First, you need to have a bin file (The method of obtaining the bin file will not be introduced here; we can discuss it in a dedicated post in the future). The bin file used in this experiment  stm32_xwrtos.bin.zip (6 KB)
stm32_xwrtos.bin.zip (6 KB)
Download the programming file:
Link: https://pan.baidu.com/s/1YiMkyqbdPxGOI_vwGtOlJw Extraction code: yi56
Tools preparation:
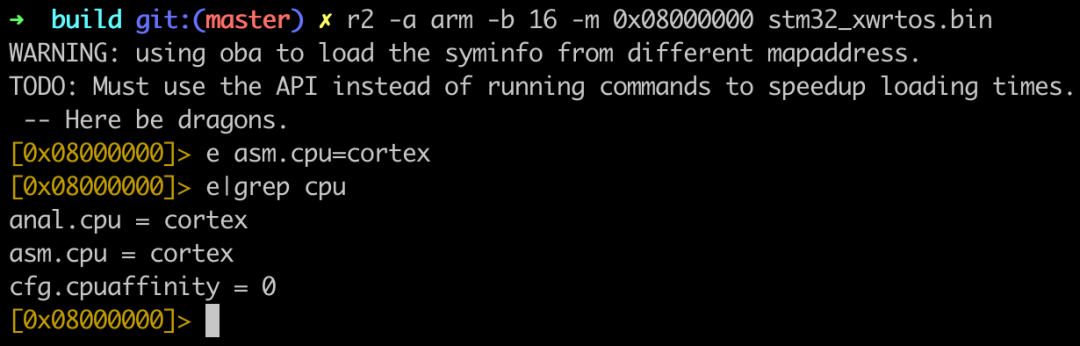
Install the open-source cross-platform reverse engineering tool r2 https://github.com/radareorg/radare2, r2 can run on all mainstream operating systems such as Windows, Linux, and Mac (The capabilities of r2 will not be discussed here; we can have a dedicated post for that in the future).Experiment steps:1) Input r2 -a arm -b 16 -m 0x08000000 stm32_xwrtos.bin to enter the r2 console, then input e asm.cpu=cortex. This step tells r2 to load the stm32_xwrtos.bin file with 0x08000000 as the base address and sets the instruction set to the cortex series thumb.
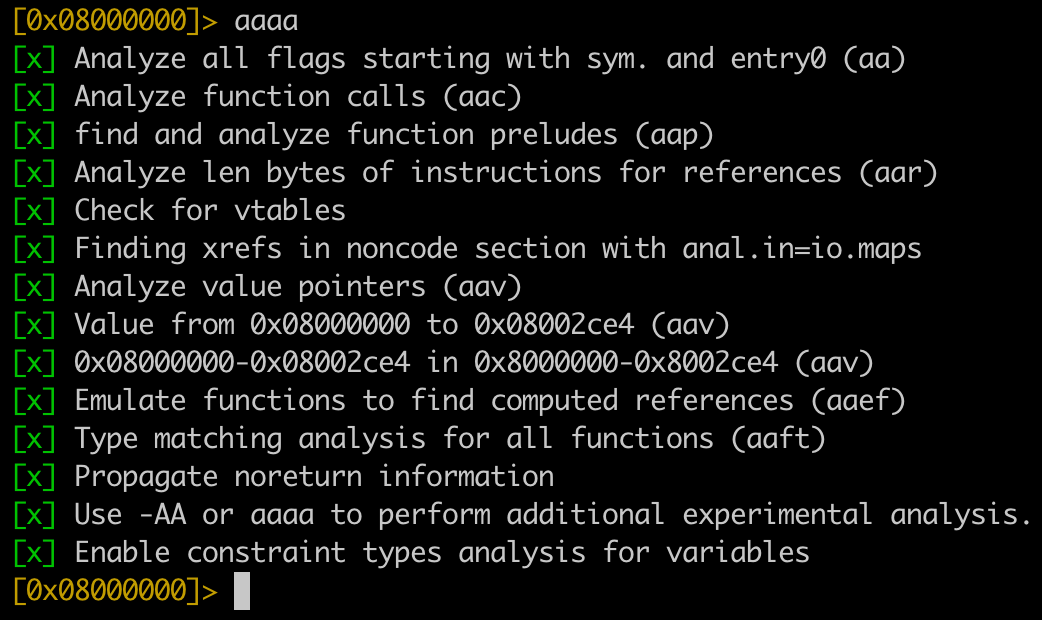
2) Input aaaa to run the automated analysis.
3) Input pxw 268 @0x08000000 to print 268 bytes (which corresponds to the interrupt vector table size) starting from 0x08000000 in little-endian four-byte format, while opening the official ST startup file startup_stm32f10x_md.s to find the .isr_vector segment for comparison.
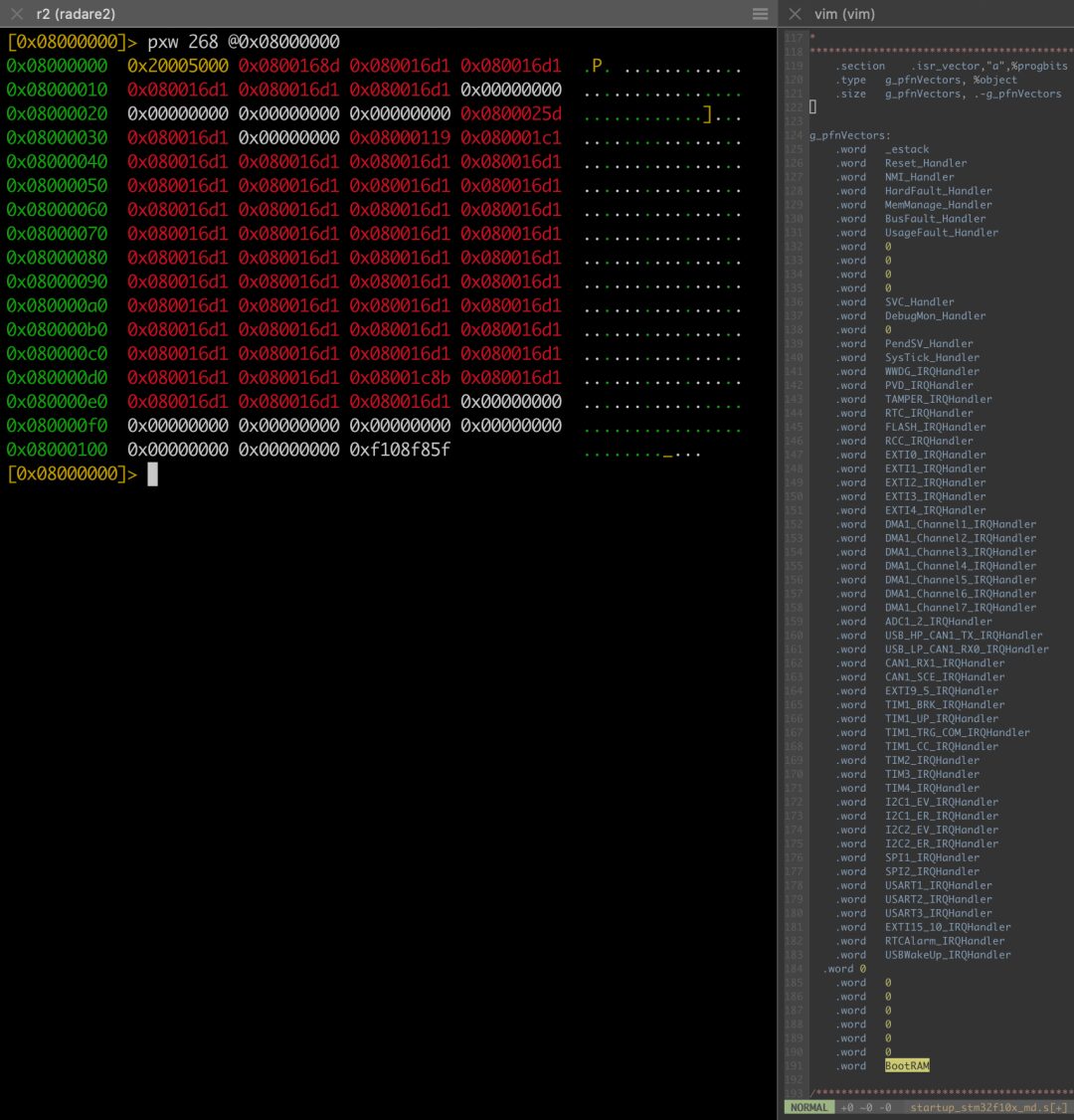
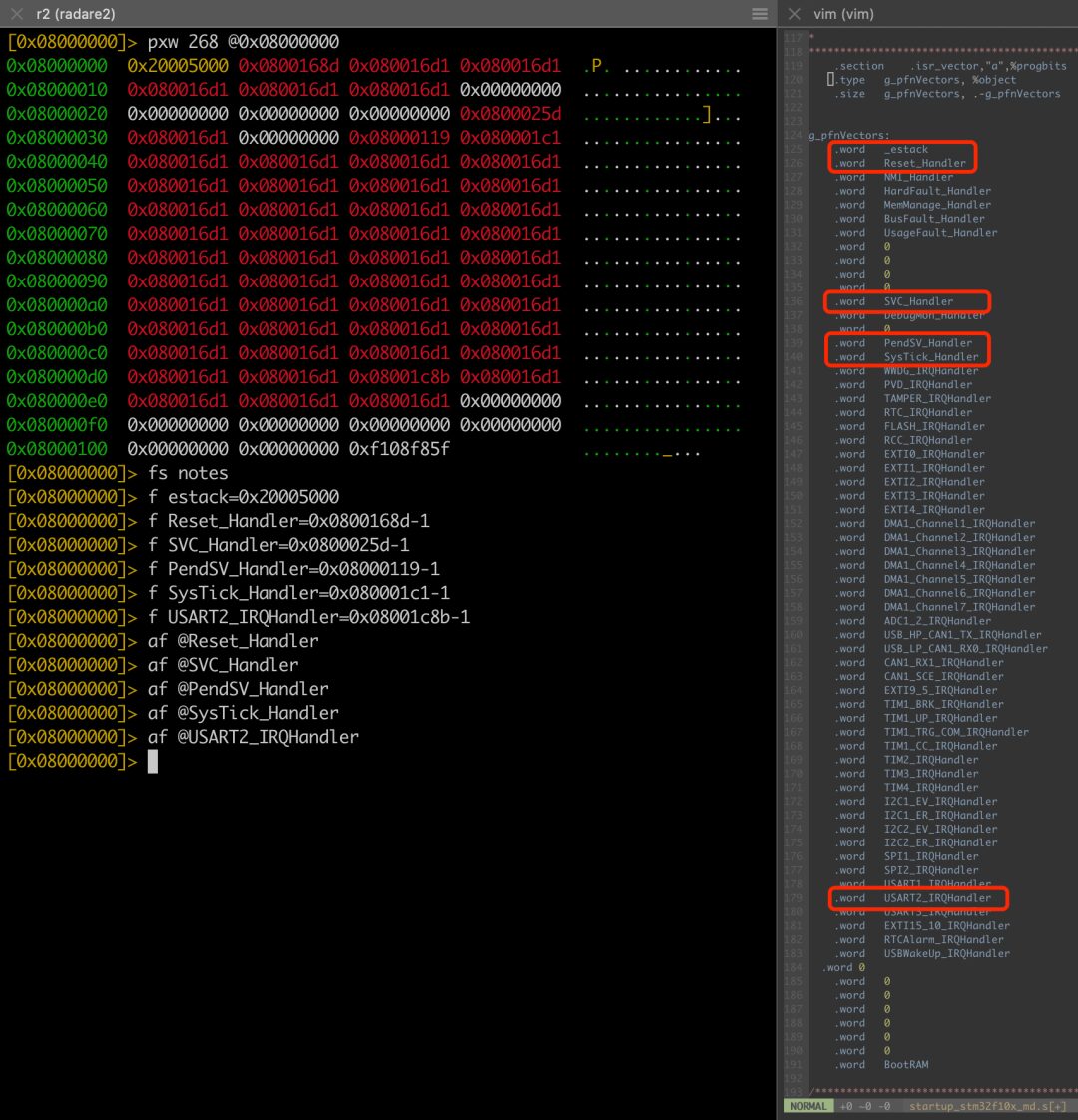
4) Following the previous step, input fs notes to create and switch to a symbol notebook named notes (it can be any other name); according to the format f flag=address, record the address correspondence of the symbols of interest in the symbol notebook. Note that if the address is a function address, you need to subtract 1 (due to the requirements of thumb instructions, the specific reason will not be discussed here); finally, input the command af @flag to force function analysis.
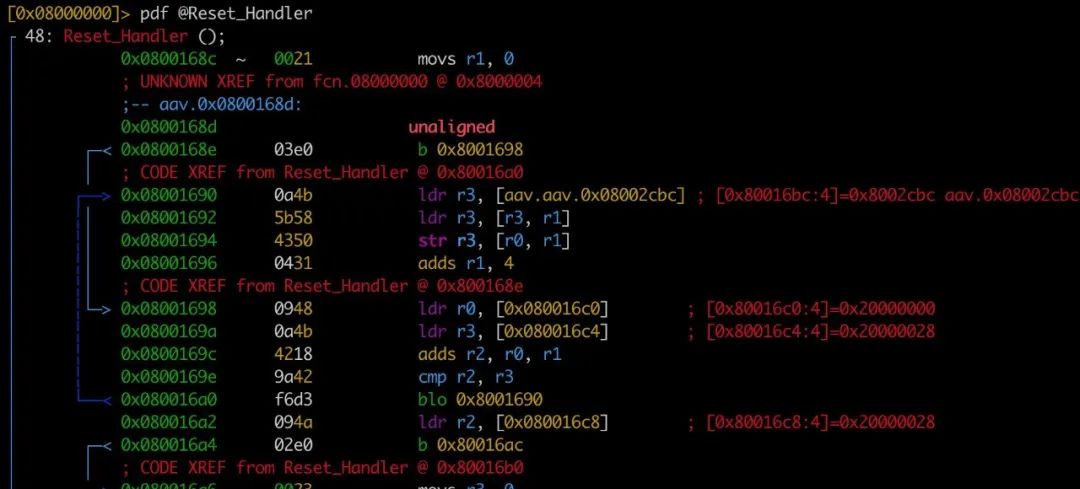
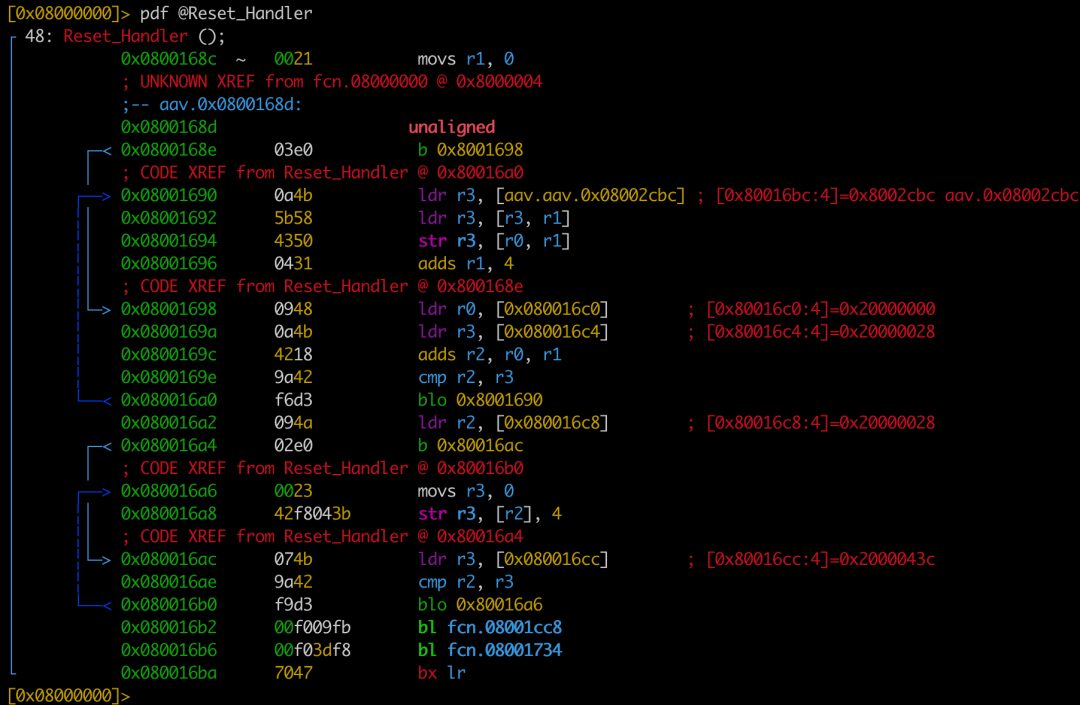
5) Input pdf @Reset_Handler to disassemble the Reset_Handler function
Input VV to switch to flowchart view
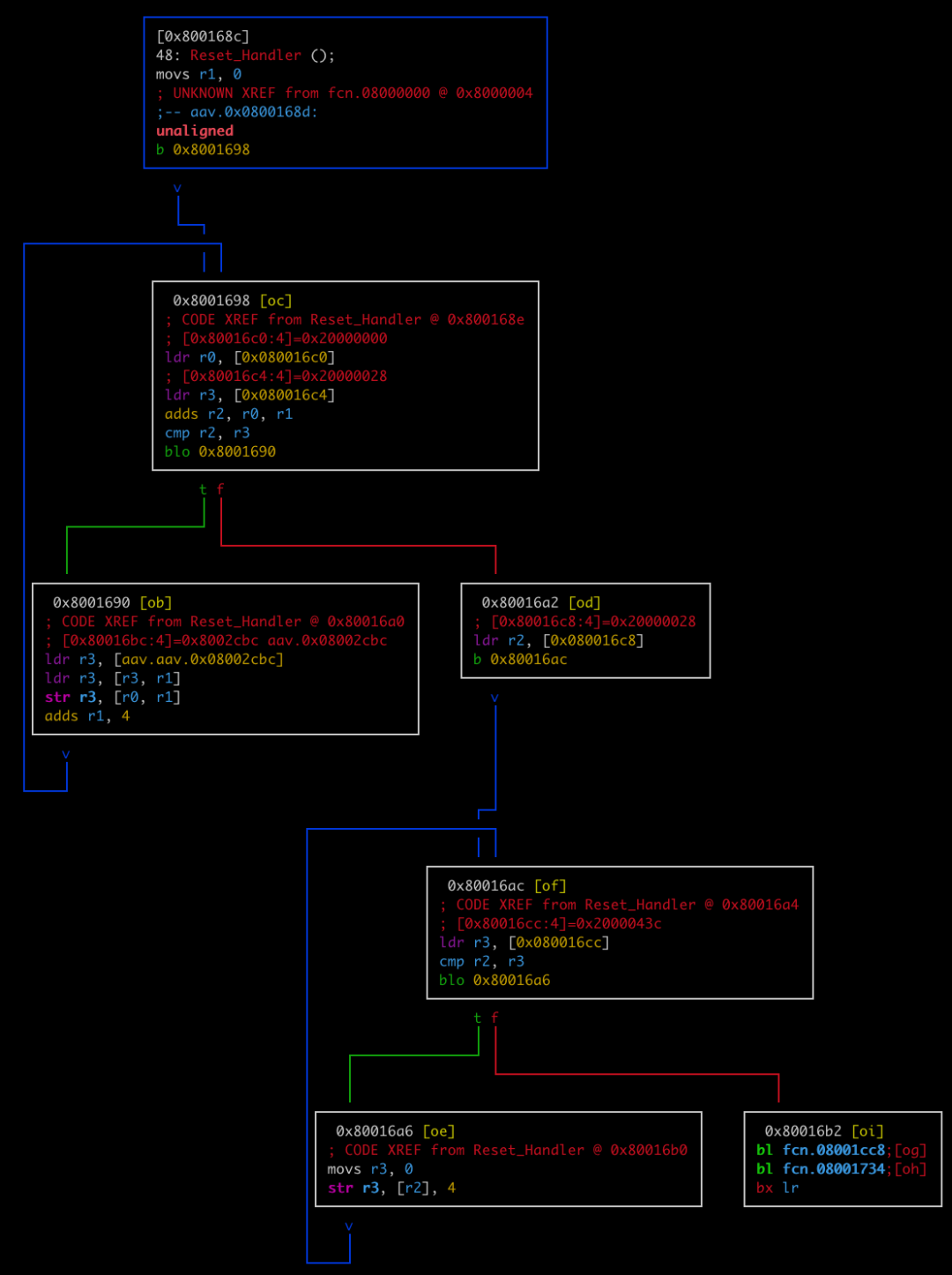
By reading the assembly code, the following information can be obtained: 1. The address range of the data segment is 0x20000000-0x20000028, and the address range of the bss segment is 0x20000028-0x2000043C
2. Reset_Handler initializes the data segment starting from 0x08002cbc with 0x28 bytes and fills the bss segment with zeros
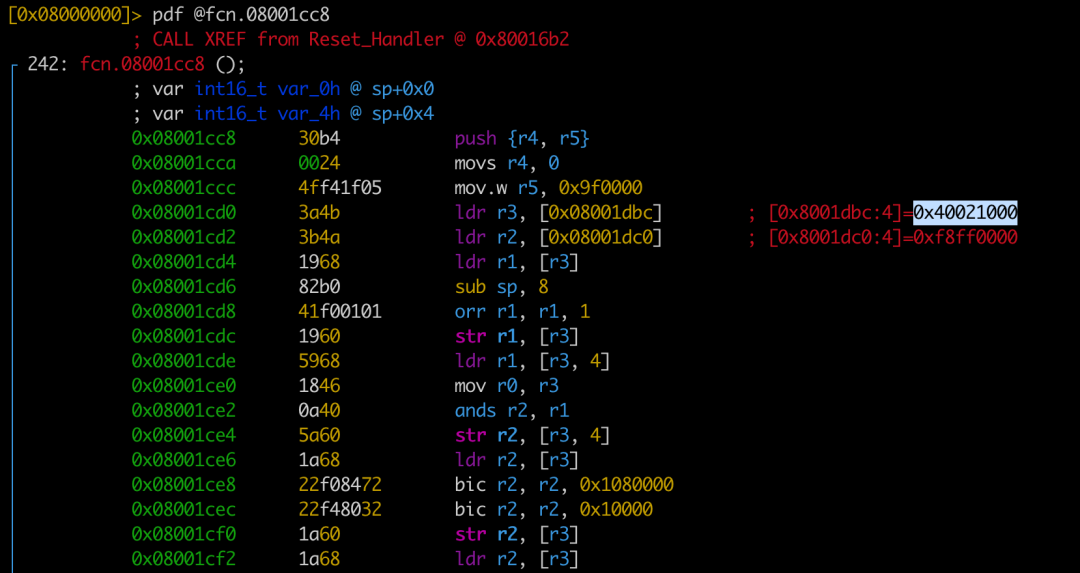
Found reference to the peripheral register address 0x40021000
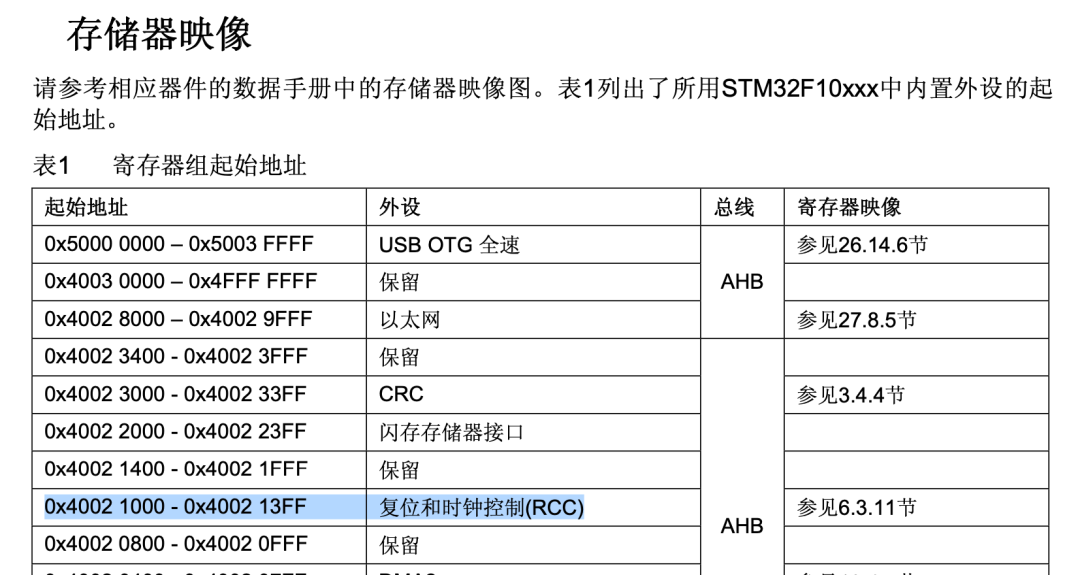
By consulting the data manual, it can be determined that the function fcn.08001cc8 should be the system initialization function SystemInit(), which initializes the clock 7) Based on experience, it can be judged that the function fcn.0800173 is the main function
This article, as the first in the series, mainly serves to familiarize readers with the basic use of r2 and provide a perceptual understanding of reverse engineering. The next article plans to introduce the discovery and exploitation of stack overflow vulnerabilities on stm32 based on reverse engineering.
Thanks again to ilovepp for sharing this wonderful article!
 Heavyweight Open Source: Offline Downloader with LCD Screen!
Heavyweight Open Source: Offline Downloader with LCD Screen!
 [Open Source Solution] 2.4G Remote Control, Complete Detailed Design Materials
[Open Source Solution] 2.4G Remote Control, Complete Detailed Design Materials
 [Fully Open Source Amplifier] Classic Chip from NS Corporation, LM3886!
[Fully Open Source Amplifier] Classic Chip from NS Corporation, LM3886!
 Sharing a Low-Cost Isolation AC Voltage Detection + Power Failure Detection Circuit from Supor
Sharing a Low-Cost Isolation AC Voltage Detection + Power Failure Detection Circuit from Supor
 Software Tool TortoiseGit, Xiaoyu Sister Teaches You to Manage Microcontroller Program Versions Graphically!
Software Tool TortoiseGit, Xiaoyu Sister Teaches You to Manage Microcontroller Program Versions Graphically!