Introduction to Ansible
Ansible is an open-source automation tool developed by Red Hat for:
- • Configuration Management
- • Application Deployment
- • Automated Task Execution
- • Batch Operations on Multiple Servers
Its main features are: Agentless + SSH-based connection + YAML scripting (high readability).
Why Choose Ansible?
| Feature | Description |
| ✅ Agentless | No agent installation required on managed nodes, operations are performed directly via SSH |
| ✅ Easy to Learn | Playbooks are written in YAML, which is highly readable |
| ✅ Rich Modules | Built-in and community modules support various platforms and tasks |
| ✅ Cross-Platform | Manages Linux, Windows, network devices, etc. |
| ✅ Extensible | Supports custom modules and a plugin system |
| ✅ Active Community | Rich open-source resources and documentation available |
What Can Ansible Do?
- • Batch deployment of software (e.g., installing nginx, mysql)
- • Configuration file distribution and template replacement
- • Restarting services, managing users, configuring firewalls, etc.
- • Automated deployment of web applications, containers, cloud services (AWS, Azure)
- • Orchestrating cross-host tasks (e.g., deploying Hadoop, K8s, Ceph)
Ansible Architecture
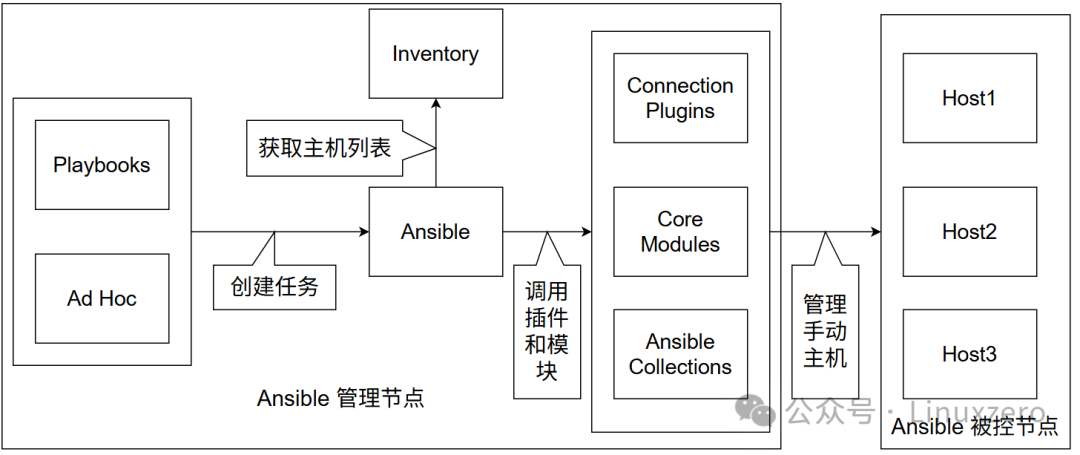
The Ansible control node is responsible for issuing tasks and includes the following components:
- • Ansible: Ansible-core, the main program of Ansible, includes related binaries
- • Inventory: A list of hosts used to define the managed servers
- • Ad Hoc: Ansible’s command line for executing simple tasks or debugging
- • Playbooks: Scripts used to define complex automation tasks
- • Core Modules: The essential modules of Ansible, which include the most commonly used modules (prior to Ansible 2.10, many modules were included, but only a few core modules are included after 2.10)
- • Ansible Collections: Core modules only meet basic functionality; new modules can be installed via Ansible Collections to extend Ansible’s capabilities
- • Connection Plugins: Connection plugins define how Ansible connects to remote hosts
The process of managing hosts with Ansible:
- 1. Ansible defines the host list through Inventory
- 2. Tasks are defined through Playbooks or Ad Hoc (tasks are executed via modules) and the hosts on which tasks will be executed
- 3. Modules are pushed to the managed nodes via connection plugins
- 4. Tasks are executed on the managed nodes, and the modules are deleted after execution
Most of Ansible’s modules are idempotent, meaning that executing them multiple times will only modify what needs to be changed. However, some modules, such as
<span>raw</span>,<span>command</span>, and<span>shell</span>modules, are exceptions.The Ansible control node must be a Linux system.
Devices and Connection Methods Managed by Ansible:
| Device Type | Default Connection Method | Description |
| Linux Systems | SSH | The most common method, supports passwordless or key-based login |
| Windows Systems | WinRM | Requires configuration of the WinRM service, supports HTTP/HTTPS |
| Network Devices | SSH or API | Uses specific modules/collections; some devices require NETCONF |
| Cloud Platforms | API (HTTPS) | Utilizes SDK/REST API, requires Access Key, Token, etc. |
| Kubernetes / OpenShift | API Server | Connects to kube-apiserver using kubeconfig or Token |
| Docker / Podman | Local or Remote API | Connects via Unix socket or remote TCP port |
| Storage/Virtualization Devices | API or SSH | e.g., VMware uses vCenter API, Dell EMC uses REST API |
| HTTP Services | URI Module | <span>ansible.builtin.uri</span> can call REST interfaces |
| Custom Services | Command/Script/API | Can use <span>command</span>, <span>shell</span>, or <span>script</span> modules to invoke |
Ansible uses the available connection methods of the managed nodes to manage them, such as managing Linux via SSH, which is why Ansible is agentless and does not require an agent to be installed on the managed nodes.