Introduction to CAN Bus Basics for In-Vehicle Testing
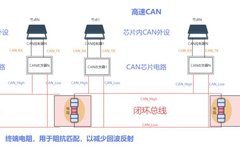
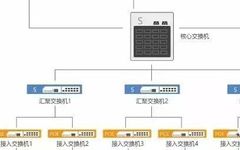
When learning about in-vehicle testing, how can we not understand CAN basics? Today, I have organized a detailed note for everyone, so let’s follow along with Songqin! Understanding CAN 01 What is CAN Bus? CAN stands for Controller Area Network, which is an internationally standardized serial communication protocol by ISO. In simple terms, the CAN … Read more