Linux | Red Hat Certified | IT Technology | Operations Engineer
👇 1000 people technical exchange QQ group, note 【public account】 to pass faster

Super User (root) and Regular User
There are two types of users in Linux: Super User (root) and Regular User
Super User: Can do anything in Linux without restrictions.
Regular User: Restricted in Linux.
You can check whether you are a Super User or a Regular User using the whoami command.
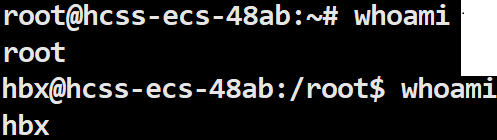
It can be observed that the command prompt for the Super User is #, while for the Regular User it is $.
su Command
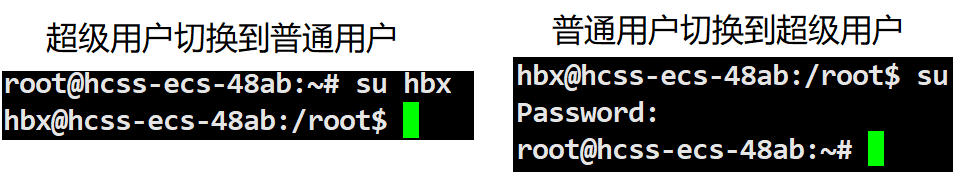
How do we switch users under different users?
We can switch users using the su command. If the Super User switches to a Regular User, just use su + the username of the Regular User to complete the switch. If a Regular User switches to the Super User, simply use the su command and enter the Super User’s password to complete the switch.
sudo Command
Temporarily elevate permissions for specified commands for Regular Users.
When we use sudo for elevation, we may encounter errors. This is because there is something similar to a whitelist; the current user does not have sudo permissions.
To use sudo, the current user must be configured in the /etc/sudoers file. At this point, the administrator needs to add the current user to the user group allowed to use sudo (usually sudo or wheel). This is not a big issue, but if you want to know more, you can check this blog post: Detailed Explanation of the Linux Command sudo.
2. Linux Permission Management
2.1 File Accessors
In simple terms, the essence of permissions is what can and cannot be done. Permissions primarily restrict roles, and the target must have corresponding attributes.
Linux permissions consist of roles and target permission attributes. Permissions = Roles + Target Permission Attributes
Roles include Owner, Group, and Others.
Roles: Owner 2. Group 3. Others Owner (User, u): The owner of the file or directory. Group (Group, g): The user group to which the file or directory belongs. Others (Others, o): All users except the file owner and user group.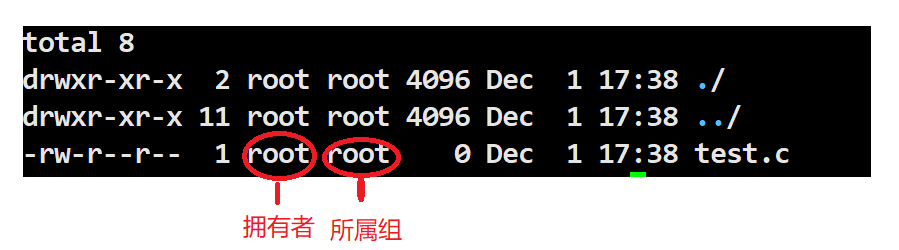
Owner
The owner is the current user in Linux, whether it is a Super User or Regular User. The owner of the file or directory.
Group
The users in the group to which the file or directory belongs. More precise permission management requires more refined identity roles.
Others
Other users. However, we find that Others are not recorded.
Others do not need to be recorded due to issues like log redundancy and excessive auditing, because Others include all users who are not the file owner or group, and operations are frequent and difficult to record accurately. The focus of auditing is different; administrators are more concerned about specific users, groups, and commands executed rather than every change in Others permissions. In terms of security and permission management, changes in Others permissions are usually infrequent and should not occur frequently, so they generally do not need to be specially recorded.
2.2 File Types and Access Permissions
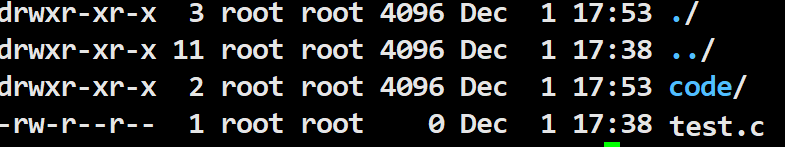
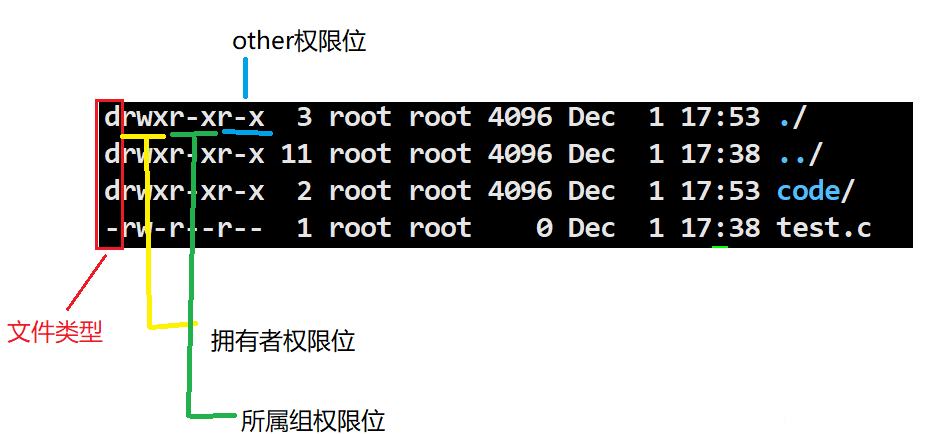
File Types
d for directory, – for file
Representation of File Permission Values
r for read permission
w for write permission
x for execute permission
drwxr-xr-x 2 root root 4096 Dec 1 17:53 code/In the above example, the owner has read, write, and execute permissions; the group has read and execute permissions but not write; others have read and execute permissions but not write.
Numeric Expression
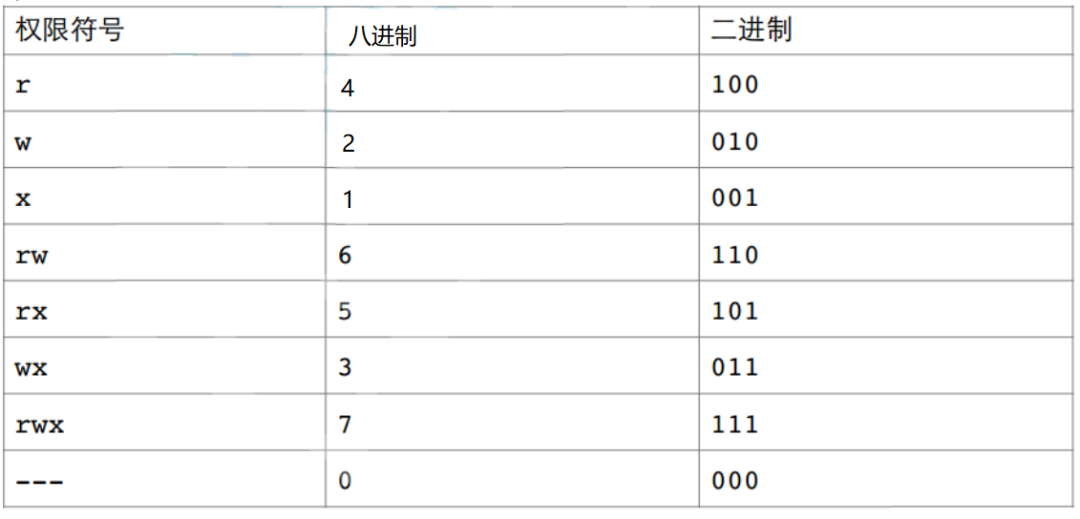
These rwx are binary; they are either allowed or not allowed. So if it is rw-rw-r–, the binary is 110 110 100, and the octal is 664.
Methods for Setting File Access Permissions (chmod)
Command chmod: Set file access permissions.
chmod u-r code
This modifies the read permission for the owner of the file code from allowed to not allowed.
root@hcss-ecs-48ab:~/learn/test_12_1# chmod u-r code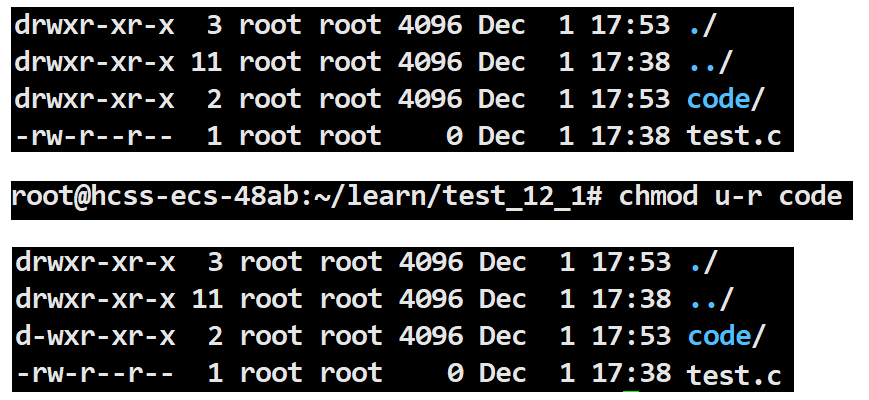
chmod u+r
This modifies the read permission for the owner of the file code from not allowed to allowed.
root@hcss-ecs-48ab:~/learn/test_12_1# chmod u+r code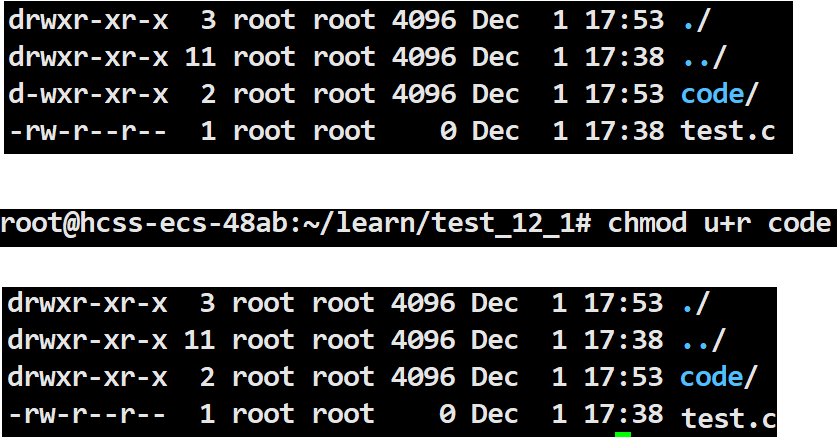
chmod g-r code
This modifies the read permission for the group of the file code from allowed to not allowed.
root@hcss-ecs-48ab:~/learn/test_12_1# chmod g-r code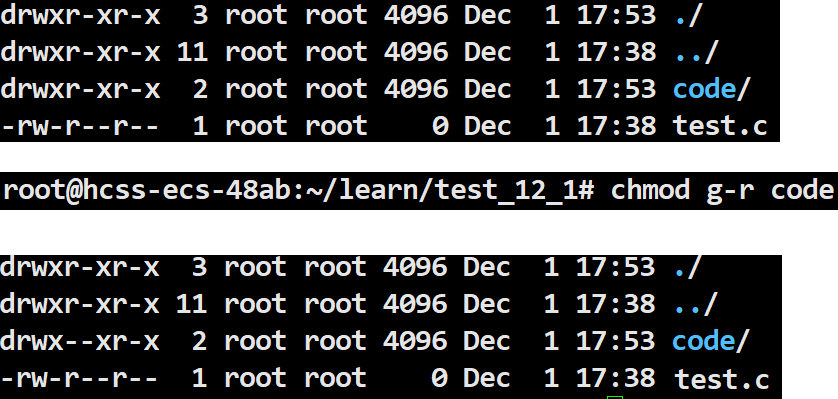
chmod g+r code
This modifies the read permission for the group of the file code from not allowed to allowed.
root@hcss-ecs-48ab:~/learn/test_12_1# chmod g+r code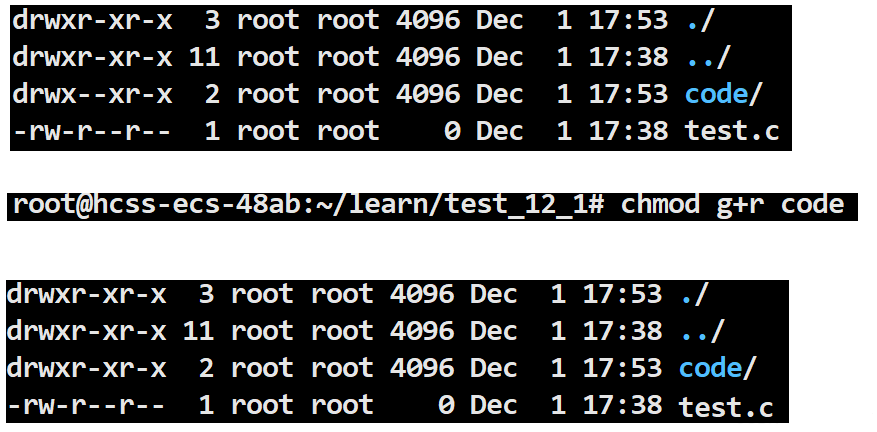
Earlier, we learned about numeric expressions and the conversion between binary and octal. When modifying file access permissions, we can also modify them using octal.
Octal is 666, binary is 110 110 110, which is rw- rw- rw-.
root@hcss-ecs-48ab:~/learn/test_12_1# chmod 666 code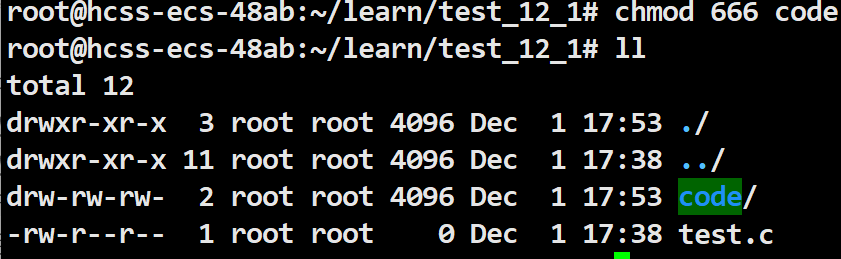
Note:
Users can only modify their own file permissions.
If you do not have permission, the system will refuse to let you access.
When determining permission information, the system will determine the user role and only determine it once. The determination is done in order from owner, group, to others.
The root user’s permissions are not restricted.
The above describes a series of executions; executable permissions != file executable.
Modify File Owner or Group (chown and chgrp)
chown changes the owner of a file/directory.
chgrp changes the group of a file/directory.
Change the owner of the code file from the root Super User to a Regular User.
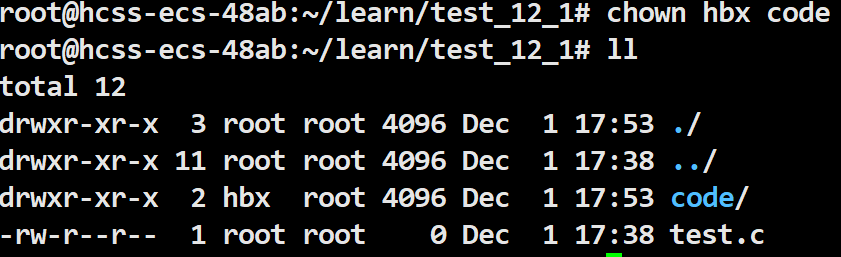
Change the owner of the code file from a Regular User to a Super User.
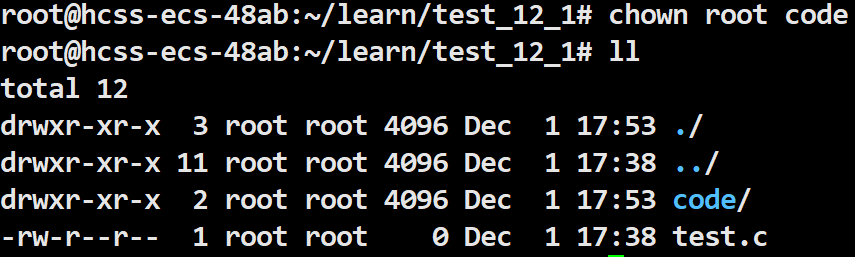
Change the group of the code file from Super User to Regular User.
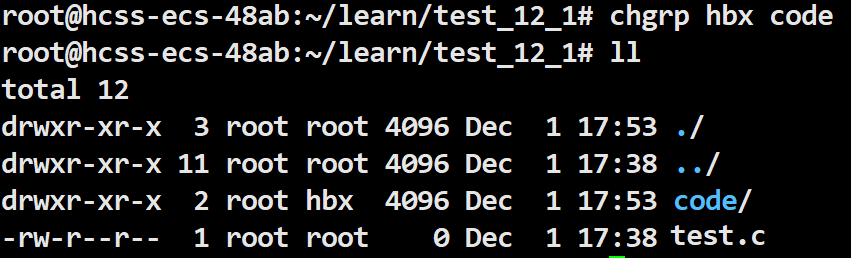
Change the group of the code file from Regular User to Super User.
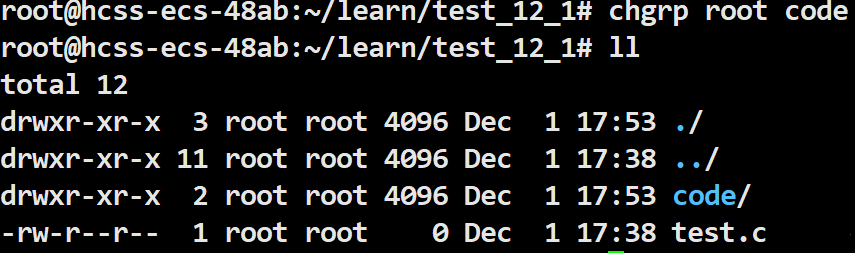
Note:
When we are Regular Users, the system defaults do not allow us to transfer files to others. If you want to give files to others, you must elevate permissions.
When a Regular User wants to transfer files to others, it is not allowed.
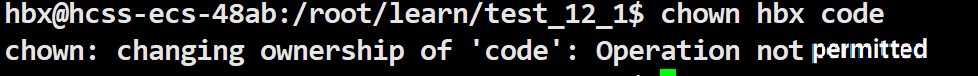
2.3 Directory Permissions
Earlier we learned about directory types; those starting with d are directories, while those starting with – are files.
Note: This refers to Regular Users; Super Users are not restricted.
If a directory does not have r, you cannot view the files in the directory.
If a directory does not have w, you cannot create files in the directory.
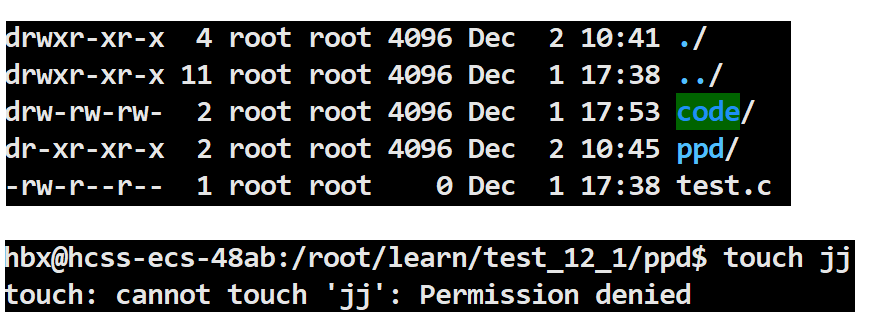
2.4 Default Permissions
For regular files, the initial permission is 666, which does not include execute permission by default.
For directory files, the initial permission is 777, which includes execute permission by default.
umask Permission Mask
Final Permission = Initial Permission & (-umask)
The purpose of umask is that any permissions appearing in umask should not appear in the final permissions.
The default permissions are determined autonomously by the operating system and cannot be modified before creation. By using umask, the system can be configured flexibly to meet the required situations. Configuring umask allows controlling the default permissions of files, making our code manageable.
2.5 Sticky Bit
In a Regular User’s directory, when creating a Regular User file and a Super User file, the access permissions of the Regular User file relative to the Super User file are Others. Under a Regular User, operations can be performed on the Super User file based on rwx. When the access permissions of the Super User file for Others are modified to not writable, not readable, and not executable, the Regular User can no longer perform any operations on the Super User’s file. However, the Regular User can delete this file. This leads to the conclusion that whether a file can be deleted is not related to the file itself, but to the w permission of the directory in which it resides.
When two users need to share a file, the tmp directory is a public directory in a multi-user environment. A public directory is created under the tmp directory. At this point, both users can modify it, and of course, users outside of these two can also modify this file. This is where the Sticky Bit comes into play.
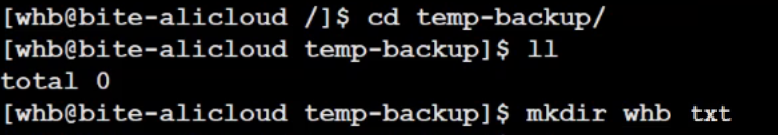
In the Linux system, the Sticky Bit is a special permission bit mainly used to control the deletion operation of files in specific directories. After setting the Sticky Bit, the current user can only delete their own shared files and cannot delete another user’s shared files. Only the file owner or root user can delete or move the file, while other users, even with write permissions, cannot delete or move these files.
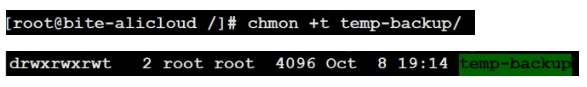
When a directory is set to “Sticky Bit” (using chmod +t)
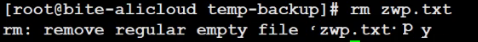
chmod +t directory # Set Sticky Bit for the directorychmod -t directory # Remove Sticky Bit for the directoryDelete shared files under the tmp directory, root deletes.
For course inquiries, add: HCIE666CCIE
↓ Or scan the QR code below ↓
What technical points and content do you want to see?
You can leave a message below to tell me!