the lower level. A noticeable difference is the memory addresses. Tools can actually reveal some changes in information.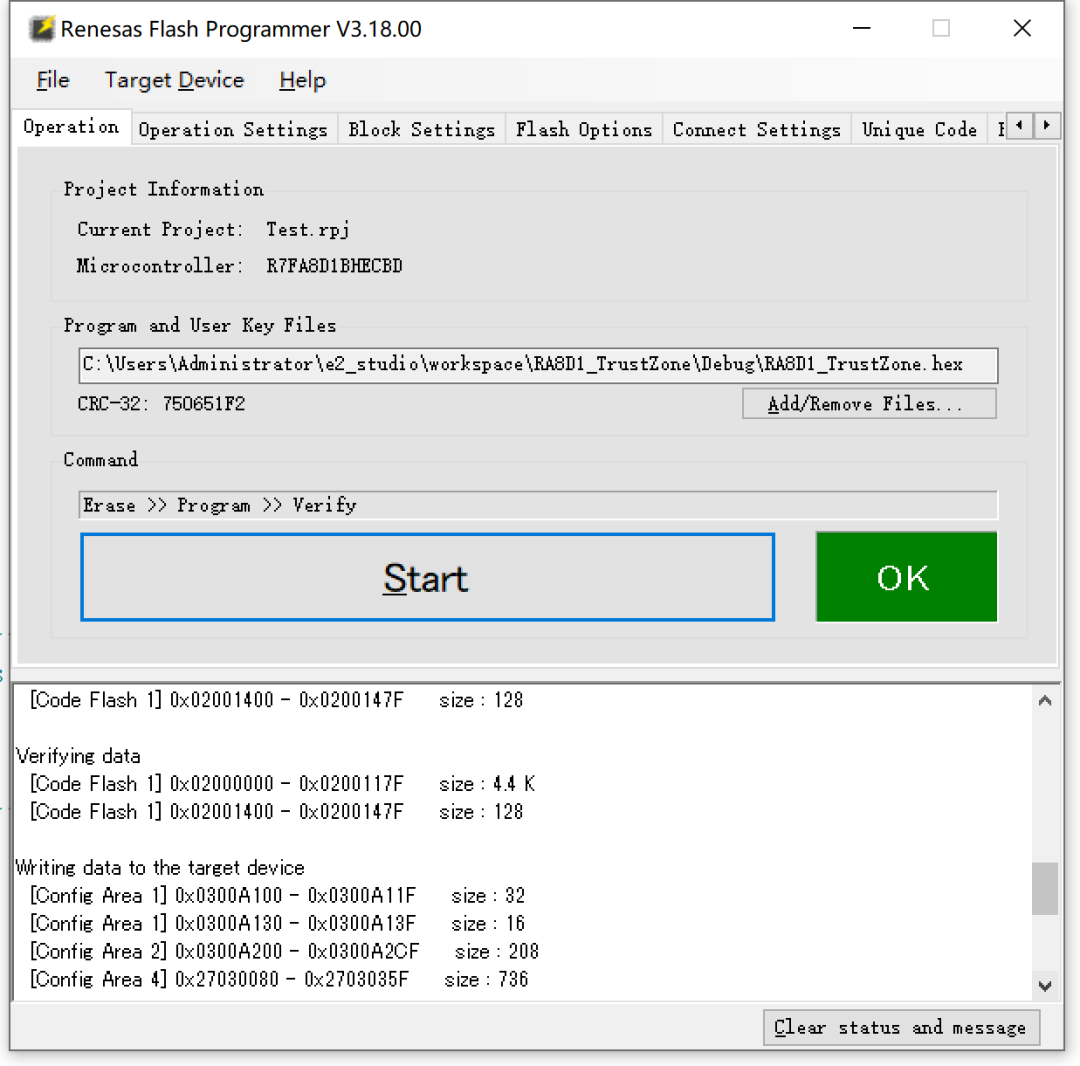 That’s all for today, mainly some basic information. More understanding requires everyone to combine it with actual projects. I hope this is helpful to everyone.
That’s all for today, mainly some basic information. More understanding requires everyone to combine it with actual projects. I hope this is helpful to everyone.
Renesas RA8 Series Tutorial······