First, let’s address the leftover issues from Jenkins. Below is the original pipeline code to add a non-image to the cluster as a deployment.
pipeline { agent { kubernetes { inheritFrom 'default' namespace 'xiejiajia' serviceAccount 'jenkins-sa' // Use the newly created ServiceAccount } } environment { ACR_SERVER = 'registry.cn-hangzhou.aliyuncs.com' ACR_NAMESPACE = 'nginx-vmware' ACR_REPOSITORY = 'jenkins-test' ACR_USERNAME = 'xxxxx' ACR_PASSWORD = '99xxxx' } stages { stage('Test Kubernetes Connection') { steps { sh ''' # Test kubectl connection kubectl get nodes kubectl get ns ''' } } stage('Build and Push Docker Image') { steps { withCredentials([usernamePassword(credentialsId: 'aliyun-codeup', usernameVariable: 'GIT_USERNAME', passwordVariable: 'GIT_PASSWORD')]) { sh ''' echo "${ACR_PASSWORD}" | docker login ${ACR_SERVER} -u ${ACR_USERNAME} --password-stdin docker build -t ${ACR_SERVER}/${ACR_NAMESPACE}/${ACR_REPOSITORY}:${BUILD_NUMBER} . docker tag ${ACR_SERVER}/${ACR_NAMESPACE}/${ACR_REPOSITORY}:${BUILD_NUMBER} ${ACR_SERVER}/${ACR_NAMESPACE}/${ACR_REPOSITORY}:latest docker push ${ACR_SERVER}/${ACR_NAMESPACE}/${ACR_REPOSITORY}:${BUILD_NUMBER} docker push ${ACR_SERVER}/${ACR_NAMESPACE}/${ACR_REPOSITORY}:latest docker rmi ${ACR_SERVER}/${ACR_NAMESPACE}/${ACR_REPOSITORY}:${BUILD_NUMBER} docker rmi ${ACR_SERVER}/${ACR_NAMESPACE}/${ACR_REPOSITORY}:latest ''' } } } stage('Deploy to Kubernetes') { steps { sh ''' # Replace the image tag in the deployment file sed -i "s|:latest|:${BUILD_NUMBER}|g" deployment.yaml # Apply deployment kubectl apply -f deployment.yaml # Wait for the deployment to complete kubectl rollout status deployment/lianghua-deployment -n xiejiajia ''' } } } post { always { deleteDir() } success { echo 'Build and deployment succeeded!' } failure { echo 'Build or deployment failed!' } }}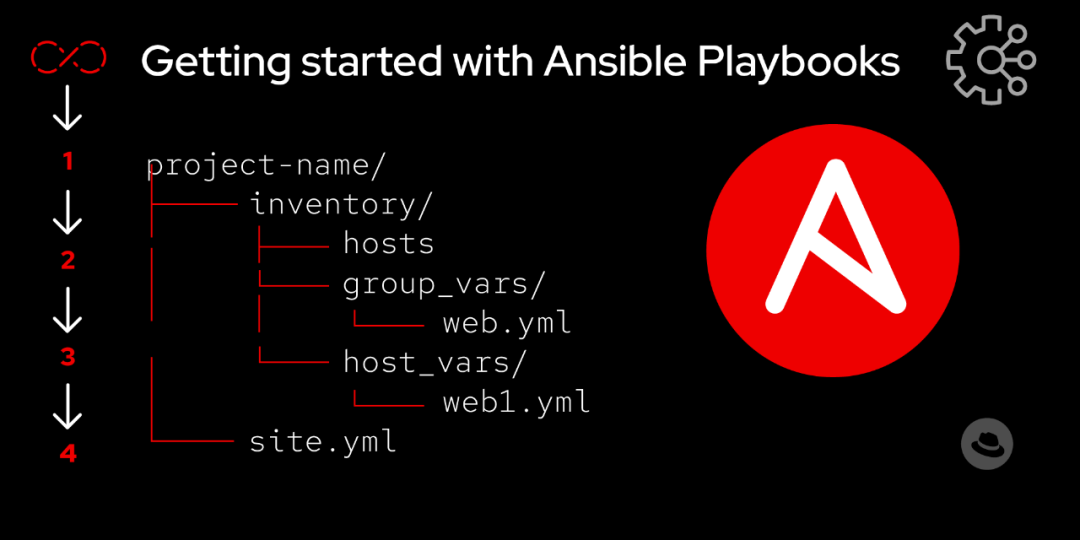
## 1. Working Logic
– Ansible uses a Push-based model
– Communicates over SSH protocol without needing an agent on the managed nodes
– Configuration files are written in YAML
– Has idempotency (same operation yields the same result when executed repeatedly)
## 2. Core Components
1. Inventory
– Defines hosts and host groups
– Supports static configuration files and dynamic generation
– Can set host variables and group variables
2. Playbook
– The core of configuration management
– Describes automation tasks in YAML format
– Reusable and composable
3. Module
– Specific task execution unit
– Built-in with many commonly used modules
– Supports custom module development
4. Role
– Organizational unit of playbook
– Facilitates code reuse
– Standardized directory structure
## 3. Comparison of Three Execution Methods
### Ad-hoc Commands
“`bash
# Example 1: Check host connectivity
ansible all -m ping
# Example 2: Execute shell command
ansible webservers -m shell -a “uptime”
# Example 3: Copy file
ansible app_servers -m copy -a “src=/etc/hosts dest=/etc/hosts”
“`
### Command Module
“`bash
# Example 1: Restart service
ansible web -m command -a “service nginx restart”
# Example 2: View directory contents
ansible db -m command -a “ls -l /var/log”
“`
### Script Module
“`bash
# Example 1: Execute local script
ansible all -m script -a “./scripts/setup.sh”
# Example 2: Execute script with parameters
ansible web -m script -a “./install.sh -v –prefix=/opt/app”
“`
## 4. Practical Examples of Playbook
### Common Playbook Commands
“`bash
# Execute playbook
ansible-playbook playbook.yml
# Check syntax
ansible-playbook playbook.yml –syntax-check
# Test run (without actual execution)
ansible-playbook playbook.yml –check
# Specify inventory file
ansible-playbook -i inventory.ini playbook.yml
# Limit execution to host group
ansible-playbook playbook.yml –limit webservers
# With extra variables
ansible-playbook playbook.yml –extra-vars “version=1.0.0”
# Execute with vault encrypted file
ansible-playbook playbook.yml –ask-vault-pass
# Execute in parallel (set concurrency)
ansible-playbook playbook.yml -f 10
# Display verbose output
ansible-playbook playbook.yml -v
“`
### Common Structure of Playbook
“`yaml
—
– name: Example Playbook
hosts: webservers
become: yes
vars:
http_port: 80
max_clients: 200
tasks:
– name: Ensure apache is installed
apt:
name: apache2
state: present
– name: Ensure apache is running
service:
name: apache2
state: started
enabled: yes
handlers:
– name: Restart apache
service:
name: apache2
state: restarted
“`
### Case 1: Batch System Update
“`yaml
—
– hosts: all
become: yes
tasks:
– name: Update apt cache
apt:
update_cache: yes
– name: Upgrade all packages
apt:
upgrade: dist
“`
### Case 2: Deploy Web Application
“`yaml
—
– hosts: web_servers
become: yes
tasks:
– name: Install nginx
apt:
name: nginx
state: present
– name: Copy configuration file
copy:
src: files/nginx.conf
dest: /etc/nginx/nginx.conf
– name: Start service
service:
name: nginx
state: started
enabled: yes
“`
### Case 3: Database Backup
“`yaml
—
– hosts: db_servers
tasks:
– name: Create backup directory
file:
path: /backup/mysql
state: directory
– name: Execute MySQL backup
shell: |
mysqldump -u root -p{{ mysql_root_password }} \
–all-databases > /backup/mysql/full_backup_$(date +%Y%m%d).sql
“`
## Best Practice Recommendations
1. Naming Conventions
– Use meaningful variable names and task names
– Keep playbook structure clear
2. Variable Management
– Use group_vars and host_vars appropriately
– Encrypt sensitive information using vault
3. Module Selection
– Prefer using dedicated modules over shell/command
– Pay attention to the idempotency of modules
4. Error Handling
– Use handlers appropriately
– Set appropriate error handling strategies
5. Version Control
– Use Git to manage playbooks
– Tag versions properly