Vehicle Network Security – UNR155 Regulations – Mitigation Measures for Vehicle Threats
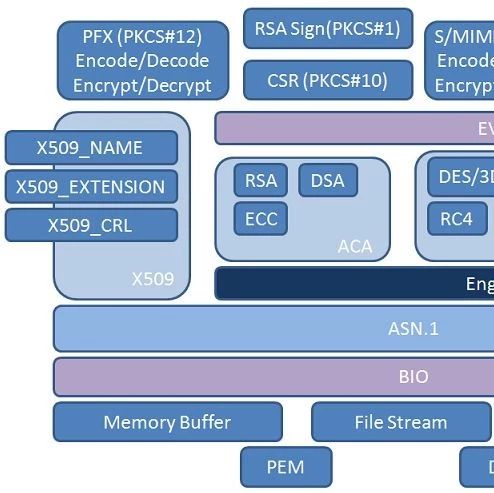
1. IntroductionThe UNR155 regulation document Appendix 5 consists of three parts.PART A introduces vulnerabilities, threats, and attack methods related to vehicles;PART B and PART C categorize the threats from PART A into internal and external threats,with PART B discussing mitigation measures for internal threats to vehicles;and PART C discussing mitigation measures for external threats to … Read more