1. Problem Description
If after booting the embedded Linux root file system made with Buildroot, you find that you are not logged in as the root user, this may be due to improper file system permission settings or user configuration issues.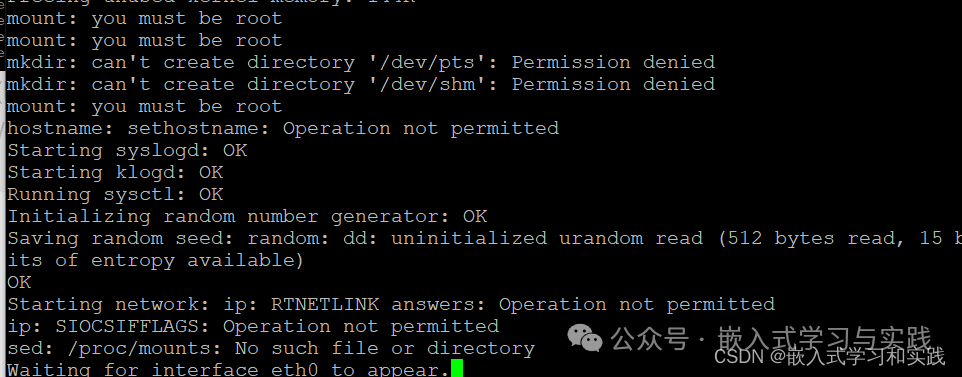
2. Solutions
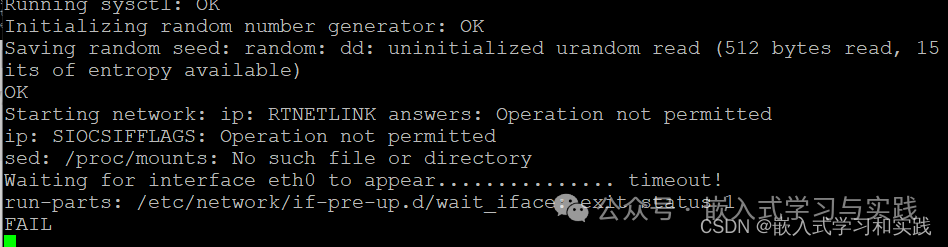
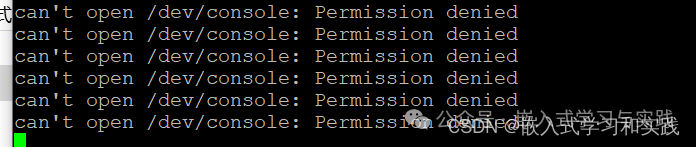
Here are some possible solutions:1. Check BusyBox Permissions As mentioned in the logs you referred to, there may be an issue with the permissions of BusyBox. BusyBox is a single executable that integrates many commonly used Linux commands and tools, and it is very common in embedded systems. Use the ls -l command to check the permissions of BusyBox. If you see permissions like -rwsr-xr-x, where the s indicates that the SUID (Set User ID) bit is set, this may allow non-root users to execute the command with root privileges. If the permission settings for BusyBox are incorrect, you can use the chmod command to modify it. For example, to remove the SUID bit, you can execute:
chmod a-s busyboxOr use the command:
sudo chown root * -RThis command means to change the owner of all files in the current directory to root, where -R means to recursively traverse and change those in subdirectories as well.2. Check /etc/passwd and /etc/shadow FilesThese files define the users on the system and their permissions. Ensure that the entry for the root user is correct and has not been improperly modified. If these files have been improperly modified, you may need to manually edit them to restore the correct settings for the root user.3. Check Initramfs or Initramfs ConfigurationIf Buildroot uses initramfs as the initial file system, then there may be an issue with the initramfs configuration. Check the initramfs configuration scripts to ensure that the root user settings are correct.4. Check Buildroot ConfigurationDouble-check the Buildroot configuration files to ensure that there are no errors or missing configuration items that may affect the user settings of the root file system.5. Rebuild the Root File SystemIf the above methods do not resolve the issue, you may need to rebuild the root file system. Ensure that you follow the correct steps during the build process and that all dependencies and configurations are correct.6. Review Boot Logs and System LogsCarefully review the logs during the boot process and system logs for clues that may cause non-root user login. This may provide more detailed information about the problem.7. Check SELinux or AppArmor PoliciesIf your system has security modules like SELinux or AppArmor enabled, ensure that their policies are not preventing the root user from logging in or performing necessary actions.NoteBe aware that directly modifying system files or permissions may lead to system instability or security risks. Before making any changes, ensure you understand the implications and potential impacts of these changes, and always validate in a test environment.
3. Practical Testing
Check the permissions of BusyBox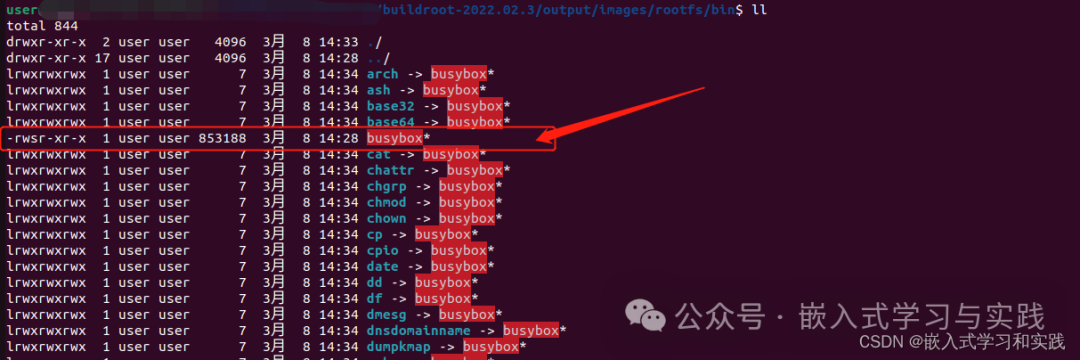 Use the command to modify, command:
Use the command to modify, command:
chmod a-s busyboxCheck the modified permissions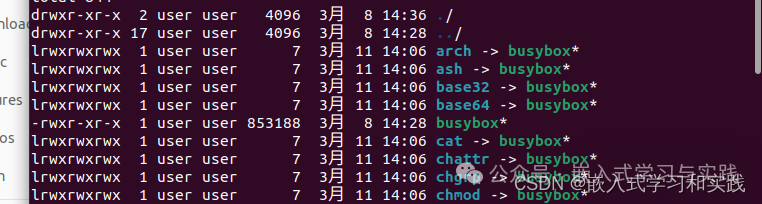 Or use the command:
Or use the command:
sudo chown root * -RThis command means to change the owner of all files in the current directory to root, where -R means to recursively traverse and change those in subdirectories as well. Check the modified permissions as follows: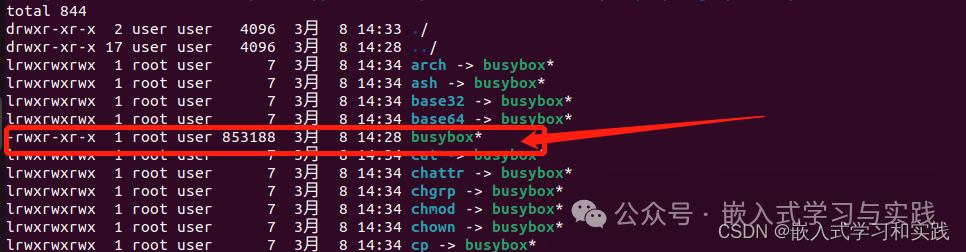 Download test
Download test System boots normally.
System boots normally.