Recently, Siemens announced that its industrial equipment, commonly used in petrochemical plants and large renewable energy power plants, has 54 security vulnerabilities. Among these, the most severe vulnerabilities can be exploited for denial-of-service (DoS) attacks or remote code execution on arbitrary servers, putting power plants at risk of failure and halting electricity generation. More alarmingly, the affected product, the SPPA-T3000 distributed control system, is widely deployed in major power plants across the United States, Germany, Russia, and other countries, which means that global power plants may face a significant crisis.

54 Critical Vulnerabilities Exposed in Siemens Industrial EquipmentGlobal Power Plants May Face Major BlackoutsThe Siemens SPPA-T3000 distributed control system is designed specifically for petrochemical and large renewable energy power plants and is widely used in power plants in the United States, Germany, Russia, etc., to coordinate and supervise power generation.

However, recently, Siemens issued a global announcement stating that: the SPPA-T3000 application server has 19 vulnerabilities, and the SPAA-T3000MS3000 migration server has 35 security vulnerabilities. Among these 54 vulnerabilities, some are rated as critical vulnerabilities that can be exploited for denial-of-service (DoS) attacks or to execute arbitrary code on the server.

During a media announcement last Thursday, Vladimir Nazarov, head of industrial control security at Positive Technologies, also stated:
“By exploiting these vulnerabilities, attackers can run arbitrary code on the application server, thereby taking control and disrupting operations. This could halt power generation and cause failures in power plants with vulnerable systems.”
It is worth noting that critical vulnerabilities can trigger remote code execution issues on applications, initiating RCE.
For example, CVE-2019-18283 is a severe untrusted data deserialization vulnerability that allows attackers to “gain remote code execution privileges by sending specially crafted objects to one of its functions.”
In addition to the above attacks, researchers have also found that by exploiting these vulnerabilities, attackers can obtain and change user passwords, retrieve directory listings and files containing sensitive information, escalate privileges to ROOT, enumerate running RPC services, upload arbitrary files without authentication, read and write arbitrary files on the local file system, access paths and filenames on the server, enumerate usernames, and access logs and configuration files, among other malicious operations.
Unfortunately, according to foreign media reports, as of now, Siemens has only patched three of these vulnerabilities.
The threat remains, and a large-scale global blackout may be imminent.
Facing the Challenge of Critical VulnerabilitiesEnsuring the Safety of “Partners” While Guarding Against “Insiders”Although the threat of vulnerabilities still exists, Siemens stated in its report that to exploit these vulnerabilities, attackers would need access to the Application Highway or Automation Highway in the PROFIBUS protocol (PROFIBUS protocol: a fieldbus standard used in automation technology). If the system is configured according to the product security manual, these network segments will not be exposed. In simple terms, these vulnerabilities are difficult to exploit from the outside.
Therefore, from another perspective, if an attacker launches an attack, they are most likely to do so through one of the following two methods:
First Method: “Indirect Attack” Tactics
Starting with infiltrating partners, then using the partner’s IT system to launch an attack on the ultimate target power station.
On January 10, 2018, The Wall Street Journal published an article stating that Russian hackers frequently attack the U.S. power grid system, but they do not directly invade; instead, they target power grid contractors with weaker defenses.
Specifically, hackers first infiltrated equipment manufacturers and suppliers of critical infrastructure like the power grid through spear-phishing to obtain login credentials or by installing malware on their machines via deceptive web pages. Subsequently, hackers took further lateral movement and ultimately obtained information about industrial control systems and energy production facility outputs from monitoring and data acquisition systems.
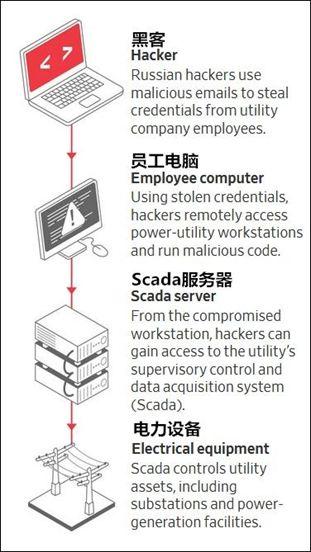
Second Method: “Insider Attack” Method
There is also a typical case—the “Stuxnet” incident that forced the Iranian nuclear power plant to “abort.” The initial infection of the virus was due to an “insider” hired by the Dutch intelligence agency.
At that time, the Dutch spy disguised as a maintenance worker successfully infiltrated Natanz. Although his work did not directly involve the centrifuges, the spy took advantage of multiple opportunities to enter Natanz over several months to continuously gather relevant information, helping the team developing the cyber weapon to formulate precise attack plans.
Additionally, the network of Iranian centrifuges is isolated, and centrifuge engineers use USB drives to transfer code into the centrifuge network. Therefore, security experts speculate that the spy either directly plugged the USB drive into the centrifuge network or infected the engineer’s storage device, allowing the engineer to bring in the infected code.
From the above analysis, it can be seen that even if Siemens officially states that these vulnerabilities are difficult to exploit from the outside, “partners” and “insiders” (including suppliers, employees, or any third-party collaborators) will be important breakthrough points for hackers to launch attacks. Therefore, security is never absolute, static, or individualized.
Thus, in the face of any vulnerabilities and hacker attacks, we must remain vigilant, especially when critical infrastructure like industrial control systems is under threat; we cannot afford to be complacent.
We must apply holistic thinking, adopt a proactive offensive and defensive perspective, and use dynamic models; integrate global security big data, threat intelligence, and knowledge bases to achieve a network security defense capability that is “visible and defensible,” relying on resources such as advanced threat response security experts to comprehensively combat increasingly complex cyber attack issues.
References:
“Flaws in Siemens SPPA-T3000 Control System Make Power Plants Vulnerable to Hackers”
https://www.securityweek.com/hackers-can-exploit-siemens-control-system-flaws-attacks-power-plants
“Russian Government Cyber Activities Targeting Energy and Other Critical Infrastructure Sectors”
https://www.us-cert.gov/ncas/alerts/TA18-074A
Original Source: International Security Think Tank
