Year: 2025
Multifocal Hepatic Steatosis
Multifocal hepatic steatosis (also known as multifocal nodular hepatic steatosis) is a rare condition characterized by multiple focal fat deposits in the liver, which can sometimes be confused with liver metastases. Epidemiology Risk Factors: Similar to other forms of hepatic steatosis, including: Diabetes Obesity Chronic excessive alcohol consumption Exogenous steroids Medications (such as amiodarone, methotrexate, … Read more
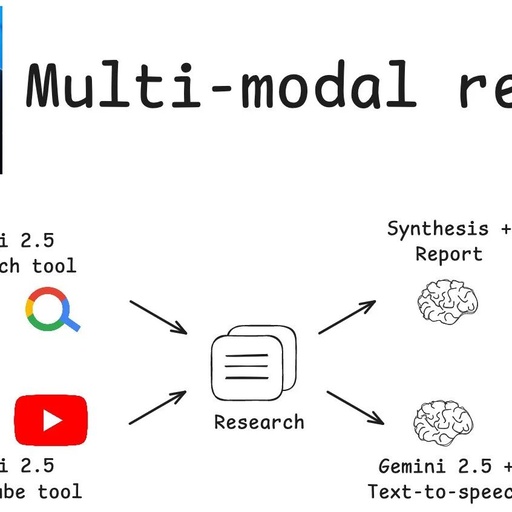
Empowering the Gemini 2.5 Model! Multi-Modal Researcher Enhances Research and Podcast Creation Efficiency
“Multi-Modal Researcher” is a simple yet efficient workflow for research and podcast generation that leverages the unique capabilities of the LangGraph and the Google Gemini 2.5 model family, integrating three practical features of this model family. Users can input a research topic and optionally provide a YouTube video link. The system then utilizes a search … Read more
WIX-multiPRO2 Dual Gel Prefabricated Gel Electrophoresis Tank #10111002
01 Product Introduction Brand: WIX Item Number: 10111002 Product Description: WIX-multiPRO2 Dual Gel Prefabricated Gel Electrophoresis Tank 02 Product Features Product Characteristics *1. Truly compatible with all domestic and international brands of prefabricated gels including BIO-RAD TGX, Thermo Invitrogen Nupage, and Thermo Invitrogen Novex. 2. Can accommodate 1-2 prefabricated gels, completing electrophoresis for 2 small … Read more
WIX-multiPRO4 Four-Slot Gel Prefabricated Gel Electrophoresis Tank #10111001
01 Product Introduction Brand: WIX Item Number: 10111001 Product Description: WIX-multiPRO4 Four-Slot Gel Prefabricated Gel Electrophoresis Tank 02 Product Features Product Characteristics *1. Truly compatible with all domestic and international brands of prefabricated gels including BIO-RAD TGX, Thermo Invitrogen Nupage, and Thermo Invitrogen Novex. 2. Can accommodate 1-4 prefabricated gels, completing up to 4 small … Read more
MeiGen-MultiTalk: Enabling Multi-Person Interactive Video Generation from a Single Photo
Reposted from Big Company Talk Recently, Meituan launched the audio-driven multi-person dialogue video generation framework MultiTalk, which has been open-sourced on GitHub. It introduces the innovative L-RoPE binding technology, which accurately addresses the challenges of multi-audio streams and character misalignment through label rotation positional encoding. This framework innovatively employs local parameter training and multi-task learning … Read more
Philips Multiva 1.5 Bed Disassembly Steps
Click the blue text above to follow us 1.Power off the device completely (LCC water cooling does not need to be turned off) before proceeding to ensure personal and equipment safety. 2.After the device is powered off, the bed board on the bed frame can be lifted down. 3.After lifting down the bed board, remove … Read more
MultiTalk: The Ultra-Realistic Digital Human for Group Conversations is Here! Essential for Karaoke, Covering Realistic Cartoon Animals, Easily Generate 15-Second Long Videos
❝ 🌹Hello everyone! Welcome toPoLang‘s homepage. Thank you for your support and encouragement. On the road of AIGC exploration, I willwalk with you. If you like it, pleasestar and follow PoLang or scan the code at the end of the article to join the discussion group! 1: Introduction to MultiTalk In previous articles, we introduced … Read more
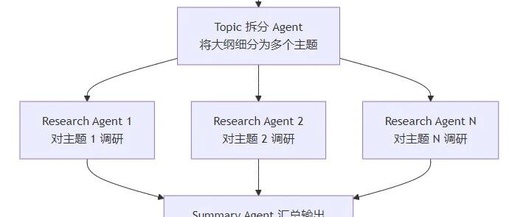
AgentPPT Laboratory: Practical MultiAgent PPT Implementation
Click the blue text to follow me for more AI insights~Paying tribute to the extraordinary, honoring the ordinary MultiAgentPPT is an intelligent presentation generation system that integrates A2A (Ask-to-Answer) + MCP (Multi-agent Control Protocol) + ADK (Agent Development Kit) architecture, supporting multi-agent collaboration and streaming concurrency mechanisms. https://github.com/johnson7788/MultiAgentPPT MultiAgentPPT A multi-agent system based on A2A … Read more
Multi-Voting Technique – A Structured Approach to Decision Making
Multi voting follows 3 steps (AVR): Multi voting follows 3 steps (AVR): Agenda – Clearly defining the purpose of voting, selecting the voters, orienting the procedure of voting Voting – Choice Selection, Sequencing, Categorization (based on Voter’s knowledge & Judgment) Result – Evaluation Structuring & Execution Agenda – Clearly defining the purpose of voting, selecting … Read more