Click the blue text
Follow us
Statement
Author: Keac Word Count: 4000 words
Reading time: about 11 minutes
Attachment/Link: Click to view the original text download
This article belongs to the 【Wolf Group Security Community】 original reward plan, and reprinting is prohibited without permission
The user is responsible for any direct or indirect consequences and losses caused by the dissemination and use of the information provided in this article. The Wolf Group Security Team and the article author do not bear any responsibility for this.
The Wolf Group Security Team has the right to modify and explain this article. If you want to reprint or disseminate this article, you must ensure the integrity of this article, including copyright statements and all content. Without the permission of the Wolf Group Security Team, no arbitrary modification or addition to this article’s content is allowed, nor can it be used for commercial purposes in any way.
Introduction
Those who follow the public account should have seen a previous article “On-Site Penetration P4wnP1_Aloa (Part 1)”. In this article, I used Raspberry Pi Zero (W), but a year has passed, and with the rising prices of chips, Raspberry Pi has also increased in price and is even hard to buy. 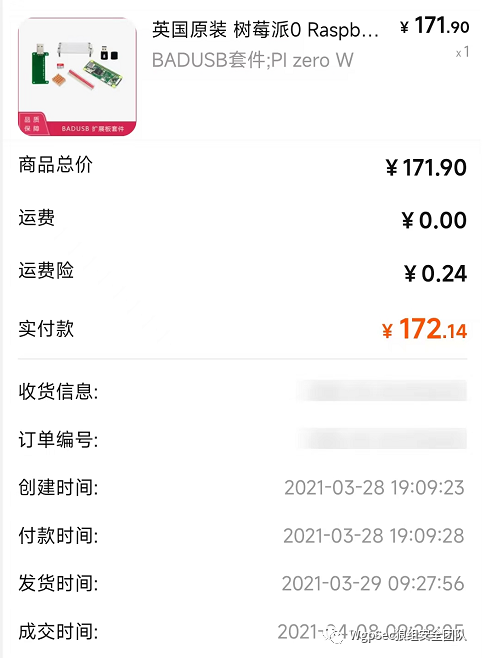

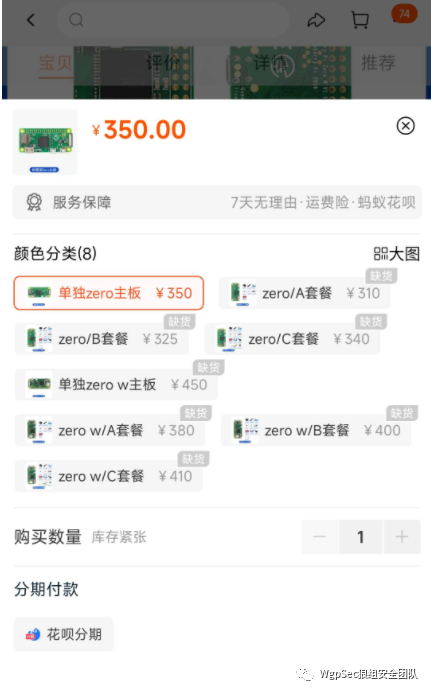 But now looking at the price, it has increased several times, nearly 4 times, it is really a “financial product”. With such a high price, it would be a pity to lose it carelessly. However, while exploring recently, I found something interesting,
But now looking at the price, it has increased several times, nearly 4 times, it is really a “financial product”. With such a high price, it would be a pity to lose it carelessly. However, while exploring recently, I found something interesting, 4G portable WiFi, which is usually used for internet access, especially during various drills, it’s good for anti-tracing and very useful (  I have a Huawei wireless card I bought, which costs several hundred, but did you notice when buying those particularly cheap portable WiFi? Our story starts here.
I have a Huawei wireless card I bought, which costs several hundred, but did you notice when buying those particularly cheap portable WiFi? Our story starts here.
What is this?
Everyone can basically find those portable WiFi costing dozens of dollars on Taobao.
You may be curious why it is so cheap? First of all, cheap portable Wi-Fi basically uses engineering mold solutions, such as Qualcomm 410, Qualcomm 210, ZTE Micro, etc. The appearance may differ greatly, but internally they might be the same solution (the same solution may have different boards), and of course, there may be cases where the same product is sent to buyers with different models; secondly, low-priced portable Wi-Fi products generally have data package options, which include an esim card, you can use it after scanning the code for real-name authentication, of course, most of them actually have a physical card slot (some products may not), you can use your own mobile card package, but you need to manually switch cards.
In most cases, cheap portable Wi-Fi is easier to crack than branded products. This is because, constrained by cost, counterfeit manufacturers generally use the same solutions, and some even use the same molds, which means they do not have the energy and financial resources to shield the mainboard 9008 port and adb, which is inconvenient for their own debugging. On the other hand, big brands like Huawei and ZTE are harder to crack, some use their own chip solutions, or need hardware modifications, which we will not consider here. In principle, you can buy any portable Wi-Fi, and the possibility of cracking is very high. However, some extra operations are required, and the tutorials are not complete, making it relatively difficult.
The default basic configuration is:
-
msm8916 main control Cortex-A53 * 4 on 0.9GHZ -
512MB memory + 4GB storage second-hand emcp -
WCN3620 & WCN3680b -
pm8916 PMIC -
android 4.4 system
Let’s compare it with the Raspberry Pi configuration 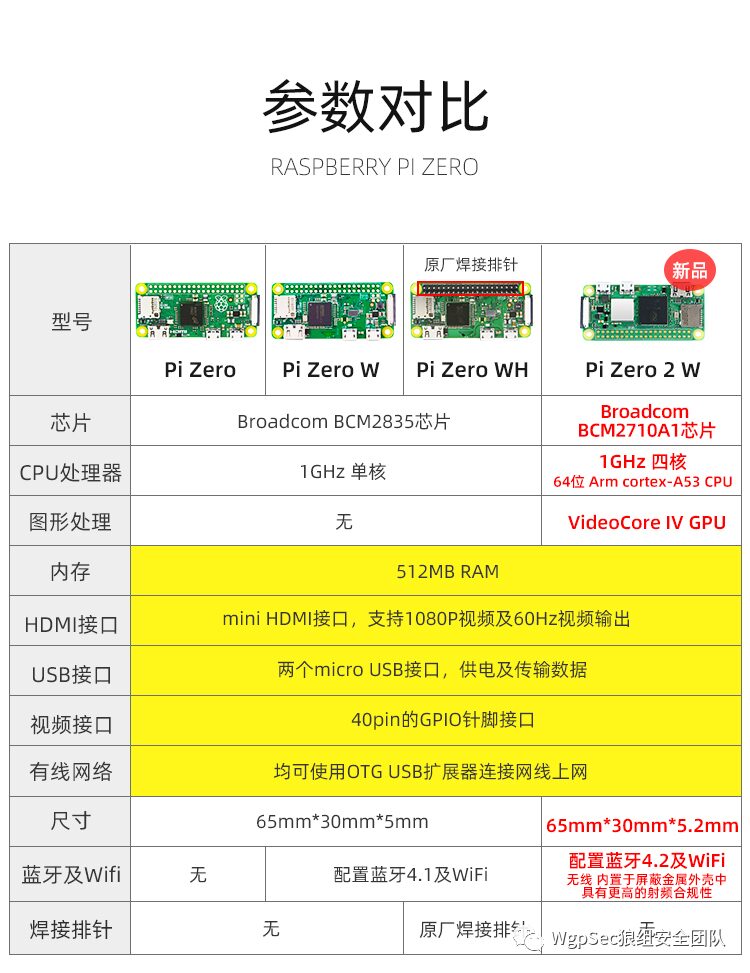 You can see that the configuration is actually quite similar to Raspberry Pi Zero, missing quite a lot of things, but there are still many things it can do. If you want to mess around, you can follow the public account and reply
You can see that the configuration is actually quite similar to Raspberry Pi Zero, missing quite a lot of things, but there are still many things it can do. If you want to mess around, you can follow the public account and reply portable WiFi to get the link, summarizing some of the better network cards I encountered.
Results Show
First, let’s take a look at what I have done with these network cards. 
Friends who are interested can communicate together
 Currently, I have only three on hand
Currently, I have only three on hand 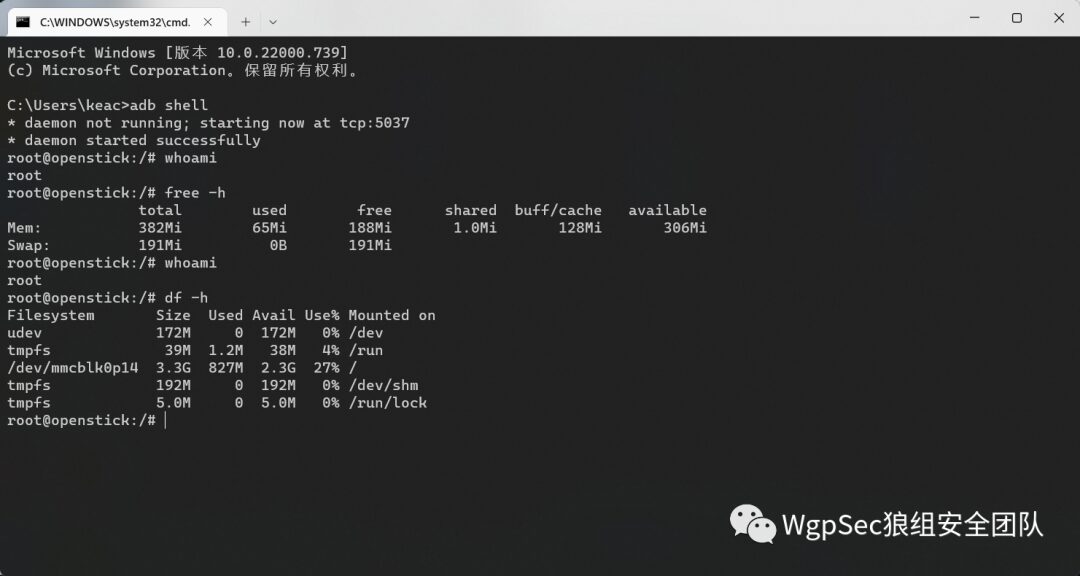 running Nmap and so on, suitable for finding a place to plug in power for remote penetration
running Nmap and so on, suitable for finding a place to plug in power for remote penetration  It can also run Docker
It can also run Docker 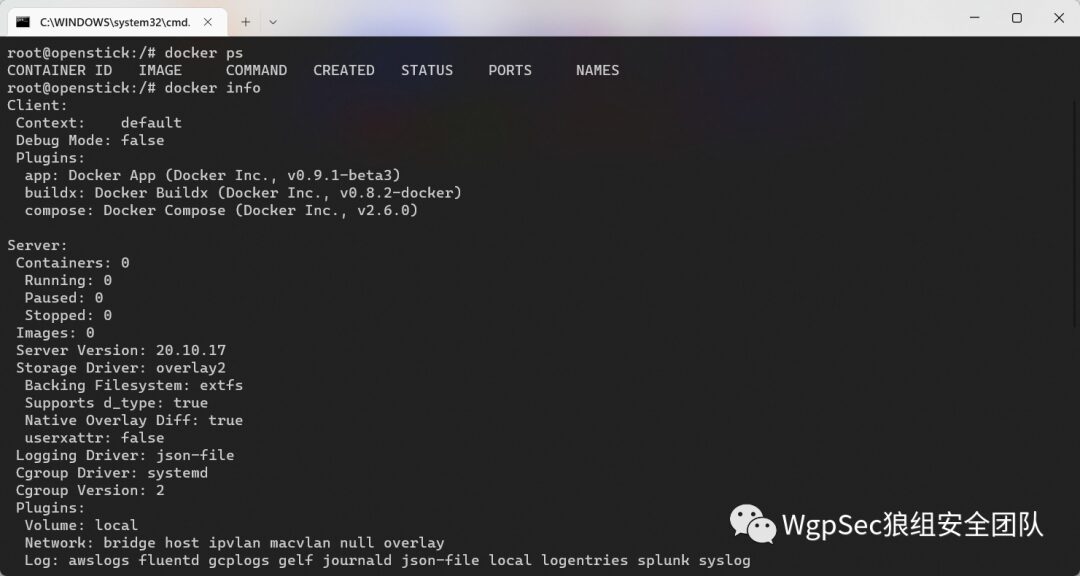 WIFI phishing
WIFI phishing 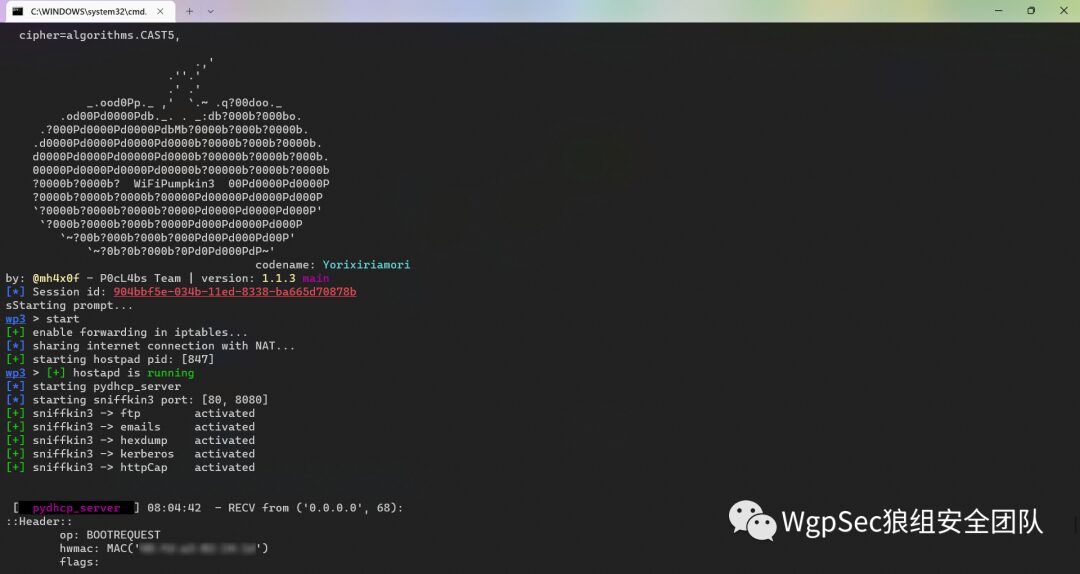 More functions are still being explored, this machine is quite powerful, and its shape is compact and cost-effective.
More functions are still being explored, this machine is quite powerful, and its shape is compact and cost-effective.
Purchase
When purchasing, be sure to pay attention to the front text “TD-LTE Wireless Data Terminal”. (What it is called is not important, the names of such counterfeit machines are not fixed, but it must look the same as in the picture), you can also follow the public account and reply portable WiFi to view the recommended machines.
Messing Around
Preparation Work
-
Portable Wi-Fi based on Qualcomm 410 (msm8916) solution: The silkscreen on the board is UFI001B, UFI001C, UFI003, UFI-W-001 is best, or SP970 -
A Windows computer (it is recommended to install Huorong, as some files may be deleted by Win’s default protection as viruses) -
Small card to large card SIM card adapter -
Screwdriver (to unscrew the portable Wi-Fi’s small cross screws)
Of course, if you directly use esim data, then you don’t need to disassemble the device, you can use it directly
Check
The first thing to do after receiving it is to plug it in, connect to the Wi-Fi provided by the portable Wi-Fi, enter the background, and check if it can work normally to prevent it from being broken upon arrival. The default device will automatically restart if there is no network for 5 minutes, and when I bought it, I almost thought they were all broken Then plug it into the computer to see if the computer recognizes the hardware, such as adb or Android, which means your machine can be cracked without disassembly, and its adb port is open. 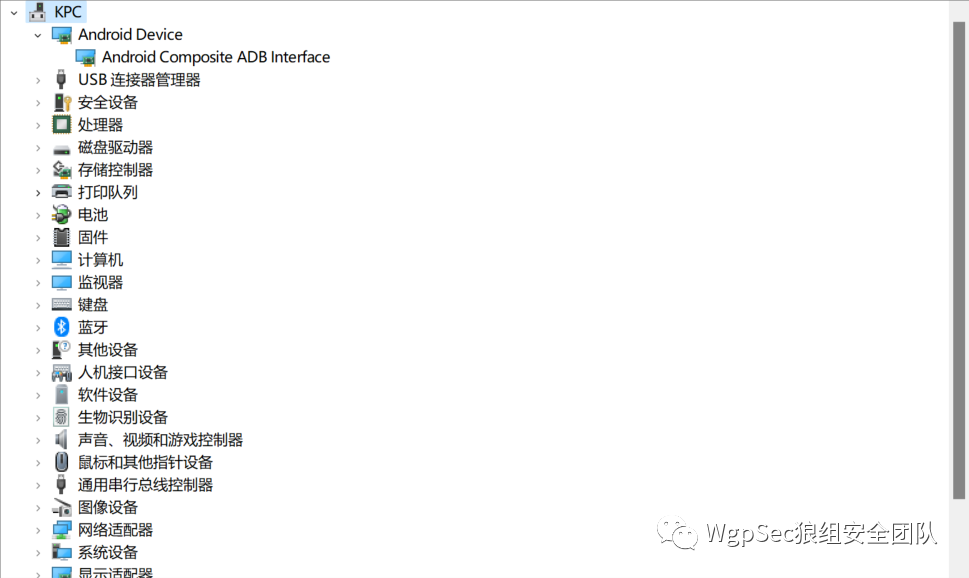 Then use the screwdriver to open it and check the board for card slots and the version silkscreen on it.
Then use the screwdriver to open it and check the board for card slots and the version silkscreen on it.
Drivers
We first need to install the required 9008 driver. Open the folder of the 9008 unsigned driver and install the driver. 
Flashing Tool
Open the Qualcomm Premium Tool V2.4 folder. First, use the key generator to generate a .key file. 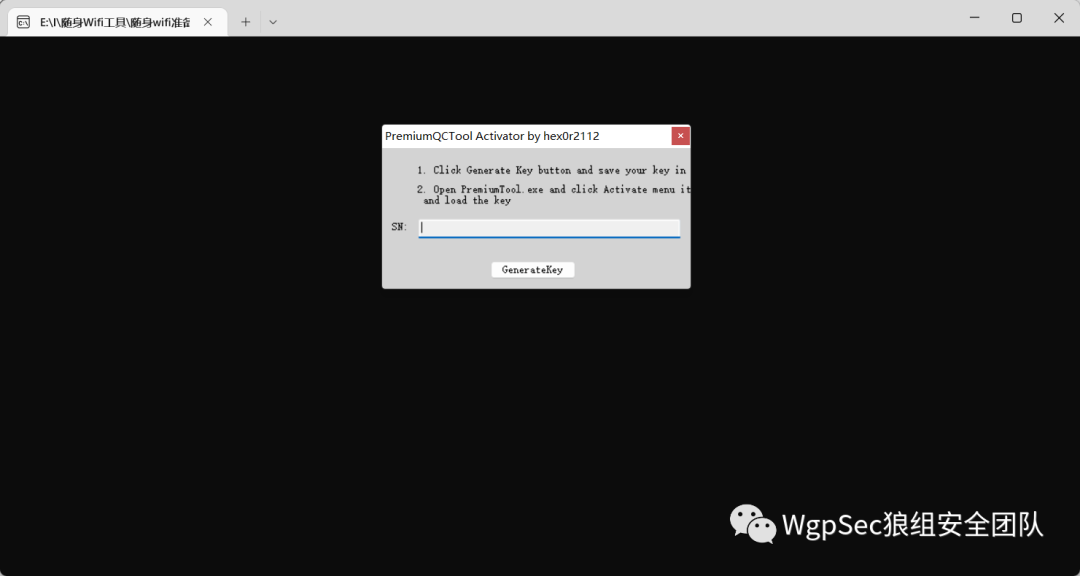 Later it will prompt you to save the .key file somewhere, just choose a place you can find it, then open Premium Tool V2.4. Click Help and then Activate to activate it, selecting the .key file you saved earlier to activate successfully.
Later it will prompt you to save the .key file somewhere, just choose a place you can find it, then open Premium Tool V2.4. Click Help and then Activate to activate it, selecting the .key file you saved earlier to activate successfully.
Flashing
Flashing is risky, proceed with caution, this article is not responsible for any bricked devices Unplug the portable WiFi, use a pen tip or something to press the reset button, and reconnect to the computer. Accompanied by a crisp prompt sound, please right-click to open Computer – Management – Port to see if the 9008 port is recognized. At this time, the portable WiFi indicator light will not be on. 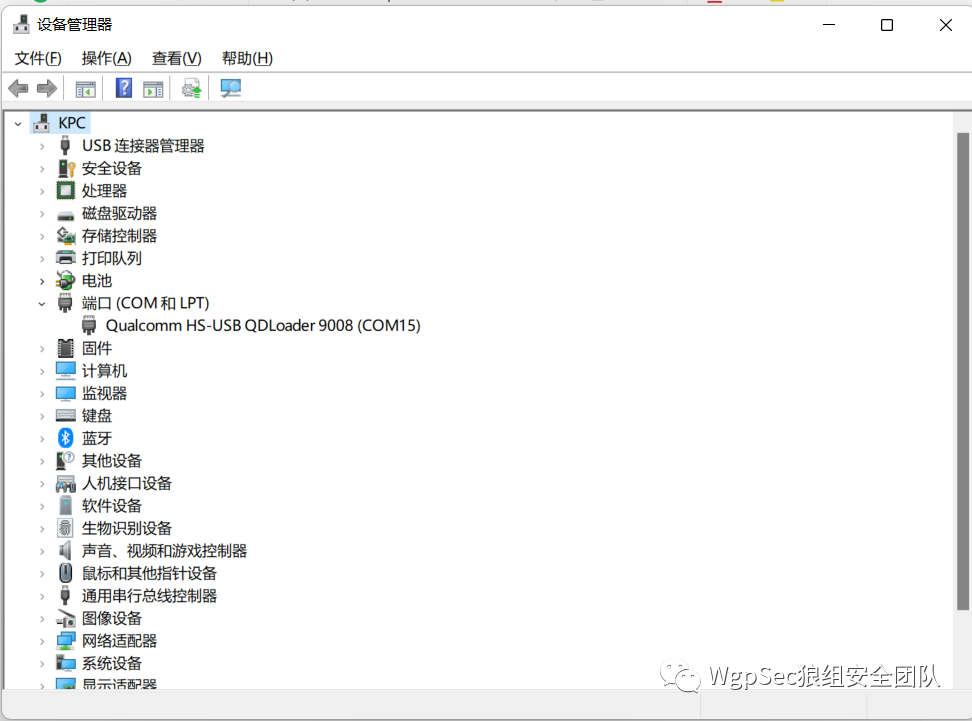 Once you see it, you can open the tool
Once you see it, you can open the tool 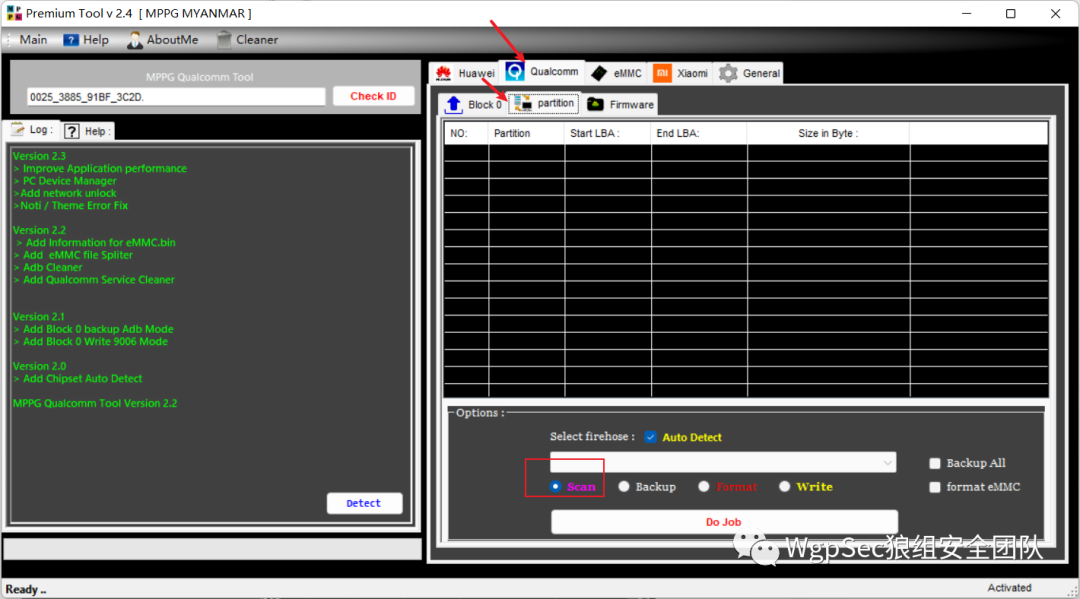 After clicking, you can find that the internal partition is recognized, and my machine has already flashed the system
After clicking, you can find that the internal partition is recognized, and my machine has already flashed the system 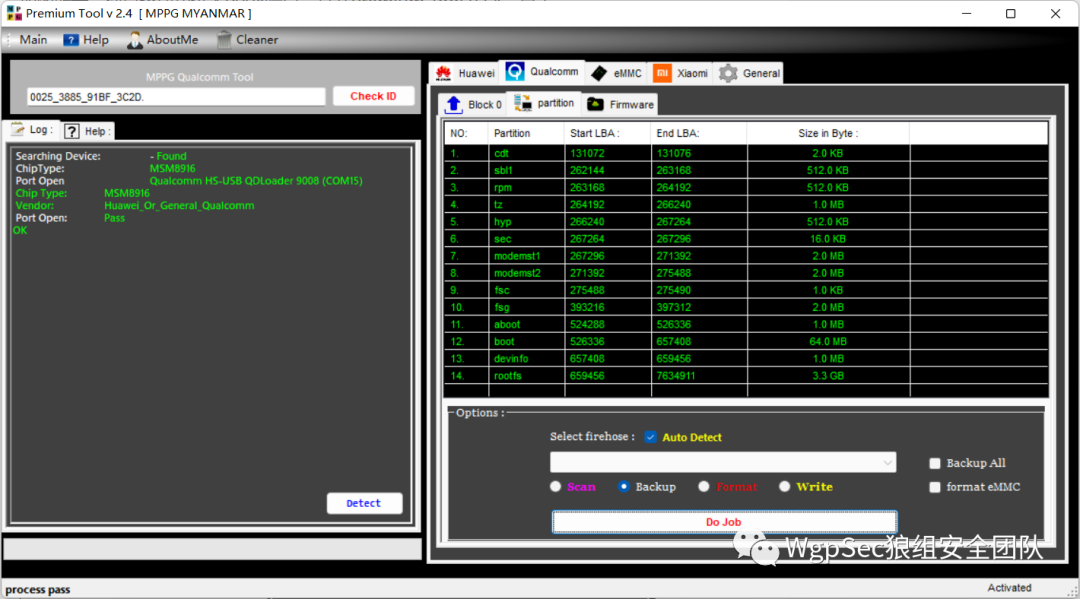 Next, we will flash the image, select 27 userdata, click write below, choose the userdata.img in the folder UFIOO1C_MB_V01_芷荷_救砖_ROM, and click do job to flash it. The flashing process is relatively long, so do not think the software is stuck and forcefully exit. The display shows success or the gray button turns back to color, indicating that the flashing is complete.
Next, we will flash the image, select 27 userdata, click write below, choose the userdata.img in the folder UFIOO1C_MB_V01_芷荷_救砖_ROM, and click do job to flash it. The flashing process is relatively long, so do not think the software is stuck and forcefully exit. The display shows success or the gray button turns back to color, indicating that the flashing is complete.
ARDC
During the flashing process, we can install the screen projection software ARDC, just click to install. After flashing is completed, unplug and reinsert to enter the interface 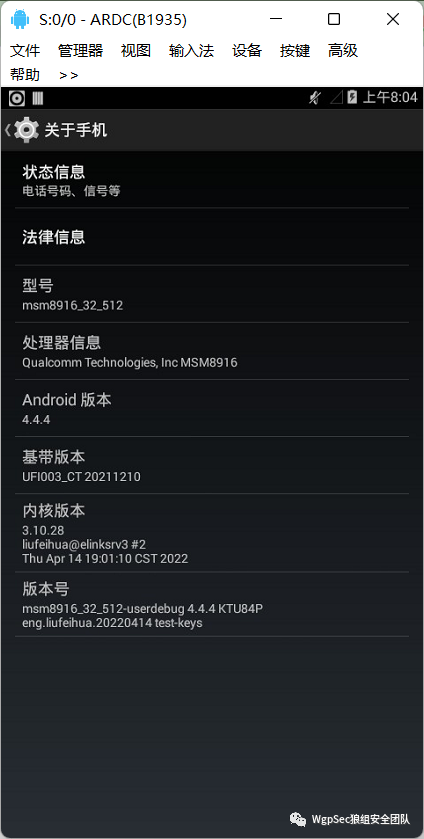
Second Fast Flashing Method
A tool written by a Coolan master, just plug in the portable Wi-Fi and open the program to flash.
Flashing Debian System
After this wave of messing around, we can successfully install APKs and other applications inside, and then we can start messing around with things.
If you need to use the SIM card data, please confirm whether you can use the SIM card for internet access before flashing Debian
Next, we will flash OpenStick to install various software. Other systems are still being researched on how to adapt, interested masters can study how to get Kali in, and install a set of P4wnP1_Aloa.
https://www.kancloud.cn/handsomehacker/openstick/2636505
★
Regarding the reverse engineering of the 4G network card based on the msm8916 chip and Mainline Linux porting. Aims to achieve a low-cost ARM64 single-board computer with 4G functionality (performance is actually similar to Raspberry Pi Zero 2 and Raspberry Pi 3B). Provides a fully usable Debian distribution image and flashing method. It will also provide advanced gameplay such as emcp expansion. Supports 4G wireless network cards with circuit board silkscreen starting with UFI001B, UFI001C, SP970, UZ801.
”
| Function | Support Status |
|---|---|
| arm64 | Supported |
| KVM virtualization | Supported |
| PSCI | Supported (v1.0) |
| Adaptive emcp space | Supported |
| WIFI (WCN3620) | Supported |
| WIFI (WCN3680b) | Supported |
| Bluetooth | Supported |
| 4G data | Supported |
| SMS | Supported |
| USB HOST | Supported |
| USB DEVICE | Supported |
| Venus video decoder | Supported |
| Venus video encoder | Not supported |
| GPS | Not verified |
| Call | Not verified |
For more introduction, you can check the official documentation. Here we will directly introduce how to flash. Taking Windows as an example, we first install the drivers mentioned above adb devices first check if the device is connected properly adb reboot fastboot then restart the device into fastboot mode.
-
Unzip the base.zip package. -
Put your device into fastboot mode. -
Execute the flash.bat inside. -
After completion, unzip .zip package. -
Execute the flash.bat inside.
The flashing process is fully automated, just wait for the progress bar to finish. After flashing is completed, we unplug and reinsert the device, then check adb devices to see if the device is displayed.
RNDIS
After messing around, we may find that the device in the network connection is missing, at this time we need to go to Device Manager to see an unknown device.
-
Click Update Driver – Choose “Browse my computer for driver software”. Then “Let me pick from a list of device drivers on my computer”. -
Select the “Network adapters” section. -
Select “Microsoft”. -
Then find a driver with the name NDISand click it to recognize it.
Then we will see an icon like this 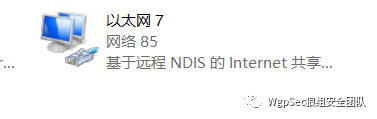
Configuring the Device
If you, like me, bought one without a SIM card slot and are too lazy to return it (actually took a month to mess around), then when installing and configuring, you need to connect to Wi-Fi. There are two ways to connect the device:
-
adb shell -
ssh find the IP of your network card, usually 192.168.68.1 username user password 1
After connecting, we first need to configure export TERM=xterm, otherwise some commands will report TERM environment variable needs set. error.
Next, we use nmtui 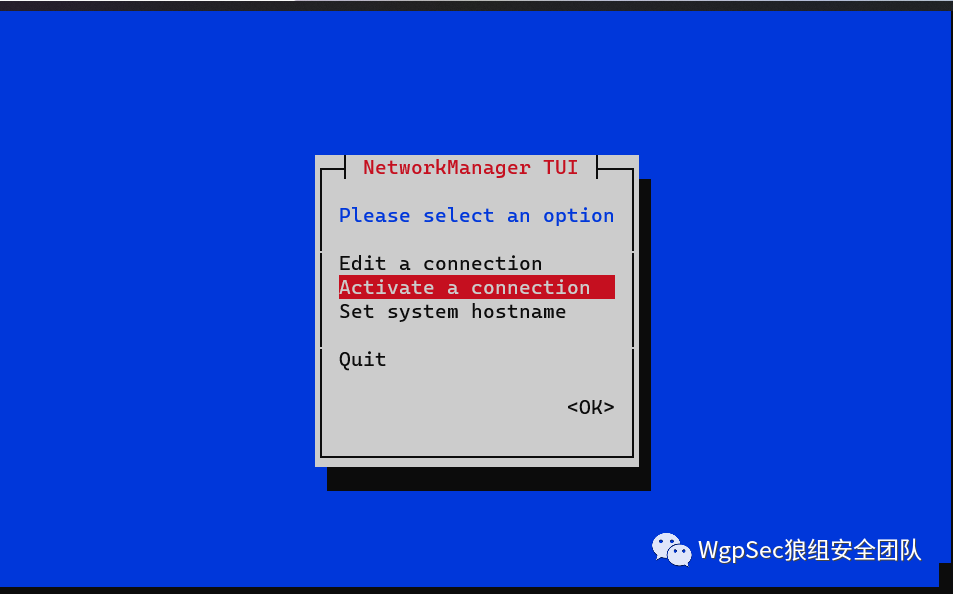 select the second option
select the second option 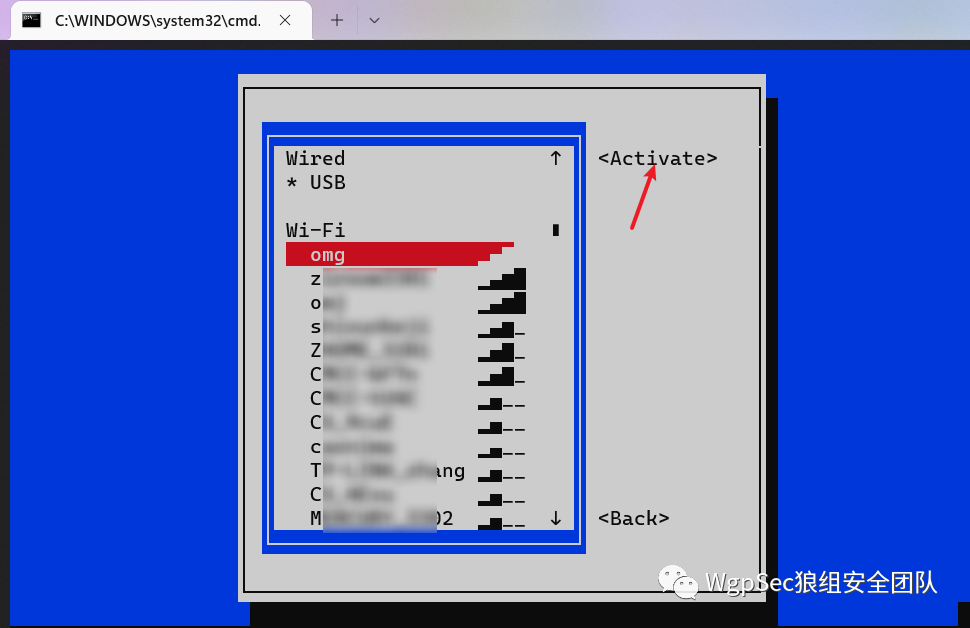 After entering, you can see your home Wi-Fi list, select the Wi-Fi and click
After entering, you can see your home Wi-Fi list, select the Wi-Fi and click Activate, enter the password and you can connect. After that, you will find that your computer also has internet access. 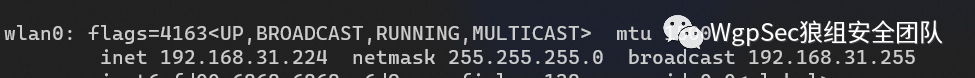 Now the remaining software can be messed around slowly, and those with ideas can also see if they can install some penetration software. This network card can be plugged directly into the现场的电脑, and you can operate remotely. Plus a data card, if it’s an esim, you don’t even need to insert your own card.
Now the remaining software can be messed around slowly, and those with ideas can also see if they can install some penetration software. This network card can be plugged directly into the现场的电脑, and you can operate remotely. Plus a data card, if it’s an esim, you don’t even need to insert your own card.
Postscript
So far, the road to messing with devices has just begun, but be aware that when installing software, pay attention to disk capacity, it only has 4GB. In the increasingly competitive red team, using such a low-cost network card can quickly penetrate on-site. Of course, it can do more than that. The current idea is to insert multiple operators’ 4G cards, and achieve anti-tracing dynamic stable proxy pool through router rotation, automatically capturing target machine data traffic packets, etc. I will update slowly when I have time. The tools mentioned in the text can be downloaded from PAN https://pan.wgpsec.org (click the original text to jump)
Reference Articles
“Flashing and Cracking Portable WiFi Entry Discussion” https://yanziblog.top/291/
“4G Portable Wi-Fi Flash OpenWRT to Become Soft Router” https://qust.me/post/msm8916/
“PostmarketOS Windows FAQ” https://wiki.postmarketos.org/wiki/Windows_FAQ
Author

Keac
A person who likes to do something.
Scan to follow the public account and reply to join the group
Discuss and study with masters~
Long
Press
Close
Note
WgpSec Wolf Group Security Team
WeChat ID: wgpsec
Twitter: @wgpsec