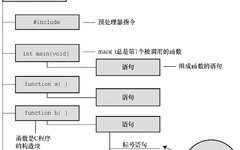
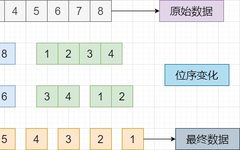
The Ideal Learning Path for C Language!
Programmers familiar with C often refer to it as the “wheel-making” language because it can do almost anything. Game company backend development, telecommunications backend development, server-side application optimization, backend system drivers, and kernels… In the eyes of programmers, C language is almost omnipotent. Of course, many people find C language difficult to start with, as … Read more