✅ Author Profile: A research enthusiast and Matlab simulation developer, continuously improving both mindset and technology.
For code acquisition, paper reproduction, and research simulation collaboration, pleasesend a private message.
🍎 Personal Homepage: Matlab King Assistant
🍊 Personal Motto: Walk every day, fear not the distance of ten thousand miles
🍊 Code Acquisition Method: QQ: 2307468664
🔥 Content Introduction
Information security has increasingly become a significant issue over the past few decades, leading to the emergence of various encryption algorithms based on algebraic methods or chaotic dynamics. This article explores a digital image encryption technology based on chaotic mapping, which primarily includes two major operations: pixel-level scrambling and bit-level masking and scrambling. Simulation results indicate that this encryption technology is effective and highly secure, but it also has the limitation of only being able to process images with equal numbers of pixels in both horizontal and vertical directions.
In recent years, with the widespread application of digital images in various fields, the issue of image security has become increasingly prominent. Traditional encryption algorithms, such as DES and AES, are inefficient when handling large image data and are vulnerable to known plaintext attacks or chosen ciphertext attacks. In contrast, chaotic mapping-based encryption algorithms have become a research hotspot in the field of image encryption due to their sensitivity to initial conditions and parameters, as well as their properties of ergodicity and pseudo-randomness. The sequences generated by chaotic systems exhibit pseudo-randomness, effectively achieving pixel-level and bit-level scrambling, thereby enhancing the security of the encryption algorithm.
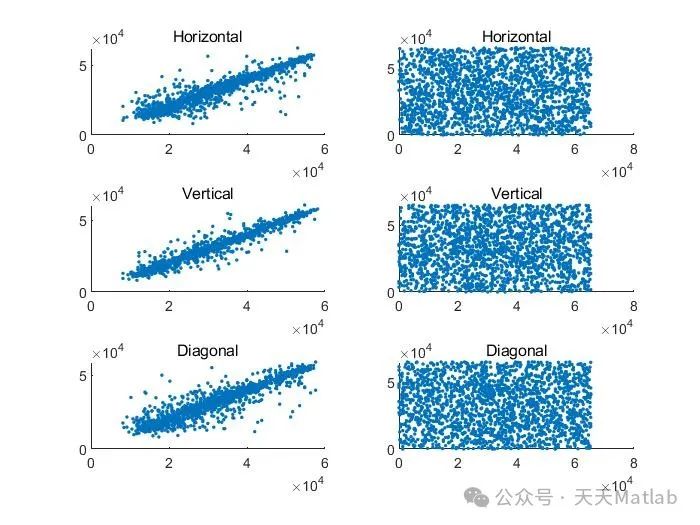
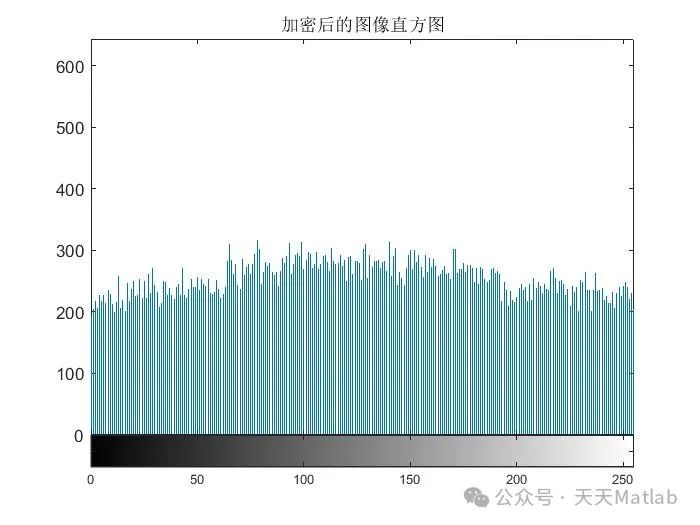
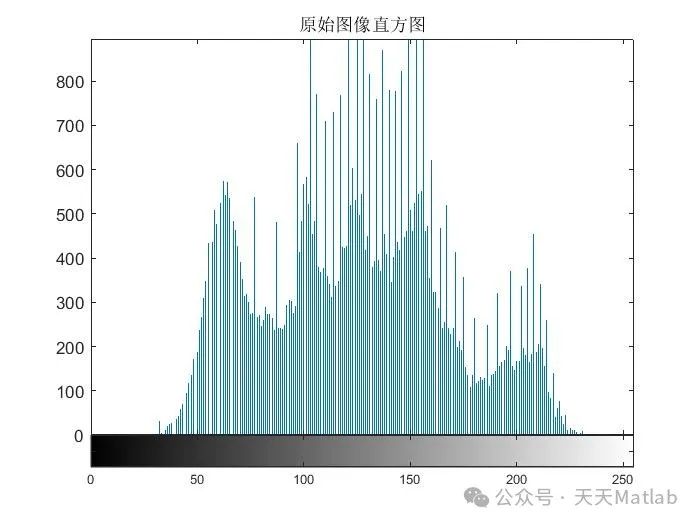
The encryption technology described in this article cleverly combines pixel-level scrambling and bit-level masking and scrambling operations, enhancing the complexity and attack resistance of the encryption algorithm. Pixel-level scrambling rearranges the image pixels through a certain chaotic mapping, disrupting the original spatial structure of the image. This scrambling operation can effectively resist statistical attacks, such as histogram analysis and correlation analysis. However, pure pixel-level scrambling may have certain security vulnerabilities, such as being susceptible to differential attacks. Therefore, the algorithm further introduces bit-level masking and scrambling operations to perform deeper processing on the image after pixel-level scrambling. The bit-level masking uses chaotic sequences to perform XOR operations on the binary representation of the image pixels, altering the bit values of the pixels and further obfuscating the image information. The subsequent bit-level scrambling then rearranges the bit sequences again using chaotic mapping, further enhancing the encryption effect and effectively countering more complex attack methods, such as known plaintext attacks and chosen ciphertext attacks.
MATLAB, as a powerful numerical computing software, facilitates the implementation of this encryption algorithm. By utilizing MATLAB’s image processing toolbox and chaotic mapping functions, pixel-level and bit-level operations can be easily implemented. The algorithm has been tested on the MATLAB platform, and experimental results show that it can effectively encrypt images of different sizes and demonstrate good encryption effects. However, the experiments also revealed a significant flaw in the algorithm: it can only process images with equal numbers of pixels in the horizontal and vertical directions. This limitation greatly restricts the applicability of the algorithm, making it unable to handle most images encountered in practical applications.
The limitations of this algorithm stem from its dependence on image size in its design. Both pixel-level scrambling and bit-level scrambling operations require specific partitioning and processing of the image, and if the numbers of horizontal and vertical pixels are not equal, these operations become complex and difficult to implement. This may be a compromise made during the algorithm design process to simplify calculations and improve efficiency. However, this compromise sacrifices the universality of the algorithm, preventing it from handling a wider range of image types.
Future research directions could focus on addressing the limitations of this algorithm. For example, more general pixel-level and bit-level scrambling methods could be studied to adapt to images of different sizes. Alternatively, adaptive image segmentation strategies could be considered to partition images of arbitrary sizes into multiple equal-sized sub-blocks for separate encryption processing, which are then reassembled. Additionally, other advanced encryption technologies, such as block encryption techniques or multi-key encryption techniques, could be combined to further enhance the security of the algorithm.
In summary, the digital image encryption technology based on chaotic mapping shows great application potential, but its development still faces many challenges. The encryption algorithm proposed in this article has achieved significant results in terms of security, but its limitations regarding image size have also been exposed. Further research is needed to improve the algorithm to achieve higher efficiency, better universality, and stronger security to better meet practical application needs. More in-depth research should focus on the security analysis of the algorithm, including the assessment of its resistance to various attack methods, as well as further optimization of the algorithm’s complexity and efficiency. Only in this way can such algorithms play their due role in practical applications, ensuring the security of digital images.
📣 Partial Code
function [correlation_coefficient]=hesap(x,y)
correlation_coefficient = corrcoef(x(:),y(:));
end
⛳️ Running Results


🔗 References
🎈 Some theoretical references are from online literature; if there is any infringement, please contact the author for deletion.
👇 Follow me to receive a wealth of Matlab e-books and mathematical modeling materials.
🎁 Private message for complete code and data acquisition, as well as customized paper modeling simulations.
Areas of Expertise:
🌈 Various intelligent optimization algorithm improvements and applications
Production scheduling, economic scheduling, assembly line scheduling, charging optimization, workshop scheduling, departure optimization, reservoir scheduling, 3D packing, logistics site selection, cargo position optimization, bus scheduling optimization, charging pile layout optimization, workshop layout optimization, container ship loading optimization, pump combination optimization, medical resource allocation optimization, facility layout optimization, visual domain base station and drone site selection optimization, knapsack problem, wind farm layout, time slot allocation optimization, optimal distributed generation unit allocation, multi-stage pipeline maintenance, factory-center-demand point three-level site selection problem, emergency supply distribution center site selection, base station site selection, road lamp post arrangement, hub node deployment, transmission line typhoon monitoring devices, container scheduling, unit optimization, investment portfolio optimization, cloud server combination optimization, antenna linear array distribution optimization, CVRP problem, VRPPD problem, multi-center VRP problem, multi-layer network VRP problem, multi-center multi-vehicle VRP problem, dynamic VRP problem, two-layer vehicle routing planning (2E-VRP), electric vehicle routing planning (EVRP), hybrid vehicle routing planning, mixed flow shop problem, order splitting scheduling problem, bus scheduling optimization problem, flight shuttle vehicle scheduling problem, site selection path planning problem, port scheduling, port bridge scheduling, parking space allocation, airport flight scheduling, leak source localization.
🌈 Machine learning and deep learning time series, regression, classification, clustering, and dimensionality reduction
2.1 BP time series, regression prediction, and classification
2.2 ENS voice neural network time series, regression prediction, and classification
2.3 SVM/CNN-SVM/LSSVM/RVM support vector machine series time series, regression prediction, and classification
2.4 CNN|TCN|GCN convolutional neural network series time series, regression prediction, and classification
2.5 ELM/KELM/RELM/DELM extreme learning machine series time series, regression prediction, and classification
2.6 GRU/Bi-GRU/CNN-GRU/CNN-BiGRU gated neural network time series, regression prediction, and classification
2.7 Elman recurrent neural network time series, regression prediction, and classification
2.8 LSTM/BiLSTM/CNN-LSTM/CNN-BiLSTM long short-term memory neural network series time series, regression prediction, and classification
2.9 RBF radial basis function neural network time series, regression prediction, and classification
2.10 DBN deep belief network time series, regression prediction, and classification
2.11 FNN fuzzy neural network time series, regression prediction
2.12 RF random forest time series, regression prediction, and classification
2.13 BLS broad learning system time series, regression prediction, and classification
2.14 PNN pulse neural network classification
2.15 Fuzzy wavelet neural network prediction and classification
2.16 Time series, regression prediction, and classification
2.17 Time series, regression prediction, and classification
2.18 XGBOOST ensemble learning time series, regression prediction, and classification
2.19 Transform various combinations time series, regression prediction, and classification
Directions cover wind power prediction, photovoltaic prediction, battery life prediction, radiation source identification, traffic flow prediction, load forecasting, stock price prediction, PM2.5 concentration prediction, battery health status prediction, electricity consumption prediction, water body optical parameter inversion, NLOS signal recognition, precise subway stop prediction, transformer fault diagnosis.
🌈 In the field of image processing
Image recognition, image segmentation, image detection, image hiding, image registration, image stitching, image fusion, image enhancement, image compressed sensing.
🌈 In the field of path planning
Traveling salesman problem (TSP), vehicle routing problem (VRP, MVRP, CVRP, VRPTW, etc.), UAV three-dimensional path planning, UAV collaboration, UAV formation, robot path planning, grid map path planning, multimodal transport problem, electric vehicle routing planning (EVRP), two-layer vehicle routing planning (2E-VRP), hybrid vehicle routing planning, ship trajectory planning, full path planning, warehouse patrol.
🌈 In the field of UAV applications
UAV path planning, UAV control, UAV formation, UAV collaboration, UAV task allocation, UAV secure communication trajectory online optimization, vehicle collaborative UAV path planning.
🌈 In the field of communication
Sensor deployment optimization, communication protocol optimization, routing optimization, target localization optimization, Dv-Hop localization optimization, Leach protocol optimization, WSN coverage optimization, multicast optimization, RSSI localization optimization, underwater communication, communication upload and download allocation.
🌈 In the field of signal processing
Signal recognition, signal encryption, signal denoising, signal enhancement, radar signal processing, signal watermark embedding and extraction, EMG signals, EEG signals, signal timing optimization, ECG signals, DOA estimation, encoding and decoding, variational mode decomposition, pipeline leakage, filters, digital signal processing + transmission + analysis + denoising, digital signal modulation, bit error rate, signal estimation, DTMF, signal detection.
🌈 In the field of power systems
Microgrid optimization, reactive power optimization, distribution network reconstruction, energy storage configuration, orderly charging, MPPT optimization, household electricity.
🌈 In the field of cellular automata
Traffic flow, crowd evacuation, virus spread, crystal growth, metal corrosion.
🌈 In the field of radar
Kalman filter tracking, trajectory association, trajectory fusion, SOC estimation, array optimization, NLOS recognition.
🌈 In the field of workshop scheduling
Zero-wait flow shop scheduling problem NWFSP, permutation flow shop scheduling problem PFSP, hybrid flow shop scheduling problem HFSP, zero idle flow shop scheduling problem NIFSP, distributed permutation flow shop scheduling problem DPFSP, blocking flow shop scheduling problem BFSP.
👇