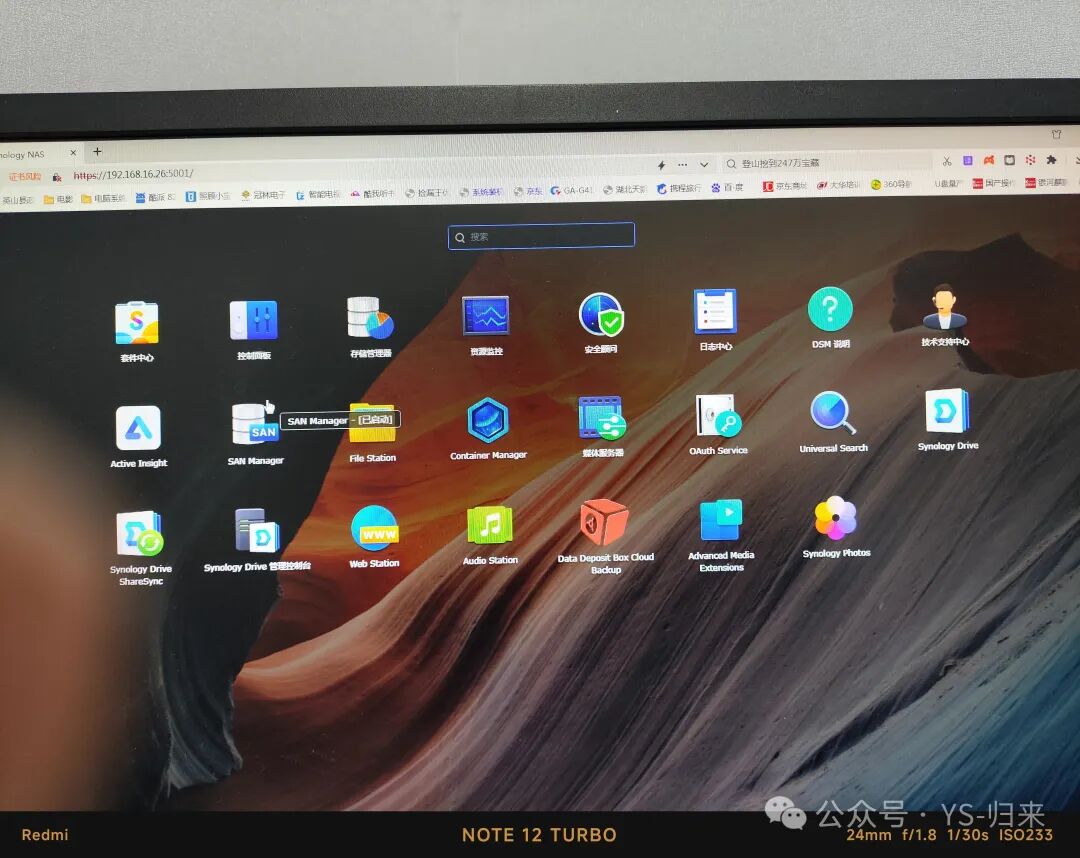
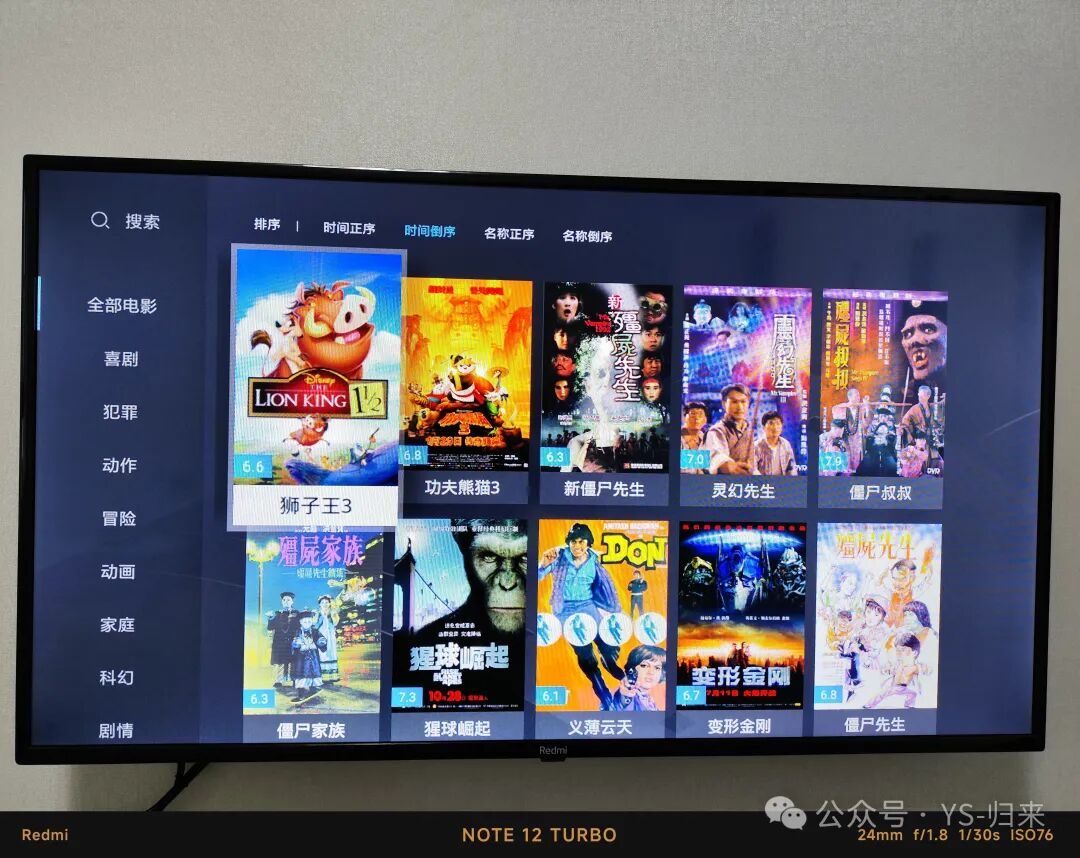
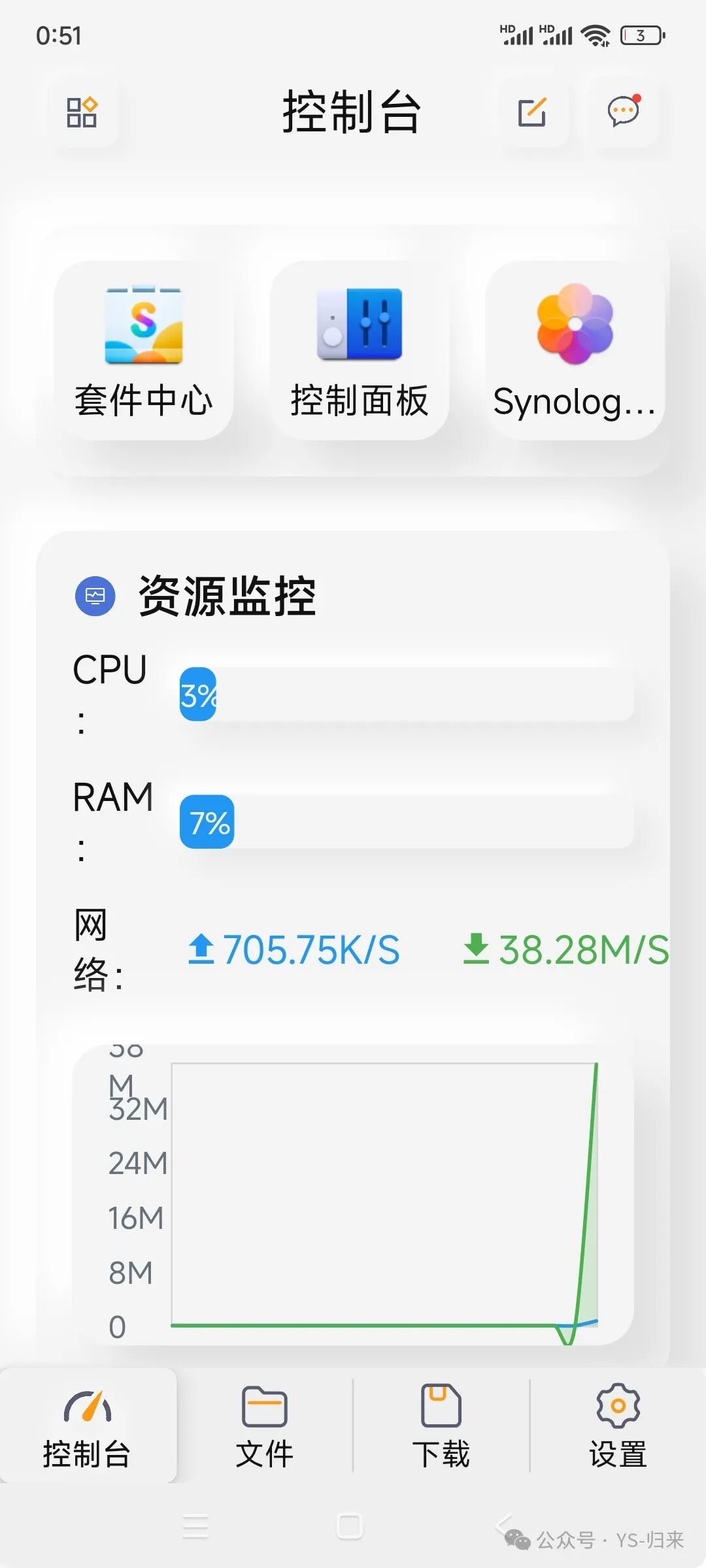
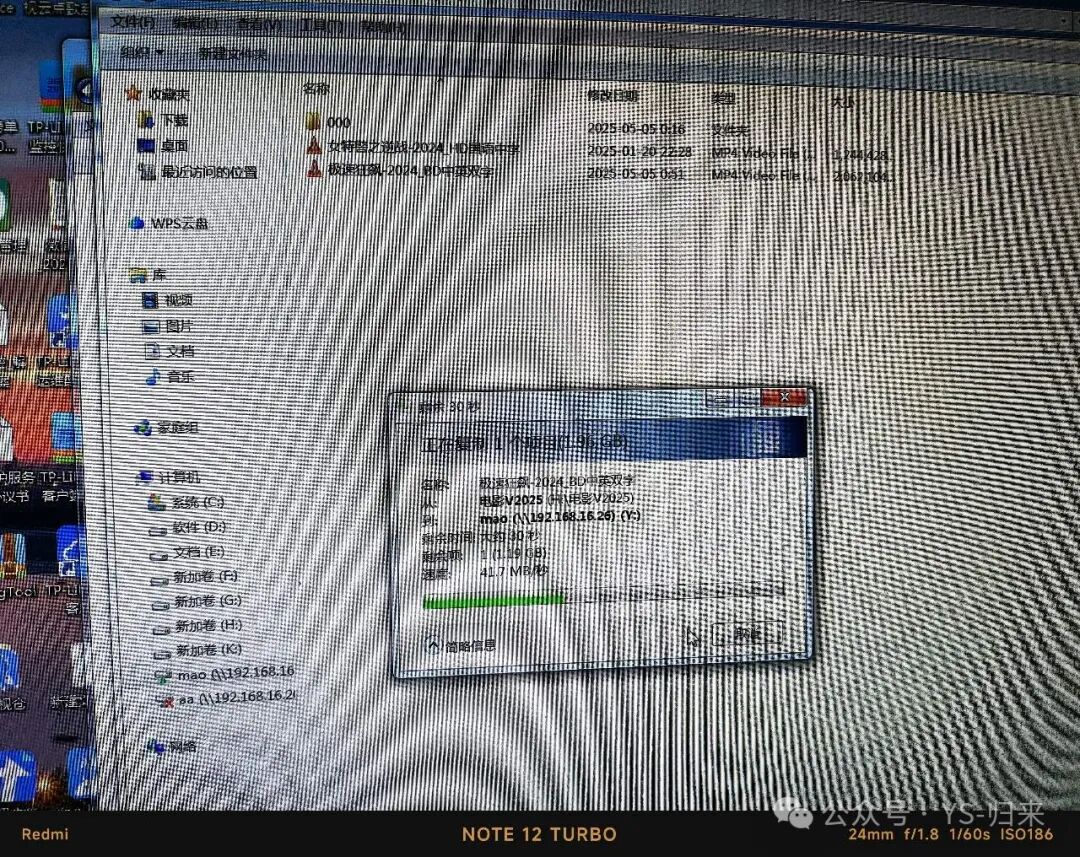
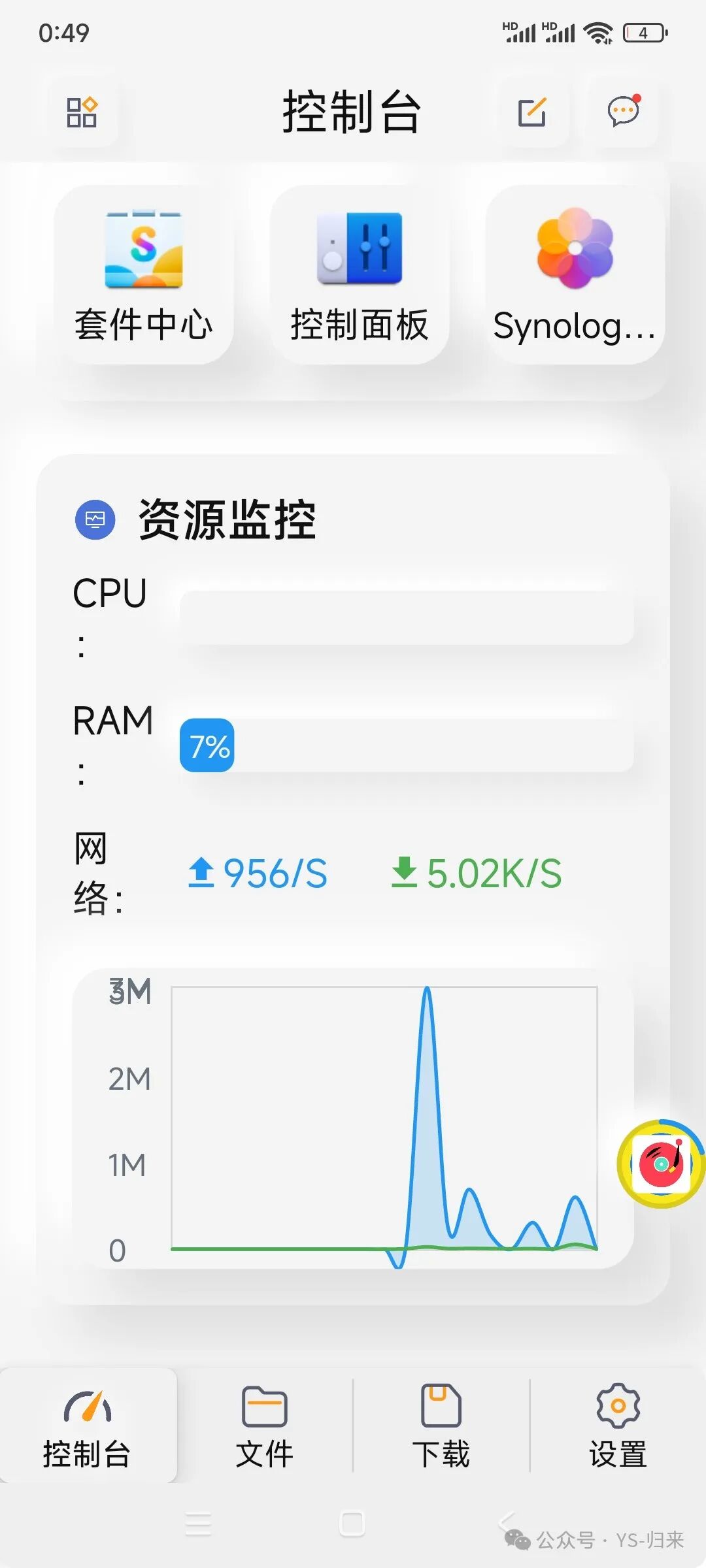

Related posts
- Linux io_uring Proof-of-Concept Rootkit Bypasses System Call-Based Threat Detection Tools
- How to Transform an Old Android Phone into a Home Server
- Understanding the HTTP/3 Protocol
- Python Indentation Rules: Writing Standards for Improved Code Readability
- Practical Guide to Integrating and Applying the National Encryption Algorithm SM4 in Financial Systems
- Testing Methods for CAN Bus on Linux Development Boards: Demonstration with the Haptic Intelligence RK3568 Development Board
- Linux Power Management (3) – The Process of Shutdown and Reboot
- The Emergence of AI Writing: How Long Can Human Writers Persist?
- A Quick Overview: Can We Discuss HTTP and HTTPS?
- Comprehensive Analysis of Linux Permissions: An Essential Guide from Beginner to Expert!
- Smart Home: A New Way of Living
- Can a Large Screen Become a Touchscreen? This Smart Projector ‘Innovator’ Explores New Uses for Big Screens
- Smart Home Scene Setup Guide: The Secret to One-Click Control of All Home Appliances
- Transforming Electricians into Smart Home Experts: A Journey of Success
- A Must-Read for Tech Enthusiasts! Build a Home Server with an Idle Computer and Earn Money
- 100 Essential Virtualization Concepts
- How to Choose Microcontroller Languages for Hardware, Software, and IoT Engineers?
- Heat Management and Safety for Home Servers and Network Devices: Special Protection for 24/7 Operating Equipment