01Introduction
This academic sharing is based on research work published by researchers from Shanghai University of Technology and others in the IEEE TRANSACTIONS ON AUTOMATIC CONTROL in 2025.
Paper Title:Stochastic Important-Data-Based Attack Power Allocation Against Remote State Estimation in Sensor Networks
Authors:Engang Tian, Mengge Fan, Lifeng Ma, and Dong Yue
Source:IEEE TRANSACTIONS ON AUTOMATIC CONTROL, IF: 7.002, Top Journal in the 2nd District of the Chinese Academy of Sciences JCR.DOI: 10.1109/TAC.2024.3477009
Value Rating:
Method Innovation: ★★★★★: This paper first proposes aStochastic Important Data-Based (IDB) attack strategy and its corresponding energy allocation method. Compared to traditional DoS attacks, this method captures key information in transmitted data packets, selects attack targets based on the “importance index” of prediction errors, and employs a random triggering mechanism to enhance concealment. It significantly outperforms existing uniform power allocation models in terms of attack effectiveness, energy efficiency, and concealment.
Engineering Value: ★★★☆☆: The paper validates the effectiveness of the proposed strategy through simulation experiments and compares it with the classic Bernoulli distribution DoS attack in terms of attack energy efficiency. However, practical deployment still faces challenges such as system dependency, dynamic information capture, and energy control constraints.
Theoretical Depth: ★★★★☆: The paper systematically constructs a complete theoretical framework from attack strategy, power allocation, performance analysis to optimization constraints, covering the establishment of prediction error-driven indicators, stochastic analysis, and optimization parameter design under energy constraints. It rigorously derives the relationship between estimation performance and attack parameter σ, and provides equilibrium solutions under attack-defense games.
Further Reading:
1. Classic: H. Zhang, P. Cheng, L. Shi, and J. Chen, “Optimal denial-of-service attack scheduling with energy constraint” (2015) This paper systematically studies the optimal DoS attack scheduling strategy in remote state estimation systems, proving the maximum destructiveness of continuous DoS attacks in specific scenarios. It lays the theoretical foundation for subsequent attack strategies based on important data.
2. Cutting-edge: X. Wang, E. Tian, W. Zheng, and X. Xie, “Important-data-based DoS attack mechanism and resilient H∞ filter design for networked T-S fuzzy systems” (2023) This research is in line with this paper, proposing an important data-based DoS attack mechanism for T-S fuzzy systems and designing a robust H∞ filter. It represents the current cutting-edge direction in attack-defense game research in complex network environments.
3. Controversial: D. Ye and Y. Song, “Optimal periodic DoS attack with energy harvester in cyber-physical systems,” (2020) This paper introduces the assumption of an “energy harvester” and proposes the optimal design of periodic DoS attacks. Although innovative, its assumption that the attacker has continuous energy replenishment capability (through energy harvesting) is difficult to achieve in actual industrial networks and complex environments, leading to academic controversy over its feasibility.
This paper proposes a novel Stochastic Important Data-Based (IDB) DoS attack strategy and its corresponding power allocation method, aimed at disrupting the estimation performance of remote state estimation systems in sensor networks. The innovation lies in its use of prediction error information in transmitted data packets to calculate the “importance index,” prioritizing attacks on key data packets that have the greatest impact on system performance through a random triggering mechanism, significantly enhancing attack concealment and destructiveness. It also designs an energy allocation method based on signal-to-noise ratio (SNR), achieving optimal attack power allocation across different channels under energy constraints. It establishes an analytical relationship between attack parameters, estimation performance, and energy constraints, providing an analytical expression for the attack parameter σ and its optimal value under constraints. Simulation results validate that the proposed method has higher attack effectiveness compared to Bernoulli distribution DoS attacks under the same attack energy.
This research not only enriches the security research of industrial control systems from the attacker’s perspective but also provides a novel theoretical framework and practical methods for network security defense.
02Research Gene
This paper has made substantial progress in theoretical innovation and algorithm design, first integrating data-driven mechanisms with random triggering strategies, proposing a prediction error-driven DoS attack model, specifically targeting remote state estimation in sensor networks. Unlike traditional uniform attack schemes, this paper identifies key data packets with larger prediction errors and allocates higher attack power to these “important data,” greatly improving attack efficiency and concealment. Meanwhile, the study also designs algorithms that can optimize attack parameters under limited energy constraints, deriving analytical expressions for the upper limits of attack intensity, establishing a complete mathematical theoretical chain. Simulation results further demonstrate the superiority of this method over traditional schemes under the same attack energy conditions, highlighting its leading advantages in attack efficiency and concealment.
At the same time, other research teams focus on network security issues under event-triggered control, especially in scenarios where nodes in sensor networks are compromised or data packets are lost, designing adaptive event-triggered filters to enhance the system’s anti-interference and self-healing capabilities under DoS attacks. Such research primarily starts from the defender’s perspective, ensuring input-to-state stability (ISS) and bounded estimation error of the system under abnormal conditions through theoretical derivation and stability analysis. In contrast, this paper innovatively combines prediction error information with random triggering mechanisms from the attacker’s perspective, proposing a more concealed and efficient attack scheme, opening up a new direction for sensor network security research.
03Literature Background
Core challenges currently existing in this field:
1. Lack of attack design oriented to system characteristics: Most current DoS attack strategies fail to integrate the characteristics of the target system (such as key parameters for state estimation), resulting in insufficient exploitation of attack effectiveness.
2. High predictability of attacks: Traditional attack strategies are mostly based on fixed or periodic scheduling, making them easy to be anticipated and intercepted by monitoring and defense systems, lacking sufficient dynamic variation.
3. Insufficient resource allocation mechanisms: Existing models often rely on empirical rules or heuristic optimization when dealing with energy-constrained attack scenarios, lacking systematic theoretical analysis and algorithmic support.
Breakthrough Points:
This paper proposes a new attack strategy design concept around the vulnerabilities of remote estimation in sensor networks, effectively addressing the above challenges through the following key innovations:
1. Target selection based on prediction feedback: Designed an attack indicator that integrates system output and prediction residuals, achieving a priority attack strategy based on dynamic feedback, significantly enhancing attack effectiveness.
2. Random perturbation enhances concealment: Introduced random perturbation factors to disturb attack behavior, significantly reducing the predictability and detectability of attack patterns.
Theoretically supported energy management: Proposed a rigorous theoretical framework, establishing mathematical relationships between attack intensity, impact range, and energy consumption, providing systematic solutions for attack scheduling under limited energy.
04Research Methodology
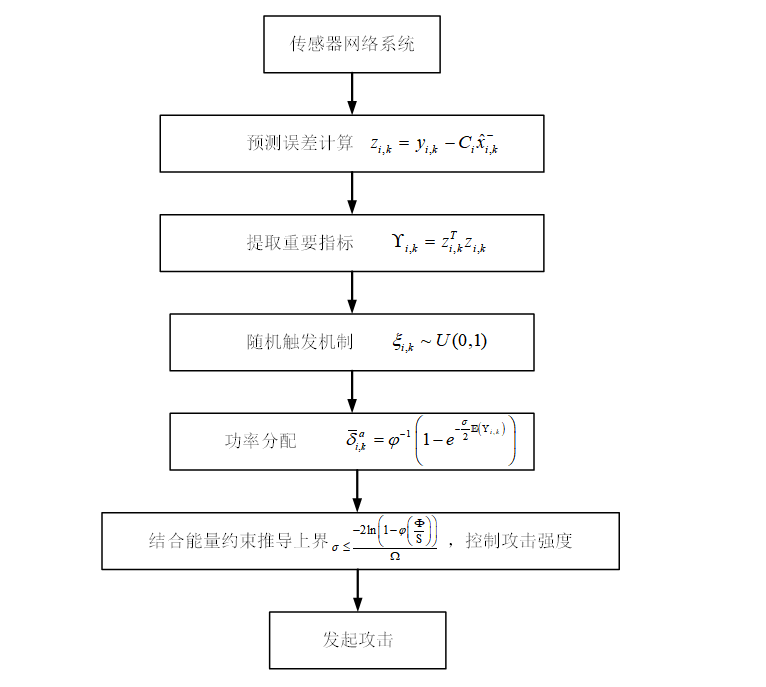
This paper focuses on the performance degradation of remote state estimation systems in sensor networks under DoS attacks, abstracting the performance degradation problem into a prediction error-driven stochastic important data-based (IDB) DoS attack model. The system consists of multiple sensors that communicate with a centralized estimator via a wireless network. Due to DoS attacks, some data packets are discarded, causing the estimator to be unable to receive all observation data, thereby reducing the accuracy of state estimation.
A. Sensor Network System Modeling:
The state model and observation model of the discrete-time linear system are:
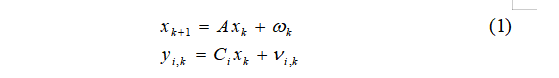
where 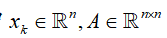 ,
,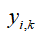 is the observation vector of sensor i,
is the observation vector of sensor i,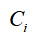 is the observation matrix,
is the observation matrix,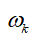 is zero-mean Gaussian process noise,
is zero-mean Gaussian process noise,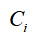 is the observation noise, and the covariance
is the observation noise, and the covariance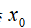 defines the initial state
defines the initial state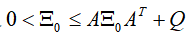 covariance matrix satisfies
covariance matrix satisfies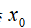 .
.
Remote State Estimator Design:
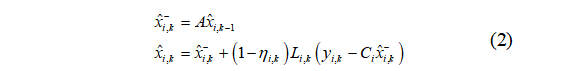
where the attack signal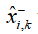 indicates that the observation is discarded,
indicates that the observation is discarded, indicates successful transmission of the observation.
indicates successful transmission of the observation.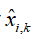 and
and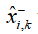 represent the prior and posterior state estimates on the i-th estimate,
represent the prior and posterior state estimates on the i-th estimate,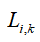 is the estimator gain matrix at the i-th node.
is the estimator gain matrix at the i-th node.
Define the estimation error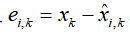 to obtain the estimation covariance
to obtain the estimation covariance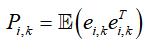 , define the initial state estimate
, define the initial state estimate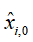 ,
, 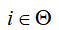 , assuming
, assuming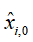 is 0, then
is 0, then is a non-zero mean Gaussian random vector.
is a non-zero mean Gaussian random vector.
Define centralized estimator and centralized error estimation:
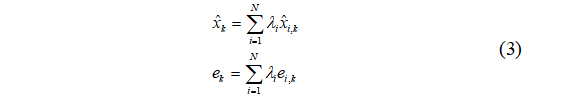
B. Random IDB Attack Strategy
Propose a random IDB attack strategy that can launch attacks based on the importance of data packets (IDP), that is, for important data packets, this strategy will adaptively increase the attack success probability (ASP).
Definition of prediction error (used to measure the importance of observations):
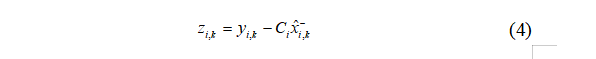
Design importance indicators: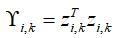
Define random attack triggering mechanism: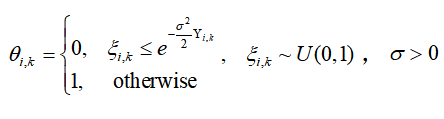 as the attack intensity parameter.
as the attack intensity parameter.
C. Random IDB Attack Power Allocation Technique
To implement the proposed IDB attack strategy and ensure that important data packets have a high ASP, a new IDB attack power allocation technique is proposed to prevent important data packets from being transmitted to the estimator as much as possible. Unlike some existing attack power allocation methods that allocate the same power to each attack, this technique can allocate more power to important data packets to ensure that the ASP of important data packets is higher than that of other packets.
Signal-to-noise ratio model and attack power allocation:
From the proposed random IDB attack strategy,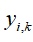 the ASP is
the ASP is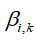 , injecting attack power into the i-th channel at time k
, injecting attack power into the i-th channel at time k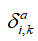 to achieve the desired ASP. The signal-to-noise ratio (SNR):
to achieve the desired ASP. The signal-to-noise ratio (SNR):
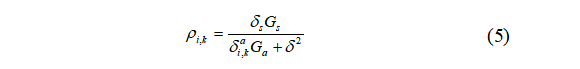
where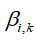 is the SNR of the i-th channel at time k;
is the SNR of the i-th channel at time k; 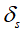 and
and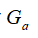 are the transmission power and noise power of the sensor, respectively;
are the transmission power and noise power of the sensor, respectively;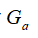 and
and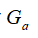 are the channel gains from the sensor and attacker to the MMSE estimator, respectively.
are the channel gains from the sensor and attacker to the MMSE estimator, respectively.
Based on (2) and (5), the probability of attack failure is
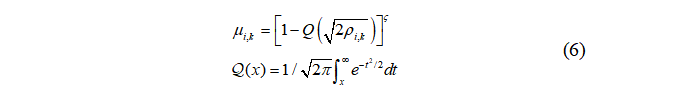
where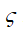 is the bit of the data packet, which can be obtained
is the bit of the data packet, which can be obtained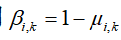 .
.
Define performance metrics:
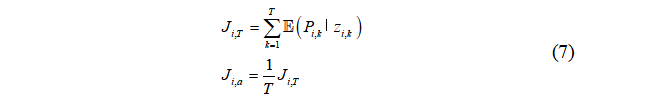
The larger the metric, the worse the estimation accuracy.
D. Core differences from conventional problem definitions:
Compared to conventional DoS attack models, the core differences in this paper include:
Data-driven mechanism: Introduces prediction error as an importance indicator, dynamically selecting high-impact data packets for attack, achieving “differentiated” attacks.
Random triggering mechanism: Uses random variables to control the attack triggering probability, avoiding periodic patterns and enhancing concealment.
Theoretically driven energy constraint analysis: Derives closed relationships between attack parameters and attack success rates, constructing optimal attack parameter solutions under energy constraints.
From the attacker’s perspective: Unlike traditional designs from the defense perspective, this paper focuses on the attacker’s perspective, identifying important data packets through prediction errors and optimizing attack resource allocation to enhance destructive effectiveness.
3. Method Innovation
Technical Route:
The technical route is divided into the following key steps:
1. Prediction error calculation: Calculate the prediction error in real-time based on sensor observations and local estimates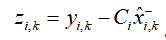 .
.
2. Importance indicator extraction: Perform a sum of squares operation on the prediction error to obtain the importance indicator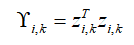 .
.
3. Random triggering design: Based on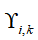 and attack parameters, use random variables
and attack parameters, use random variables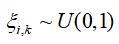 to implement attack triggering determination
to implement attack triggering determination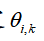 .
.
4. Signal-to-noise ratio and power allocation: Based on channel characteristics and energy constraints, dynamically allocate attack power through inverse functions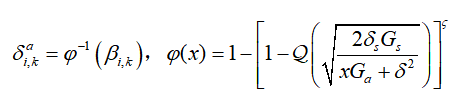 .
.
5. System constraints and optimization: Combine total energy constraints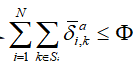 with estimator performance indicators, there exists
with estimator performance indicators, there exists 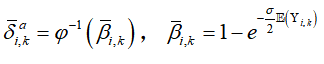 . Derive the closed upper bound of attack parameters, that is:
. Derive the closed upper bound of attack parameters, that is:
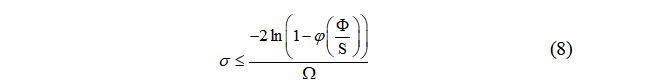
where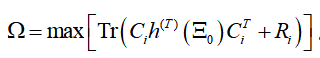 .
.
Design Details:
Prediction error-driven importance indicators: Use prediction errors to construct key packet identification indicators, achieving priority attacks on data that have a greater impact on system performance compared to traditional models of “indiscriminate attacks.”
Random triggering mechanism: Introduce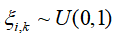 to control triggering probability, avoiding periodic attacks and enhancing concealment.
to control triggering probability, avoiding periodic attacks and enhancing concealment.
Theoretical closed optimization: Under the total energy constraint Φ, establish closed relationships between attack parameters and system performance indicators, analytically derive optimal attack intensity.
Signal-to-noise ratio-driven power allocation: Utilize parameters such as sensor and attack channel gains, transmission power, and system noise to dynamically adjust attack power, achieving efficient energy utilization.
Implementation Principle:
The attack strategy utilizes prediction error information to identify key data packets, enhances concealment through random triggering mechanisms, and optimizes attack power based on signal-to-noise ratio theory and energy constraints. This strategy achieves efficient disruption of remote state estimation systems in sensor networks and has strong theoretical and engineering applicability.
05Experimental Section
A. Description of Experimental Objects:
The parameters of the experimental objects are as follows:
The experimental object is a simulated sensor network remote state estimation system, which includes three sensor nodes, corresponding parameters are:
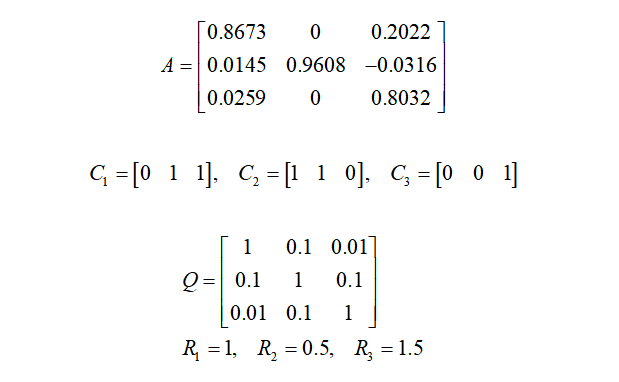
Sensor transmission power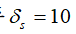 , channel gain
, channel gain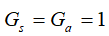 , noise power
, noise power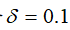 , data packet length
, data packet length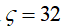 .
.
B. Reasonableness Analysis of Benchmark Comparison Experiment Design
To verify the effectiveness of the proposed random important data-based (IDB) attack strategy, the following comparative experiments were designed:
1. The benchmark scheme adopts the traditional Bernoulli distribution DoS attack strategy, that is, randomly attacking all data packets with a fixed probability, without distinguishing priority.
2. The proposed scheme adopts the IDB attack strategy, dynamically identifying key data packets and allocating attack power under the same energy consumption constraints.
3. Comparison metrics include average attack success rate (ASR) and system estimation error increment. Simulations are repeated multiple times to ensure statistical reliability.
The experimental results show that under the same attack energy, the IDB strategy achieves greater system performance degradation, verifying its effectiveness and advantages.
C. Most Convincing Data Metrics
Metric Name:
Average Destruction Metric F: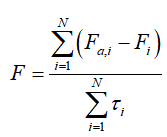 , this metric intuitively reflects the degree of degradation in system state estimation performance caused by the attack. This metric comprehensively considers attack effectiveness and frequency, accurately reflecting the average destructiveness of the attack, fully demonstrating the advantages of the IDB strategy over traditional uniform attack strategies under the same attack energy.
, this metric intuitively reflects the degree of degradation in system state estimation performance caused by the attack. This metric comprehensively considers attack effectiveness and frequency, accurately reflecting the average destructiveness of the attack, fully demonstrating the advantages of the IDB strategy over traditional uniform attack strategies under the same attack energy.
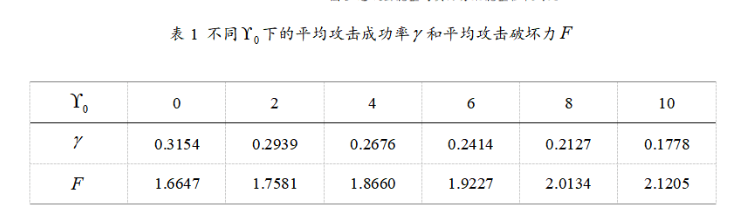
The experimental results show that as the importance threshold increases, although the attack success rate decreases, the average destruction significantly increases, indicating that prioritizing attacks on key data packets can significantly enhance destructive effects.
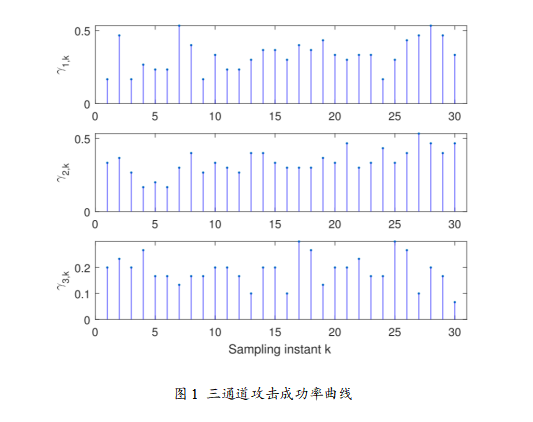
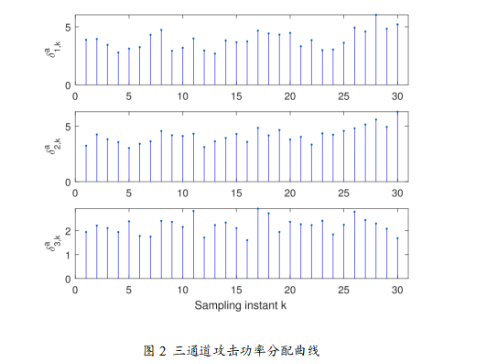
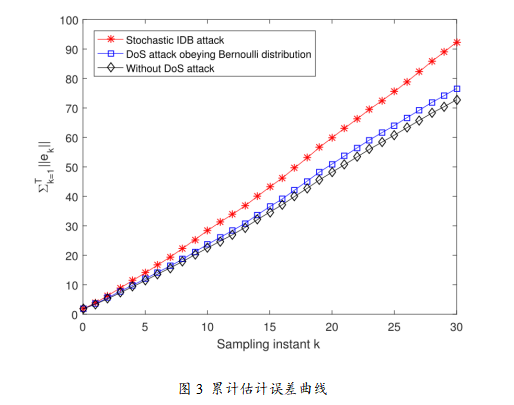
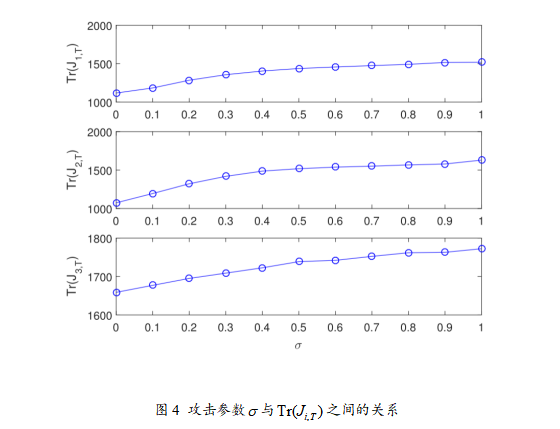
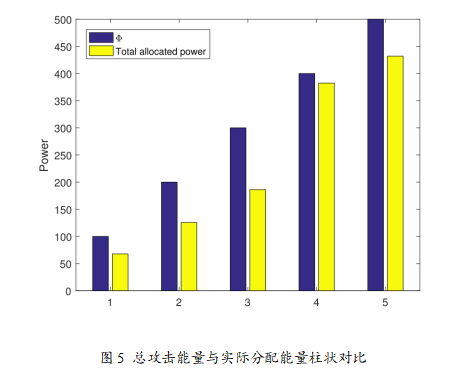
The experimental results of this paper clearly demonstrate the advantages of the random important data-based (IDB) DoS attack strategy through multiple graphs. First, Figure 1 shows the attack success rate curves for different channels, indicating that the IDB strategy can dynamically adjust the attack success rate based on the importance of data packets, with the highest success rate in channel 2, reflecting the key data identification capability driven by prediction errors. Figure 2 displays the attack power allocation curves for each channel, further illustrating that the IDB strategy allocates more power to important data packets, validating the dynamic power allocation effect driven by signal-to-noise ratio. Figure 3 compares the cumulative estimation errors under no attack, Bernoulli random attack, and IDB strategy, showing that the system estimation performance degrades the most under IDB attacks, confirming the conclusion that the IDB strategy can achieve greater destructiveness under the same energy. Through Table I and the destruction metric, it further demonstrates that as the importance threshold increases, the average attack success rate decreases, but the average destruction increases, validating the efficiency of prioritizing attacks on key data. Figure 4 depicts the growth trend of the covariance trace of system estimation error under different attack intensity parameters, proving that increasing attack intensity leads to greater system performance degradation. Finally, Figure 5 uses bar charts to compare the theoretical maximum attack energy and actual allocated energy under different total energy constraints, indicating that the IDB strategy achieves reasonable power allocation while ensuring energy constraint conditions, ensuring feasibility and efficiency.
In summary, the experimental results fully validate the theoretical design and practical effects of the random IDB attack strategy, demonstrating its advantages in attack efficiency, concealment, and energy management.
Insights and Questions
Question: Is the real-time acquisition of the importance indicator driven by prediction errors feasible in practice?
The attack strategy in this paper relies on real-time calculations of prediction errors to determine the importance of data packets; however, this requires the attacker to have access to the internal state and observation values of the system. In real sensor networks, it is difficult for attackers to continuously capture sufficient system state and observation information without interrupting or exposing themselves. This premise is reasonable in theory but poses significant implementation barriers in engineering practice, potentially affecting the feasibility of the strategy.
The implicit assumptions of the methodology may affect its universality, mainly reflected in the following aspects:
Assumption 1: The attacker can accurately and in real-time obtain sensor observations and prediction errors
This is an ideal condition in theoretical modeling; in practical applications, it requires invading the network to obtain data, facing multiple challenges such as system defense, concealment, and data integrity.
Assumption 2: The channel model (SNR, channel gain) is known and stable
Attack power allocation relies on the calculation of SNR and known channel parameters; however, in dynamic or complex networks, channel conditions change over time, and attackers may not be able to accurately grasp these parameters, affecting the accuracy of attack power allocation and attack effectiveness.
Assumption 3: The system adopts an ideal linear model and Gaussian noise distribution
Actual systems may have nonlinear and non-Gaussian characteristics, and the prediction error indicators and power allocation models established based on linear system assumptions may not be applicable in complex systems, potentially affecting the universality of the strategy.
Summary
For the remote state estimation problem in sensor networks, this paper proposes a new attack strategy, namely random IDB attack, and studies the corresponding attack power allocation problem. This attack strategy improves destructiveness by allocating more power to important data packets. Based on signal-to-noise ratio theory SNR, the attacker allocates power according to known attack success probabilities. By analyzing the impact of attack parameters on estimation quality and total attack power, suitable attack parameters are obtained to maximize attack destructiveness under given energy constraints. Simulation results demonstrate the effectiveness of this method.
Deep Thinking
1. Technology Transfer
A. Adjustment and Adaptation Modules:
Prediction error calculation module: For different systems (nonlinear systems, distributed systems), it is necessary to redefine the calculation formula for prediction errors and importance indicators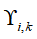 .
.
Channel model and power allocation strategy: For different physical networks, it is necessary to reset the SNR calculation method and channel gain parameters to adapt to dynamically changing complex environments.
Random triggering mechanism parameters: In new scenarios, it may be necessary to adjust attack parameters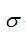 and importance thresholds
and importance thresholds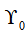 , to adapt to new target system performance requirements and defense strategies.
, to adapt to new target system performance requirements and defense strategies.
B. Reusable Value Components:
Construction of prediction error-driven importance indicators: Can be transferred to other systems that require dynamic identification of key data.
Random triggering attack strategy: Can be directly used for attack scheduling and concealment design in different systems.
Closed-form attack parameter optimization under energy constraints: Can be widely applied to scenarios involving system disturbances under energy constraints.
2. Defect Thinking
1. The experiments mainly adopt ideal linear systems and uniform noise models, and the baseline comparison is limited to Bernoulli distribution DoS attacks.
2. The closed-form derivation of the attack intensity coefficient uses expectations instead of specific instantaneous values, which may introduce bias in complex networks, lacking strict proof of universality under complex dynamic environments.
(PhD Year 2: Liu Haotong)

Changchun University of Technology
Laboratory of Safety and Reliability of Complex Systems
END
 z
z




